
Passwords protect the sensitive data against unauthorized access and use to prove the identity of users before accessing the digital systems. The stronger the password, it’s less likely it to be cracked. A strong password comprises a combination of letters, numbers, and symbols. But, remembering the password and entering it each time logging in to a system is a painstaking task. Multi-factor authentication adds even more security layers to the authentication process. The passwordless authentication approach removes the passwords and provides more convenient ways to prove the identity of users.
The latest authentication updates in Azure Active Directory are now available for eliminating the use of passwords by users and their organizations and more friction-free ways of going passwordless with the introduction of the new Temporary Access Pass. Microsoft’s approach of goes passwordless aims to provide both convenient and high-security ways to avoid security breaches. They use three different passwordless methods to keep the user’s identity safe.
- Windows Hello for Business
- Microsoft Authenticator app
- FIDO2 security keys
With these methods, Microsoft aims to eliminate the use of passwords. There are few stages, and this approach, including developing passwordless methods, growing the partner ecosystem for devices and improving the admin experience. But the good news is that everything Azure AD users need to go passwordless is now available. It enables the much broader adoption of this technology with the Temporary Access Pass's next step.
Since many users widely use passwords, it’s challenging to stop using them overnight. But, over the past year, many people work remotely, and the use of passwordless methods has reached an inflection point. More than 200 million users are now using passwordless authentication across Azure AD and Microsoft consumer accounts. For users beyond these methods, Azure AD now supports FIDO2 security keys as an authentication method for signing into operating systems, applications, and services. Organizations can issue these keys to everyday information workers, and this approach can make life much easier for frontline workers using shared devices.
FIDO2 Security Key
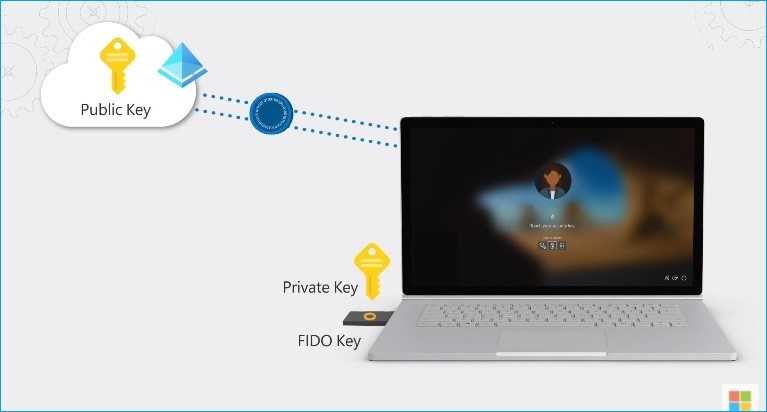
Image source: Microsoft Ignite - YouTube
This works by using industrial-strength public-private key technology. The FIDO device securely stores private keys that can unlock via a biometric or PIN. All authentication messages that exchange are signed by the private key and then validated by the public key, which stores in Azure AD. Which then sends a token or session cookie to the device as proof of authentication. This process happens within just a fraction of a second, and it feels instantaneous and convenient to the user.
Passwordless Adoption
For IT, Microsoft has made it easier to drive passwordless adoption. It includes how passwordless authentication methods launch in Azure AD. The management of passwordless can be automated using PowerShell or new Microsoft Graph APIs. It helps as you roll out new authentication methods and track their usage over time. You also can integrate these metrics with your apps using APIs.
Users who sign into different machines, phones, and cloud services using the authenticator app need to remember their email addresses and get verifications from the phone. They never need to remember or even type passwords. Though it’s easy and more secure than using passwords, it still uses two-factor authentication. When users do not have a phone or a dedicated Windows 10 device, they can use a FIDO security key. Microsoft has worked as part of the FIDO Alliance to develop a simple and common architecture for secure authentication with FIDO2.
Let’s see how this method can use to sign in to Windows 10. First, you have to insert the USB key into your device. Then on your profile on the screen, choose the sign-in options and select the security key method. It will ask you to touch the security key and uses your fingerprint to authenticate. Since Windows 10 supports seamless Single Sign-On (SSO) authentications, this session can forward to the browser too. If you go to myapps.microsoft.com, you will automatically sign in, and all your apps can see there. The Microsoft apps and SaaS apps such as Box that configured using Azure AD and Windows-based authentication can also be accessed. It again shows that you do not need to enter the password, and you can connect to your resources whether they are on-premise in the Microsoft cloud or other clouds and services.

As your PIN and biometric tie to the USB key, you can use it to sign in to services with other devices as well. For example, consider a computer configured to dual boot to Linux (Ubuntu) and running Chrome. In this case, when you try to sign in to myapps.microsoft.com, you can choose the sign-in options without even entering your email address. After selecting the security key option, you need to insert the USB key into the device and use your fingerprint for the authentication process. It will then show the accounts that registered with your key. Next, choose your account, and it will direct you to the same resources that support Azure AD-based authentication. Microsoft is expanding the Microsoft Intelligent Security Association (MISA) ecosystem of security partners, and these partners are developing a growing range of FIDO2 security keys. It includes support for the use of NFC reader devices for passwordless sign-in.
Improving the admin experience
Admin experience can improve by enabling the necessary experiences in the Azure AD portal. To do that, go to the security setting and then select the authentication methods. There you can see all of the new authentication methods include Microsoft Authenticator and the FIDO2 security key.
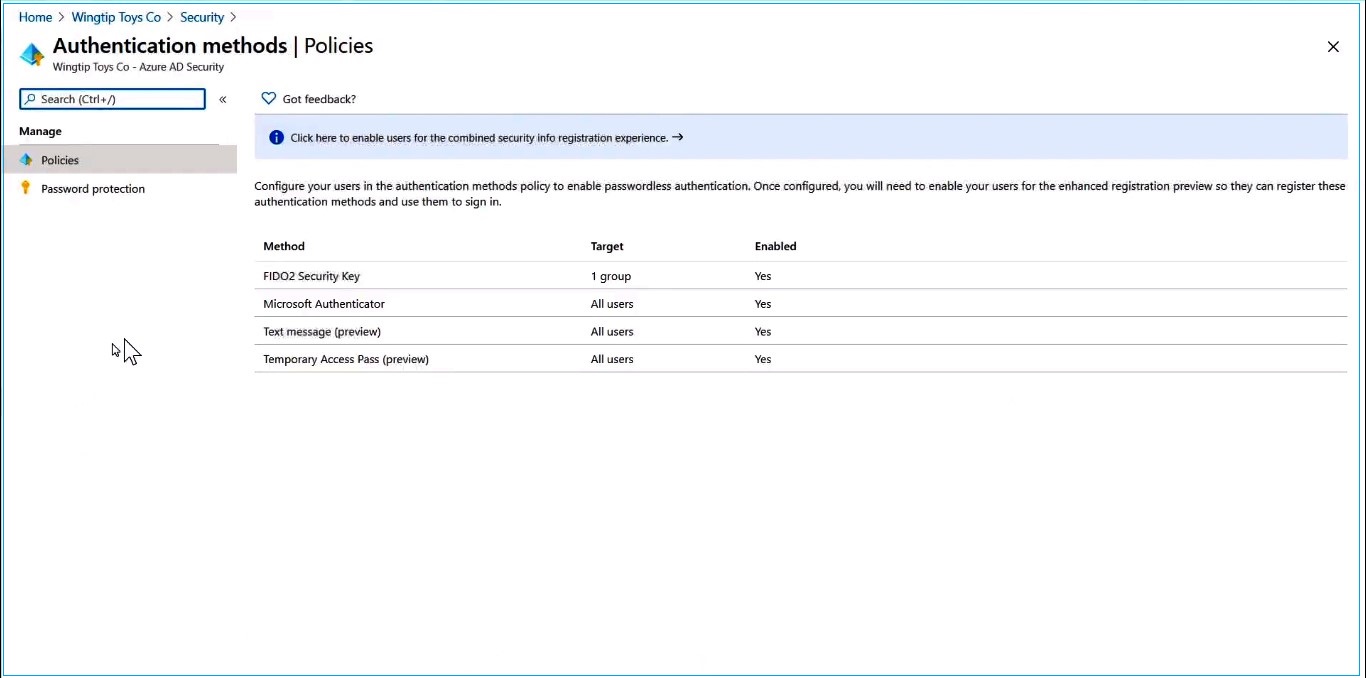
After choosing the FIDO2 security key, you can scope it to all users or limit the scope to selected users or groups. Imagine that you choose the ‘Select users’ option, and now you can add a new user. If you want, you could broaden the scope by adding multiple users and groups. After saving changes, new users are ready for FIDO2 authentication.
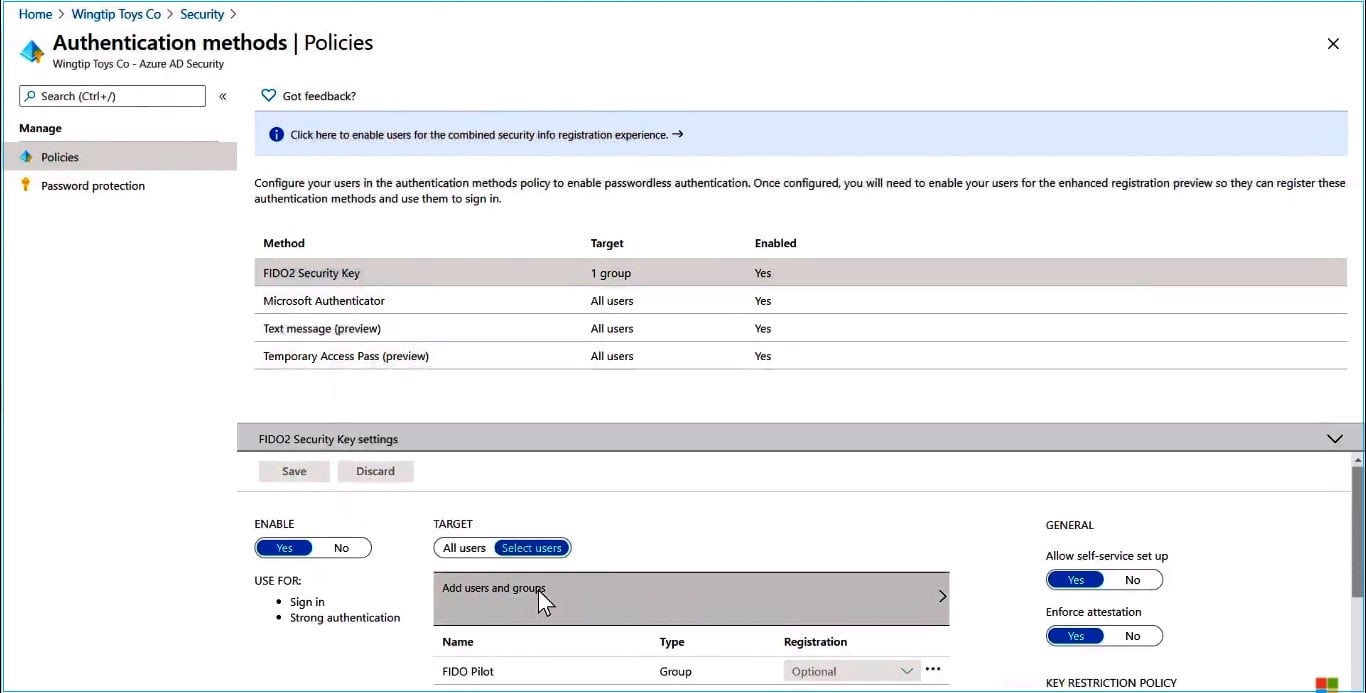
As a next step, a new user needs to register his key. To do that, he needs to sign in and navigate to the aka.ms/mysecurity.com and choose the ‘Add method’ option.
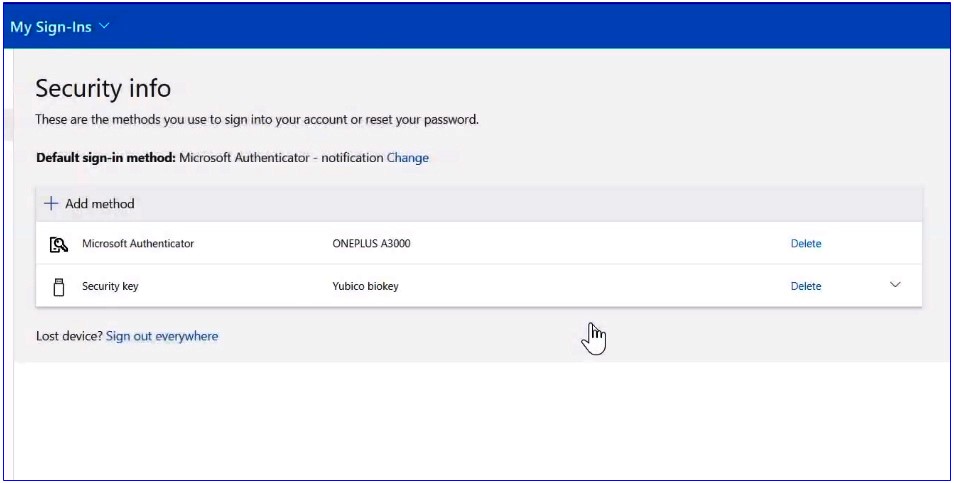
From the dropdown, the user needs to select a security key and add it.
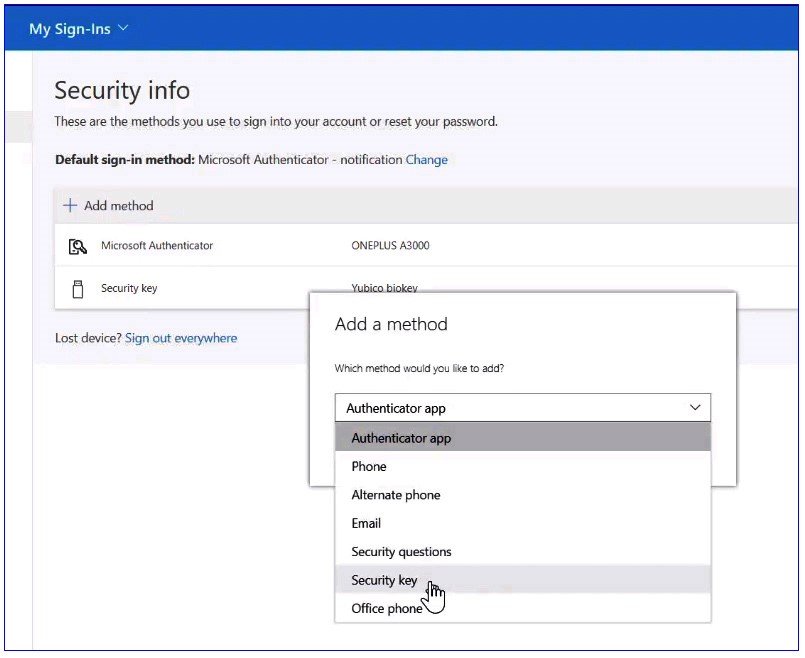
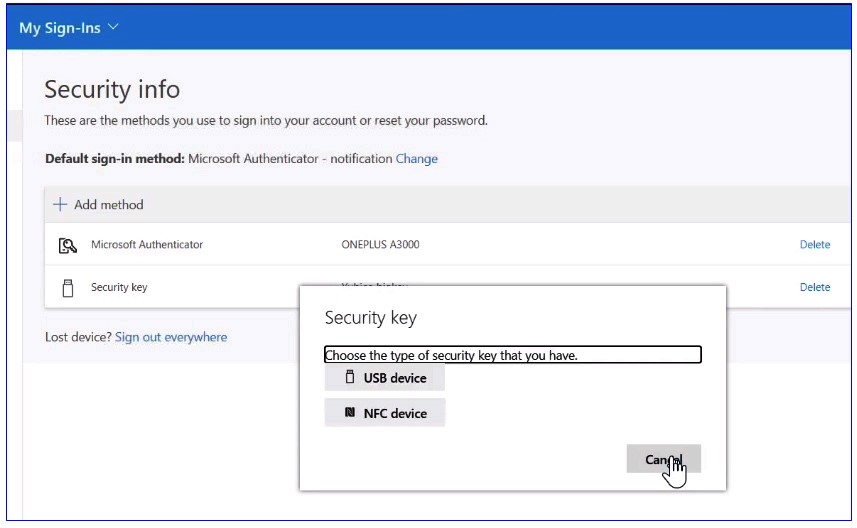
Next, the user can choose a USB or NFC device type. Let's say he chooses the USB and verifies the key to continue the setup.
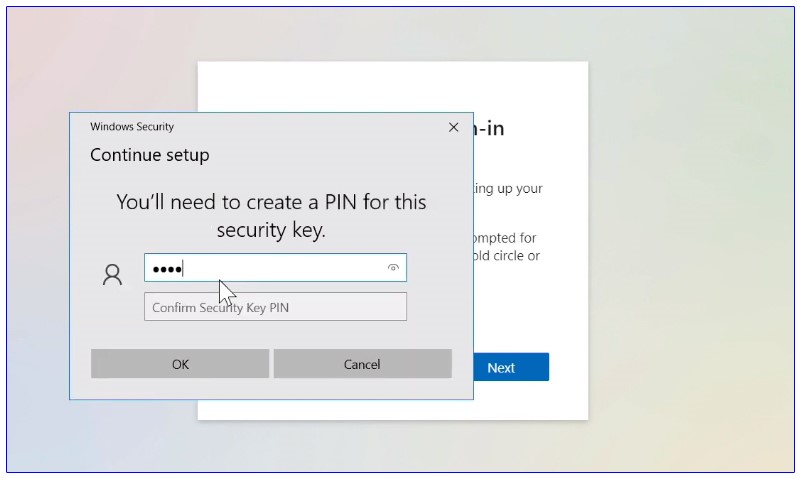
Then the user needs to set up a six-digit PIN and give a name to his security key that will help distinguish it from other keys.
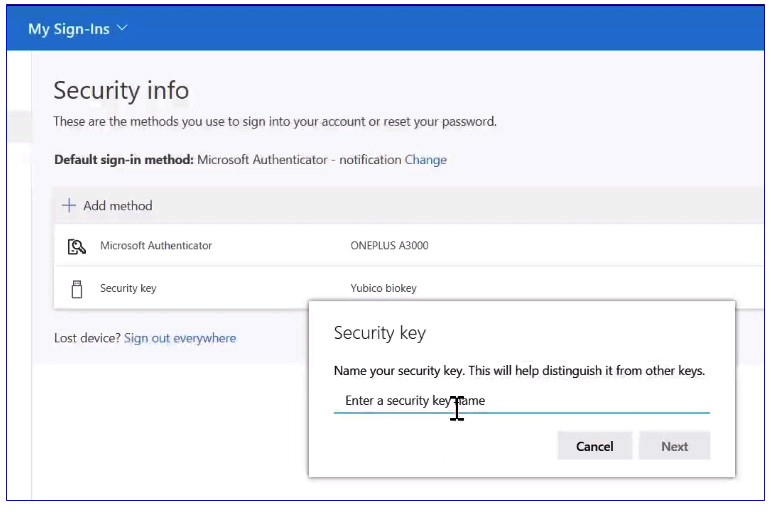
Now user's key is ready to use, and he can use this key to sign in to Azure AD joined PC or use it at the browser level on PC, Mac, or Linux.
Set up a Temporary Access Pass
If you already adopted MFA, you have all the pieces in place to enable passwordless authentication quickly. For new employees who do not have a password or MFA, that is where the new Temporary Access Pass comes in. For example, most organizations have a process to prove the user identity, and end of this process, an administrator can issue a temporary access pass to the verified user. This temporary access pass is a time-limited passcode that the user can apply to register their passwordless sign-in methods such as FIDO key or Microsoft authenticator app.
To do this, you need to go to the security settings and then the authentication methods. The Temporary Access Pass is configured as an authentication method. When you select it, you can see the same controls that you saw earlier. In this case, let’s set the scope for all users.
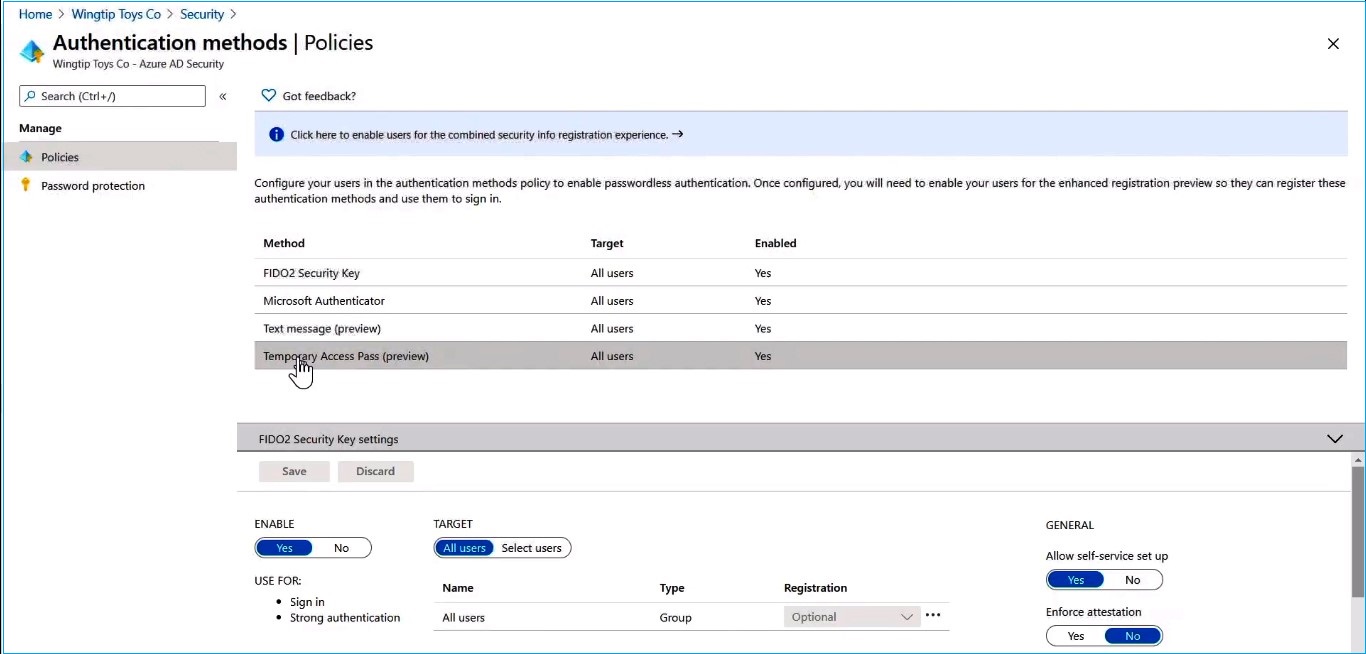
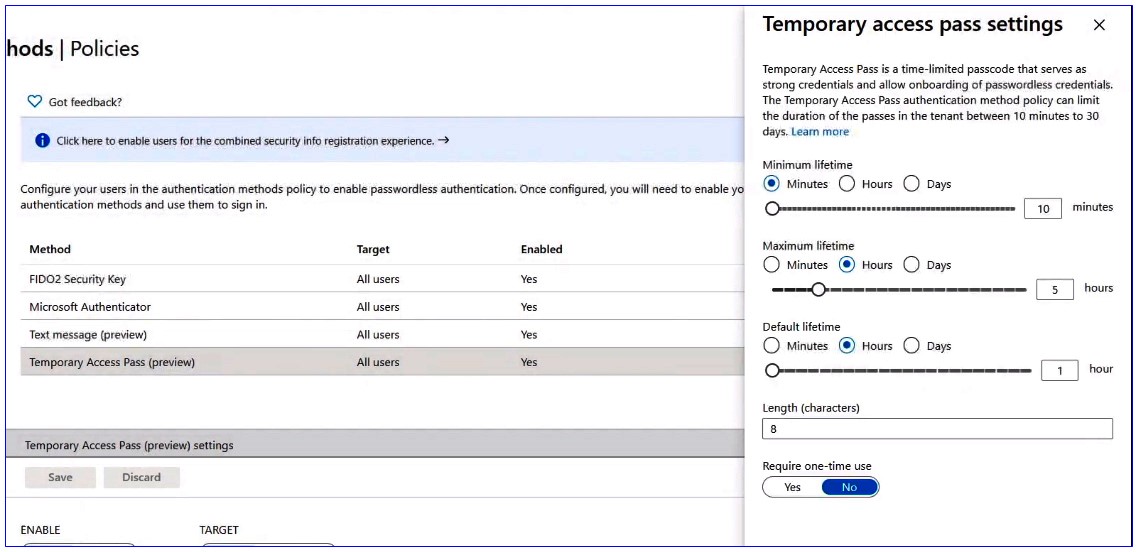
If you click into edit, you will see all the available settings. You can set the minimum and a maximum lifetime and a default lifetime. Then set the one-time use setting. You can select no if you need to use it more than once during that timeframe.
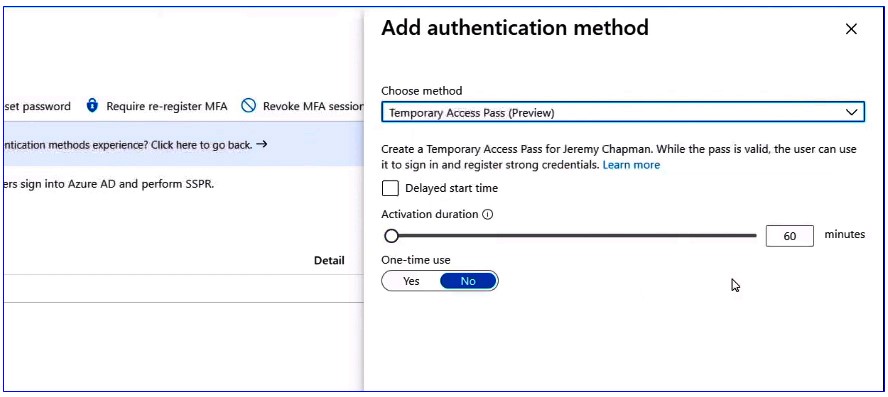
Next, to issue a Temporary Access Pass to a user in Azure AD, go to the user you want and then navigate authentication methods. Choose ‘Add authentication methods’ and then select Temporary Access Pass. You can either keep the default duration, which is 60 minutes or choose a duration that you want.
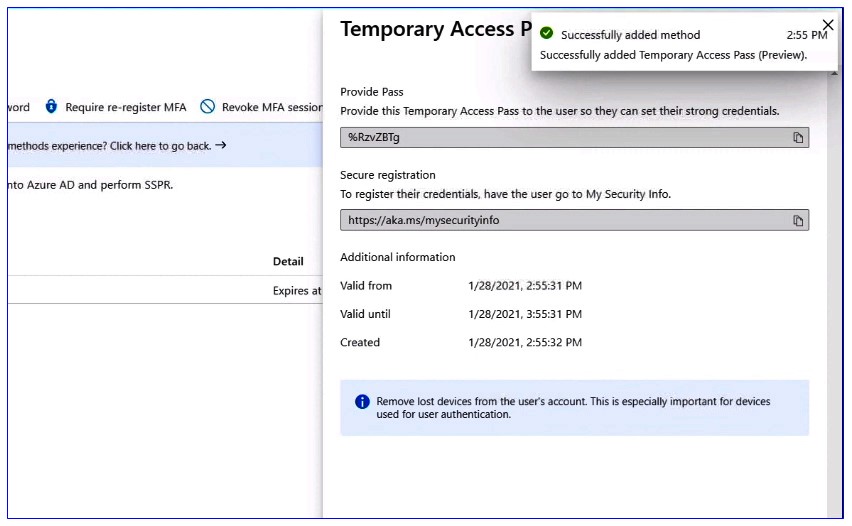
Then select add, and it will display the Temporary Access Pass that you can copy and send to the user.
This is just one way to do this, and there are some APIs for this. So you can integrate this process into your solutions.
I hope this post is useful.
Cheers
Asitha














