
The concept of tokenization isn’t new to real-world businesses. Physical tokens have been used as substituents for actual money from the beginning of the current currency system. Casino token is such an instance, inside casinos, real money exchanges for tokens at gaming tables. These tokens are valid only for inside transactions and outside of the casino. They are just pieces of plastics without any value. Later, this concept of tokenization had adopted in the digital world. With the invention of e-commerce, digital payment has gained popularity, and it became one of the fastest-growing payment methods. According to a Statista Research Department report, retail e-commerce sales have reached $3.53 trillion in 2019. They predict that revenue from e-commerce is expected to grow to $6.54 trillion in 2022. This growth of digital payment creates new types of security vulnerabilities to both businesses and customers. While millions of payment card details transfer between online stores and bank servers, cybercriminals might have an opportunity to snatch these valuable data. Digital tokenization has been introduced to ensure the security of digital transactions.
What is Tokenization?
Tokenization is converting sensitive payment card credentials such as payment card numbers into a non-sensitive unique code called a token. A token represents the original data, but there’s no way to retrieve original values from it. Because the token generating process does not use a mathematical algorithm like in encryption, the tokenized value of a 16-digit payment card number (1121 0500 0100 3567) can be a random number as 4521 2015 0255 3007. It’s impossible to find a meaningful relationship between the card number and the tokenized value. In fact, only token vaults are capable of the map and validate the tokenized value against the original payment card number. This mechanism serves to achieve the purpose of tokenization, which is the prevention of credit card fraud. Once the payment process starts, these tokens exchange inside payment networks instead of actual payment credentials. This prevents the exposure of sensitive information to unauthorized actors. In the case of a data breach, stolen tokens do not have any use for cybercriminals.
A tokenization server is a secure, centralized server where tokens are being generated, and token vaults store original payment credentials and tokenized values. Token Service Providers (TSP) are responsible for managing the token vaults. Two types of tokens are used for payment processing, namely High-value tokens (HVT) and Low-value tokens (LVT).
High-value tokens: act as surrogates for actual payment card numbers in payment processing, and the format is similar to the actual number. These tokens can be used to process a complete transaction. HVT can be tied to a specific device such as your smartphone, which may help track fraudulent transactions.
Low-value tokens: also act as surrogates for actual card numbers. But, payment processing is different from the HVT, and LVT cannot complete payment transactions by themselves. To continue the payment process, LVT must match back to the actual payment card number.
Tokenization can be used for different types of online payment transactions including,
- NFC digital wallets such as Apple Pay and Google Pay. For example, Apply Pay scans the payment card and send that details to the Token Service Provider through Apple servers. TSP then generates a token called Device Account Number (DAN) and sends it back to the device. Apple device saves this information in the secure element (SE) for future use.
- E-commerce sites that offer one-click checkouts. Each time customers purchase items from an online store, they have to enter card details, which isn’t an interesting experience. Instead of that, customers can store tokenized values of their payment cards securely on the online store for future use using tokenization. Next time, when they make a purchase, they could complete the transaction with a single click.
- Businesses that keep a customer’s card-on-file for subscription billing and recurring payments. Tokenization allows businesses to store their customers’ billing information securely and bill them periodically.
TrustCommerce, a software and financial technology company, was the first to introduce tokenization in 2001. It replaced cardholder data of their subscription-based merchants with billing ID.
How does tokenization work?
Tokens are generated by Token Service Providers (TSP) such as Mastercard and Visa. Imagine a customer wants to set up a digital wallet such as Google Pay by adding his payment card.
- The customer enters his payment credentials such as payment card number or primary account number (PAN), CVV code, and other required information.
- Digital wallets send this information to TSP and request a token.
- TSP requires verifying the customer’s card details with the account issuer or customer’s bank.
- After the bank’s approval, TSP generates a unique token by replacing the customer’s payment card number.
- The token sends back to the customer’s digital wallet.
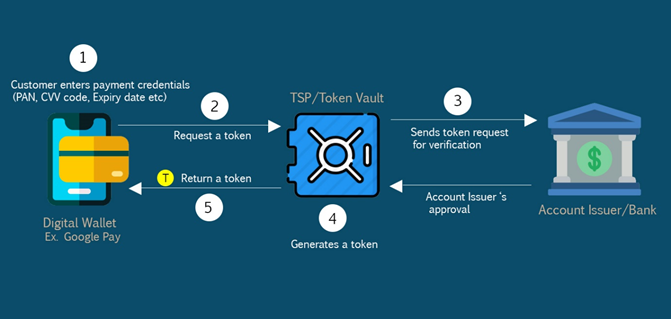
This token may be bound only to the customer’s device. Each time the customer makes a payment through the digital wallet, the transaction can proceed with this token instead of the customer’s actual card credentials. Let’s imagine the customer purchased an item and decide to pay using the digital wallet. First, the merchant sends the customer’s token to the TSP for authorization. Then TSP sends the token and payment card credentials to the account issuer or bank for authorization. The issuer allows or declines the transaction and sends its response back to the TSP. Next, the token and issuer’s response sends back to the merchant to complete the transaction.
Tokenization and Encryption
In the context of the payment card industry, tokenization and encryption are two different technologies used to achieve a common purpose, to secure the payment information. Both methods obfuscate sensitive data and make them unreadable to unauthorized parties. Though these concepts technologically different from each other, two terms are used interchangeably in the payment industry. Therefore, it’s important to make clear the differences between them.
Encryption
Encryption uses a mathematical algorithm and a secret key to convert the plain text data into a non-readable encrypted form. The more complex the algorithm, is more secure the data because attackers require more computing power to decipher the encrypted data. Encryption is reversible. Data can be decrypted with a decryption key. Both structured and unstructured data can be secured using encryption and obfuscated original data transfers between payment networks. Compared to tokenization, encryption allows encrypting large volumes of data.
Tokenization
Tokens generate randomly, and they act as a reference to the original sensitive data. These tokens share no sensible relationship with the original data. Tokenized values and original data have to store together to map and validate payment tokens during a payment process. Tokenized values are irreversible because tokenization doesn’t use any mathematical algorithm as in encryption. Only structured data such as payment card numbers or social security numbers can be used to generate tokens. Unlike in encryption, original data never transfers between payment networks. Not only payment credentials, but tokenization can also be used to secure other sensitive information such as social security numbers, medical information, passport numbers, driver’s license numbers, etc.


