From my previous post, I have discussed how we can protect corporate data on BYOD devices using Windows Information protection and deploying it through Intune app protection policies without enrolling devices. With few configurations, you can add Windows virtual desktop into this strategy and drive your corporate BYOD strategy with WIP, Intune, and WVD. Let us discuss the expected result, cost benefits, and how we can implement it from this post.
Refer to the previous posts on this subject:
01 - Understanding Microsoft Information Protection
02 - Windows Information Protection | Intune App Protection Without Enrolment | Step by Step
03 - Windows Information Protection | Intune App Protection Without Enrolment | User Experience (This Post)
Use of WIP with WVD in BYOD scenario
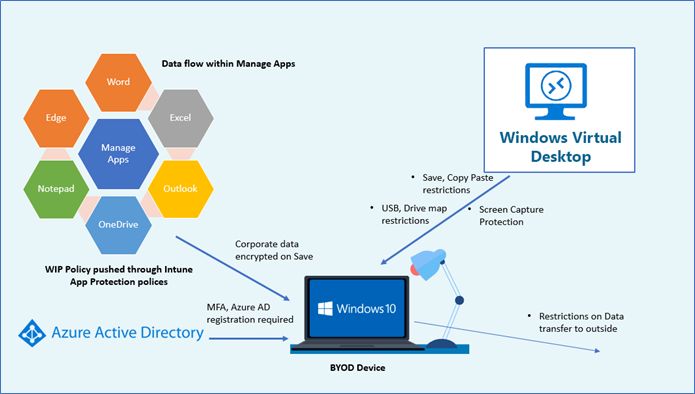
Below is the summary of the use case we can expect with WIP Intune app protection policies configured with Windows virtual desktop
- User can bring their own device to corporate use.
- Users can be anywhere. No VPN or any other connectivity is required to access corporate data.
- Intune App protection policy configured and expectation as below
- Corporate data are tagged from the domain name, save location, application with username, network location, etc.
- Corporate data are separated from personal and protected on unauthorized use.
- Corporate data can only be accessed from manage apps and cut, copy-paste, save only across manage apps.
- Data will be encrypted when saving in the local drive
- When sign in to manage the app, Azure AD registration is required with MFA
- WVD RD client is still not supported as an Intune enlighten app, so restrictions will not apply
- However, WVD itself capable of restricting file copy paste and clipboard functions. So, this can be enabled from the RDP settings of the WVD
- WVD connecting Client machine USB redirection and Drive redirection can be restricted via RDP settings.
Optimize resources for the WVD environment
With this approach, manage apps such as office apps are protected from unauthorized access. Which means corporate data sharing is blocked. So, you do not need to run these manage apps on the WVD VM. Instead, you can easily offload them to the end-user device. This will save resources in the WVD Host pools. For example, Teams uses close to 1GB of memory and 4GB of user profile disk space. Also, you do not need to worry about audio redirection—the same example for running Excel on a large scale.
WVD sizing recommendation - Virtual machine sizing | Microsoft Docs
Remote desktop workload identification - Remote Desktop workloads | Microsoft Docs
WIP and WVD Conflict
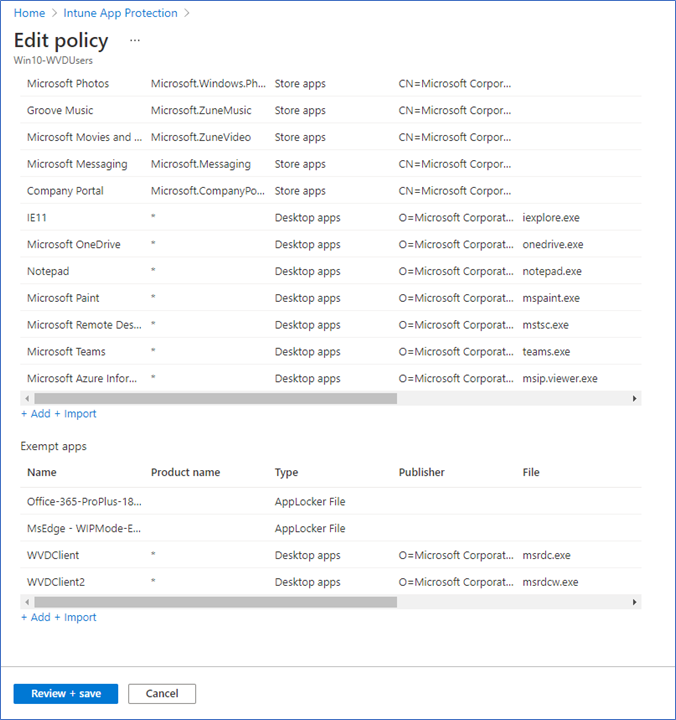
To prevent data sharing from manage apps and out of corporate locations, you need to select Block on the Windows information protection mode on your App protection policy asl below.
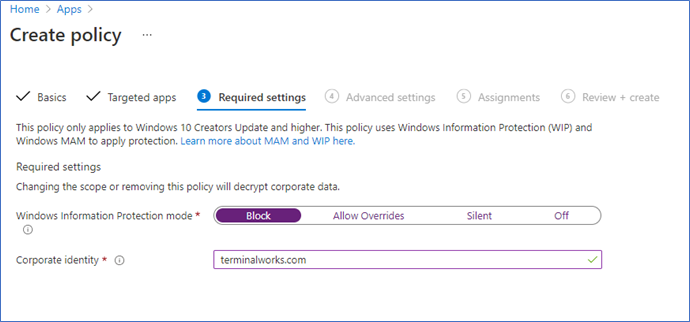
However, after applying the policy, it will block access to the WVD resources from the Remote desktop client with the following error.
Refresh unsuccessful. We need your sign-in information to refresh this feed. Click refresh to get started. Activity ID – xxxx.xxxx.xxx.xxx
This is because, as of this moment Remote desktop client is not an Intune enlighten app, and it will not be aware of the policy, and by default, it will block will. So you need to add exceptions to the RD client.
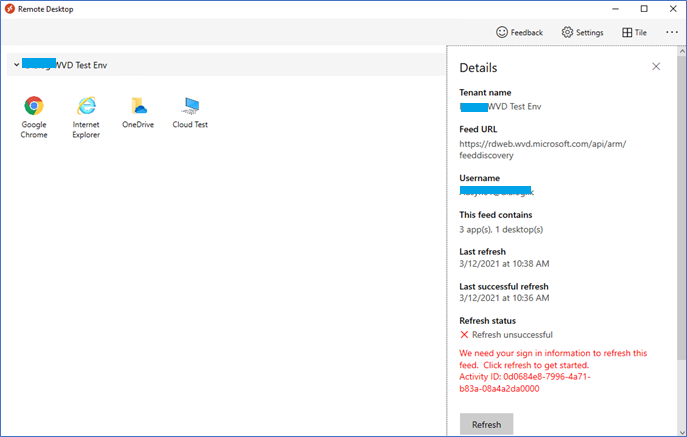
Configuring exceptions for WVD Remote Desktop Client
You need to add msrdcw.exe and msrdc.exe applications to the exception list of your Intune App protection policy. This will whitelist these two apps, which are required to access the WVD resources. As I mentioned before, from the WVD side, you need to configure the restrictions, so here you can give the policy exception.
Add below two entries to the exception list
Name – <Any Name>
Publisher - O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Product Name - *
File – msrdc.exe and msrdcw.exe
Min Version - *
Max Version - *
Action – Allow
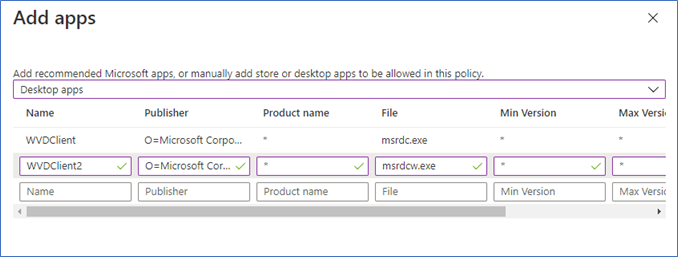
Next, you need to sync the policy and wait few minutes to apply the changes.
Now you can access the WVD feed from the Remote desktop client.
I hope this post is useful.
Cheers
Asitha De Silva







