
What is Biometric Authentication?
Password-based authentication has provided protection for user accounts and devices for a long time. User credentials were sufficient to authenticate the legitimacy of the users. But, advancements in IT-related technologies challenge the safety of the user data and increase the vulnerability of data breaches. This leads IT companies to adopt innovative and secure user authentication methods to secure user accounts and devices. For instance, instead of passwords, big tech companies like Apple, Samsung, and Microsoft started to use the physical characteristics of users for authenticating their accounts and devices.
Users can use three methods to prove their identity: Using something the user knows (username & password, personal identification number), using something the user has (security token, smart card), and using something the user is (Biometrics -fingerprints, voice, facial, iris). Among them, the use of biometrics offers users a more secure and easy mode of authentication.
In general, biometrics are referred to as body measurements and calculations related to human characteristics. Biometric authentication verifies the user identity based on physiological and behavioural characteristics of individuals such as fingerprints, face, voice, retinal patterns, iris of the eye, etc. Biometric authentication systems store these biometric data in template databases and extract them to compare whenever users request to access their accounts or devices. For instance, in a fingerprint recognition system, sensors scan the user’s fingerprint, produce its digital representation, and store it in a database. When a user tries to log in, the system again scans the user’s fingerprint and matches it against the stored templates.
Not only user accounts and devices but biometric solutions can also be used for building access control to stop unauthorized entry. Compared to traditional authentication methods, biometric solutions are more reliable because biometric traits cannot be easily shared, lost, or duplicated, and the user needs to be present during the authentication process. Gartner, a research and consulting firm, emphasized that “Biometric authentication does not depend on the secrecy of biometric traits, but instead relies on the difficulty of impersonating the living person presenting the trait to a device.” Therefore, systems that are protected with biometric solutions are more secure from cyber-attacks.
There are two types of biometrics: physiological biometrics and behavioural biometrics.
Physiological biometrics
Physiological biometrics consists of two parts, namely morphological and biological.
Morphological biometrics includes fingerprints, iris, retina, face shape, and veins. Biological biometrics involves genetic and molecular traits such as DNA and blood.
Behavioural biometrics
Behavioural biometrics consists of the behavioural characteristics of a person, such as voice, gestures, keystrokes, signature dynamics, and gait. These behaviours are unique to each individual.
To minimize the risks and difficulties associated with password-based authentication, new authentication methods such as Single Sign-on (SSO), Two-Factor Authentication (2FA), Multi-Factor Authentication (MFA), Token-based Authentication, and Smart Card Authentication has introduced. But, compared to them, biometric solutions consider the most foolproof method. It’s important to note that, during the identification process, it’s not required to be 100% identical to the input biometric sample with stored templates but has to be nearly identical because the physical and behavioural traits of humans never remain unchanged over time. This may open up new security risks in biometric-based authentication, for instance, modern AI algorithms are able to generate fingerprints which can deceive the fingerprint scanners during the identification process.
Types of Biometric Authentication
These are some of the most popular biometric authentication methods available today.
Fingerprint recognition
Initially, Fingerprint recognition was used by law enforcement agencies to identify criminals. Since then, it has come a long way to modern-day sophisticated fingerprint scanners, and now it’s one of the most popular biometric authentication methods. Particularly mobile devices widely use this technology to verify the user identity. Tiny ridges and valleys in the finger create fingerprints that are unique to each individual. Fingerprint scanners capture the digital image of that fingerprints and match it against the stored fingerprint templates. Three types of fingerprint scanners are available in the market; optical scanners, capacitive scanners, and ultrasonic scanners. Fingerprint recognition is relatively cheap authentication technology.
Facial recognition
The use of facial recognition in digital security systems is very common in Sci-fi movies. But it’s not just a feature of science fiction anymore. Facial recognition systems use the distinctive features of the human face to authenticate the users. The facial features used for identification include nose structure, the distance between the eyes, the shape of cheekbones, the depth of eye sockets, and the contour of the lips, ears, and chin. There are four basic steps involved in facial recognition solutions; face detection, capturing the face and analysis, converting the image to data, and finding a match. Facial recognition is a touchless solution, and now it’s widely used to unlock the devices such as mobile phones, tablets, and laptops.
Iris recognition
Iris recognition is considered to be one of the most accurate and fast biometric authentication methods. Iris recognition uses unique patterns in an individual’s iris for identification. These patterns remain unchanged throughout the life of individuals. The Iris scanner captures the detailed structure of the iris using invisible infrared light. After that, it detects the iris and removes unnecessary details such as eyelids and eyelashes. Then the iris part is divided into small blocks and converted into mathematical data. This data will be compared with the stored templates in the database for identification. Similar to facial recognition, iris recognition uses touchless technology. Researchers have found that there’s a possibility to deceive an iris scanner using a high-resolution photograph of an individual’s eye.
Voice recognition
The length and tension of an individual’s vocal cords create voice prints that are unique to each individual. This uniqueness of the individual’s voices can be used to create a robust biometric authentication method. The advancement of neural network technologies has enabled the development of this method. There are two types of voice authentication methods; Text-independent recognition and Text-dependent recognition. Analysis of different vocal qualities such as tone, pitch, and frequency are used to identify the users. Voice recognition solutions are perfect for secure authentication over the phone. But, it may be not work properly in a noisy environment or if the user has severe respiratory illnesses.
Vein recognition
Vein recognition or vein matching is a highly accurate biometric authentication method that uses the patterns of veins in the palm or finger. These patterns are unique to each individual and even vary among identical twins. This method is more secure than fingerprint recognition because it uses unique patterns of blood vessels inside the skin, which are impossible to forge. Vein patterns can be captured using near-infrared light. When this infrared light infiltrates the finger or palm, the haemoglobin in the blood vessels absorbs the light and makes the veins visible as a pattern of line. These vein patterns are recorded as an image using a camera and digitised as an image. Then, this data is verified against the stored images in the database. The vein recognition method has a close to zero rejection and false acceptance rate making it a highly accurate biometric solution.
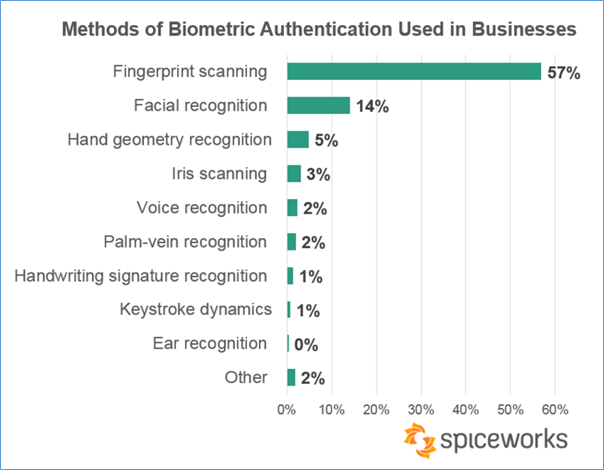
Use cases of Biometric Authentication
The importance of biometric authentication has been proven across many industries. The below use cases show how industries adopt this technology to secure their systems.
Healthcare
The Healthcare sector uses biometric authentication mainly for patient matching and patient and employee identification. Many healthcare facilities use biometric solutions such as facial, iris, fingerprint, and vein recognition to identify their patients in order to access their confidential medical records. These types of trusted authentication methods allow hospitals to give the right medication to the right patient. It also helps to prevent cybercrimes related to medical data.
Banking and Financial services
Traditional authentication methods such as passwords, PINs, and digital signatures, don’t provide adequate security for sensitive customer information such as credit cards and bank account details. It has increased the risk of financial fraud and cyber-attacks more than ever. These risk factors convinced banks and financial institutions to adopt biometric solutions to authenticate customers when accessing their services. It also helps to stop internal financial fraud committed by employees. Mobile banking apps use the fingerprint method to authenticate the transactions such as money transfers and online payments. Biometric solutions provide flexible, secure, and low-cost authentication methods for banks and FinTech companies.
Travel and Hospitality
The travel industry has increased the efficiency of its services by adopting biometric authentication for access control. Facial recognition is widely used in airports and airlines to identify passengers. For instance, some airlines allow their customers to check in to flights using facial recognition. Biometric authentication is also reshaping the hospitality industry. Hotels use biometric solutions such as facial recognition and fingerprint scanning to check in to the rooms. Furthermore, hotels can use these methods to manage guest access areas.
Law enforcement
Law enforcement agencies have been using fingerprint identification to recognize criminals for a long time. Now, biometric technologies are taking the use of human characteristics in criminal investigations to the next level. Law enforcement agencies widely use biometric solutions such as facial recognition, fingerprints, and DNA. Now law enforcement officers can scan the fingerprints of suspects at the crime scene and verify them against the remote database. Not only fingerprint scanning, but the FBI has also developed a program called Next Generation Identification (NGI) based on facial recognition and iris recognition.
Hope this post is useful


