
What is confidential computing?
It is important to understand today's security flux and transformation. As smart attackers conduct their attacks across silos and perimeters, security tools are becoming more complex and poorly integrated into DevOps cycles, and separating the signals from the noise is difficult. Azure Cloud Security addresses these issues. Microsoft currently has over 650,000 Azure Cloud customers and over 8,500 security experts. Microsoft 365 Defender blocked 9 billion malware threats on endpoints in 2020, and Microsoft processes over 24 trillion signals every 24 hours. This shows that Azure Cloud is regarded as a secure and dependable solution. However, there is still space for improvement in terms of security.
Customers' trust is difficult to gain these days, and they want full control over the data lifecycle. Privacy, trust, untrusted collaboration, and evolving regulations and compliance in the European Union and around the world are driving this trend. Untrusted collaboration is a new scenario enabled by confidential computing.
The current state of the data protection lifecycle
It is possible to protect data at rest and data in transit using existing encryption technologies. If you enable BitLocker, for example, no one can access the files on your laptop. Similarly, when your data stays at rest in the Cloud, it is encrypted with your unique key. Secure file transfer methods such as HTTPS and TLS can be used for file transfer. Similarly, you can encrypt data while it is transported in the Cloud.
Customers' Cloud, on the other hand, operates in a broader context. For example, data center admins have access to the data. The client runs on a guest operating system, and their Cloud runs in a broader context with a hypervisor or a host operating system managing the instances. Though Azure Cloud provides security, users frequently request that the Cloud's security capabilities be expanded. Confidential computing covers gaps in the data security lifecycle by protecting data in use, while in RAM, and during computation. Confidential computing allows customers to control their data throughout the data lifecycle. It protects against malicious insiders, hackers, and emerging scenarios such as multi-party confidentiality. In Azure, confidential computing requires an independent hardware root of trust, verifiable attestation, and memory encryption capabilities.

Confidential computing is defined by the Confidential Computing Consortium as the protection of data in use by performing the computation in a hardware-based Trusted Execution Environment (TEE). It ensures verified data integrity, code integrity, and data confidentiality.
Confidential Computing in Azure
Azure confidential computing has distinct capabilities that can assist you in achieving the highest level of data privacy.
Hardware Root of Trust (RoT): Azure confidential computing believes in an independent hardware Root of Trust that’s rooted down to AMD, Intel or Nvidia.
Attestation: Azure confidential computing includes attestation capabilities, which allow you to ensure that your environment is as you expect it to be. The attestation service itself operates in a confidential environment.
Confidential Keys: Microsoft took Azure Key Vault and created an Azure Managed HSM (Hardware Security Module), which runs in a confidential environment. It provides Secure Key Release (SKR) capabilities, ensuring that your keys are only clear inside the enclave and encrypted outside.
Confidential IP Services: Azure provides a slew of confidential PaaS/SaaS services.
It is virtual machines, containers, and services that enable confidential computing. There are various virtual machine sizes, including DCA/ECA VMs on AMD, DCsv2/DCsv3/DCdsv3 VMs on Intel SGX, and Nvidia VMs in limited preview. As the world shifts to Cloud Native computing and containerization, Microsoft offers options for protecting your containers with confidential VM worker nodes managed by AKS and serverless containers with confidential containers on ACI.
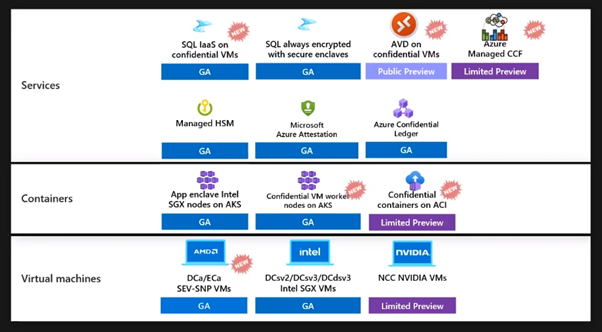
Microsoft has introduced new services such as Azure Confidential Ledger, which provides tamper-proof audit logs. It is now possible to run your SQL IaaS installation on confidential VMs. SQL is always encrypted with secure enclaves, and now there is a public preview of Azure Virtual Desktop (AVD) on confidential VMs, and a limited preview of Azure Managed CCF.
Spectrum of confidential computing
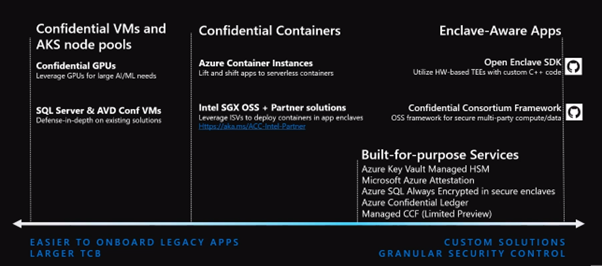
On the right, you can see Enclave Aware applications that can be created using the Open Enclave SDK, the Confidential Consortium Framework, and a variety of other publicly available SDKs. You will have full control over the lines of code that run inside the enclave, and you will be able to use purpose-built services.
In the middle, you can see confidential containers, and you can lift and shift them in a confidential environment. You don't have to change a single line of code here.
On the left, you have confidential VMs and AKS node pools that make available through confidential GPUs and SQL Server & Azure Virtual Desktop confidential VMs.
CPU Trusted Execution Environments (TEEs) in Azure
On CPUs, Azure has various Trusted Execution Environments (TEEs). Azure is unique in that it provides a wide range of capabilities. It includes AMD confidential VMs, allowing you to lift and shift into a confidential environment. As a result, you get two levels of encryption. You can encrypt the memory while it is in RAM and pre-encrypt your operating system disk. Within Azure, the operating system can be pre-encrypted, and there are multiple key management options for OS disk encryption, including customer-managed keys and assistant-managed keys.
You can obtain VMs with app enclaves using Intel SGX (Software Guard Extensions). It enables you to divide your app into untrusted and trusted regions, with sensitive code placed in the trusted environment. Encryption of VM memory in RAM and app-specific Enclave Protected Cache (EPC) memory are available here. It includes capabilities such as TME-MK, which encrypts the entire VM memory, and EPC memory, which allows you to run trusted code. It also has a robust ISV and Open Source Software (OSS) ecosystem, allowing you to deploy existing containers without requiring any code changes.
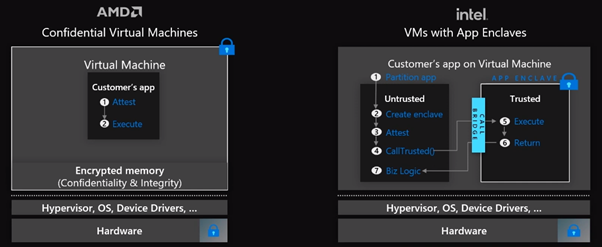
App Enclaves with Intel SGX
Azure is the first Cloud provider to provide a virtualized environment for Intel SGX, allowing you to achieve the highest levels of data privacy while maintaining control over every single line of code. These can be found in DCsv2 and DCsv3 applications that use Intel SGX and TME-MK memory encryption. The most recent DCsv3 VMs are powered by 3rd generation Intel Xeon Scalable confidential processors. In comparison to previous generations, Microsoft has increased EPC memory (1500x) to 256 GB. Signal Messenger and Fireblocks are two applications that use Intel SGX TEEs on DCsv2/DCsv3 VMs.
Confidential VMs with AMD SEV-SNP
In SEV-SNP, the SNP element is important because it provides integrity protection. You can make your applications confidential using AMD SEV-SNP without changing any code. These are now accessible via DCasv5 and ECasv5 VMs. Memory encryption is possible with CPU-protected keys, and full OS disk encryption is possible with keys sealed in vTPM. It also has guest attestation capabilities, which can be used with 3rd Generation AMD EPYC Milan processors equipped with SEV-SNP technology. F5, HashiCorp, and BMW Group are three applications that use the SEV-SNP environment on ECasv5/DCasv5 VMs.
New confidential VM features and integrations
Guest attestation
Guest attestation is a key capability that is now available. You can run confidential VMs on a hardware-based Trusted Execution Environment (TEE), which provides security features such as isolation, integrity, and secure boot. It enables you to make application deployment decisions based on a desired good state. It enables the use of remote attestation artefacts (tokens and claims) received from another system to allow relying parties to gain trust in order to conduct transactions with the other system.
Confidential VM node pools on AKS
You can get data using encryption for your AKS agent node pools here. This allows for seamless Linux deployments on AMD SEV-SNP-protected nodes. You can achieve full AKS parity and enable remote guest attestation to verify your deployments on provisioned nodes.
Azure Confidential GPU VMs
Azure Confidential GPU VMs are now in limited preview, ensuring that your data and code remain confidential in both GPU and CPU environments. These are ideal for maintaining the confidentiality and integrity of AI workloads in use. These are also ideal for securing ML and large data AI workloads. Microsoft collaborates with Nvidia, and a limited preview is available on Nvidia A100 Tensor Core GPUs.
Confidential Serverless ACI Containers
You can make your containers confidential without changing any source code and deploy them in a serverless environment using confidential Azure Container Instances (ACI). This ensures full attestation by using platform-integrated tools to measure all in-use components. These are ideal for confidential ML, AI, and short-lived burstable workloads. You will receive dedicated hypervisor and hardware-derived in-memory encryption per entire container without changing the code for your containers.
Confidential VM option for SQL Server on Azure VMs
This feature allows you to run a full SQL Server installation on a confidential VM. VMs have additional protection for data in use. You can add defence-in-depth to your existing SQL Server security features and get remote attestation at boot. These are ideal for all types of lift and shift workloads.
Azure Virtual Desktop (AVD) on Confidential VMs
This allows for a complete Windows 11 desktop and application experience in a confidential environment. With Windows Hello and Windows 11 multi-session capabilities, you can gain secure remote access. You can also use this capability to autoscale confidential VMs as demand changes. With a virtualized environment, you get the benefits of the Cloud while operating in a confidential environment.
Azure Managed Confidential Consortium Framework (CCF)
This enables you to develop confidential stateful services faster. It reduces reliance on compute nodes and specialized labour compared to traditional Digital Ledger Technologies (DLT). In addition, the method allows for the deployment of CCF-aware applications over a verifiable confidential network. The consortium-style governance model allows programmable confidentiality between multiple parties operating in confidential compute infrastructure.
Use cases by industry
There are several use cases in industries such as retail and advertising, financial services and healthcare.
Retail and advertising
- Cleanroom and multi-party AI/ML analysis
- Targeted offers
- Untrusted collaboration
- Marketing and micro-targeting with responsible AI principles
- Retail edge confidentiality
Financial services
- Anti-money laundering
- Secure payment processing including credit card and bank transactions
- Fraud prevention
- Credit risk assessment and qualification from combined bank records
- Digital currencies
Healthcare
- Disease diagnostic
- Insurance fraud prevention
- Contact tracing
- Drug development
- Records and evidence management
Reference:
Microsoft Ignite Sessions





