Azure AD joined VMs for AVD is a big breakthrough in the AVD world, not only that, but recently Microsoft has announced General Availability of Azure Files integration with Azure Active Directory (Azure AD) Kerberos for hybrid identities. With these releases, identities in Azure AD can mount and access Azure file shares without the need for a line-of-sight to an Active Directory domain controller.
Until now, Azure Files supported identity-based authentication over Server Message Block (SMB) through two types of Domain Services: on-premises Active Directory Domain Services (AD DS) and Azure Active Directory Domain Services (Azure AD DS). On-premises AD DS requires clients to have line-of-sight to the domain controller, while Azure AD DS requires deploying domain services onto Azure AD and domain joining to Azure AD DS. Azure AD Kerberos is a new addition to these identity-based authentication methods. Azure AD Kerberos allows Azure AD to issue Kerberos service tickets over HTTPS for service applications in Azure AD. This removes the need to set up and manage another domain service, while also removing the line-of-sight requirement to the domain controller when authenticating with Azure Files. For this experience, the clients connecting to Azure Files need to be Azure AD-joined clients (or hybrid Azure AD-joined), and the user identities must be hybrid identities, managed in Active Directory. Hybrid identities require maintaining the AD Domain Controllers where the identities have originated from.
In this post, I’m going to discuss the step-by-step configuration of the Azure Storage account and Azure files to support Azure AD Kerberos on AVD FSLogix User profiles.
Enable Azure AD Kerberos on Azure files
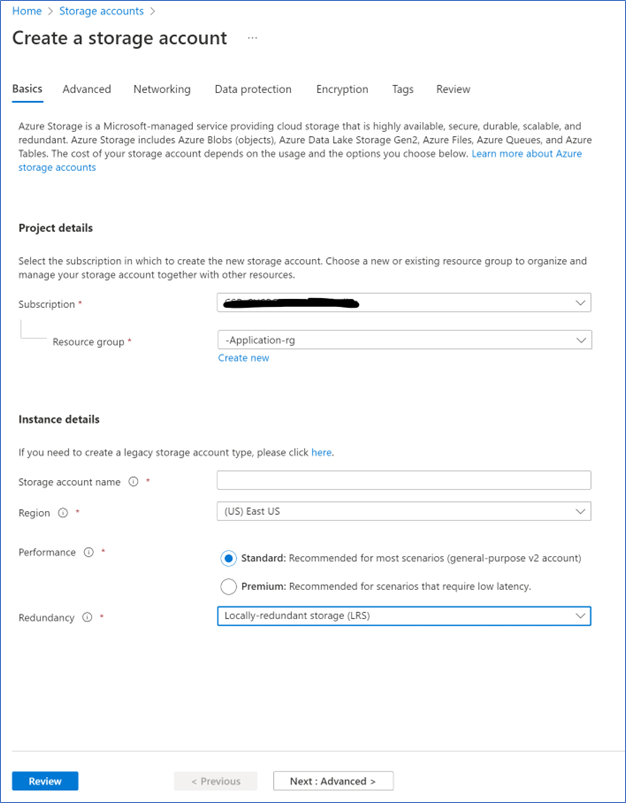
- First, create a new Azure Storage account, you cannot use a storage account which is already enabled for Active directory domain services or Azure AD Domain Services.
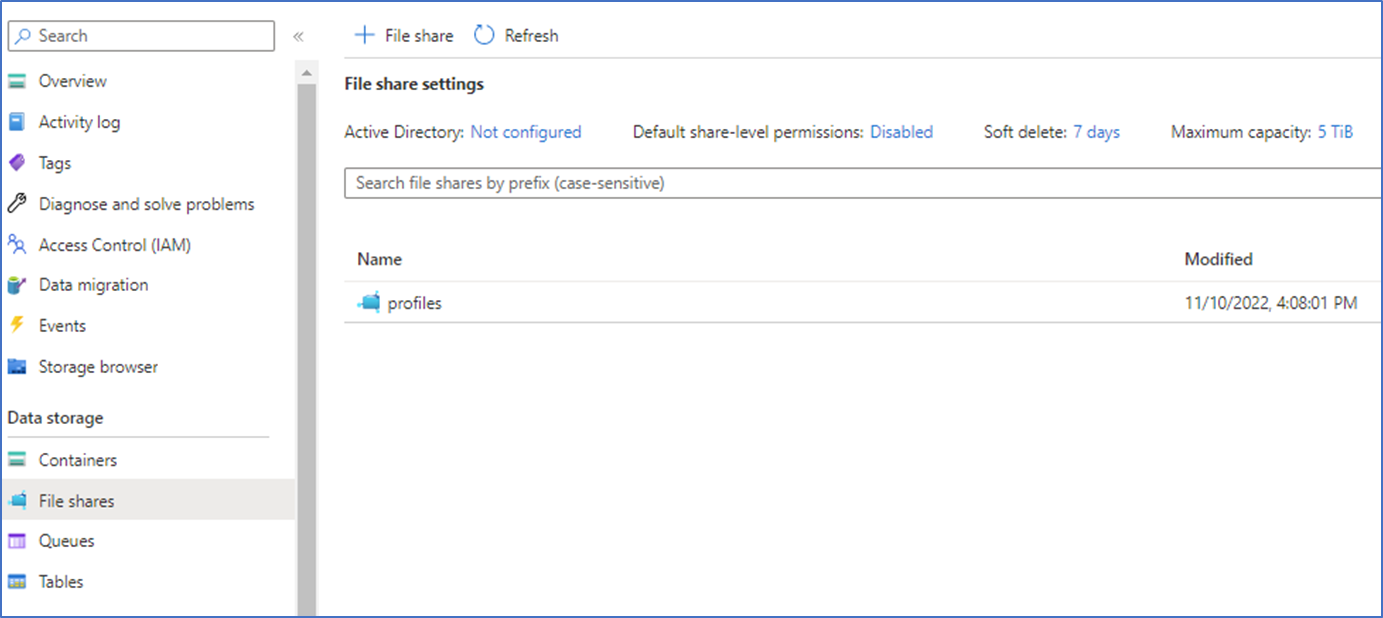
- Next, create an Azure File share on your Storage account
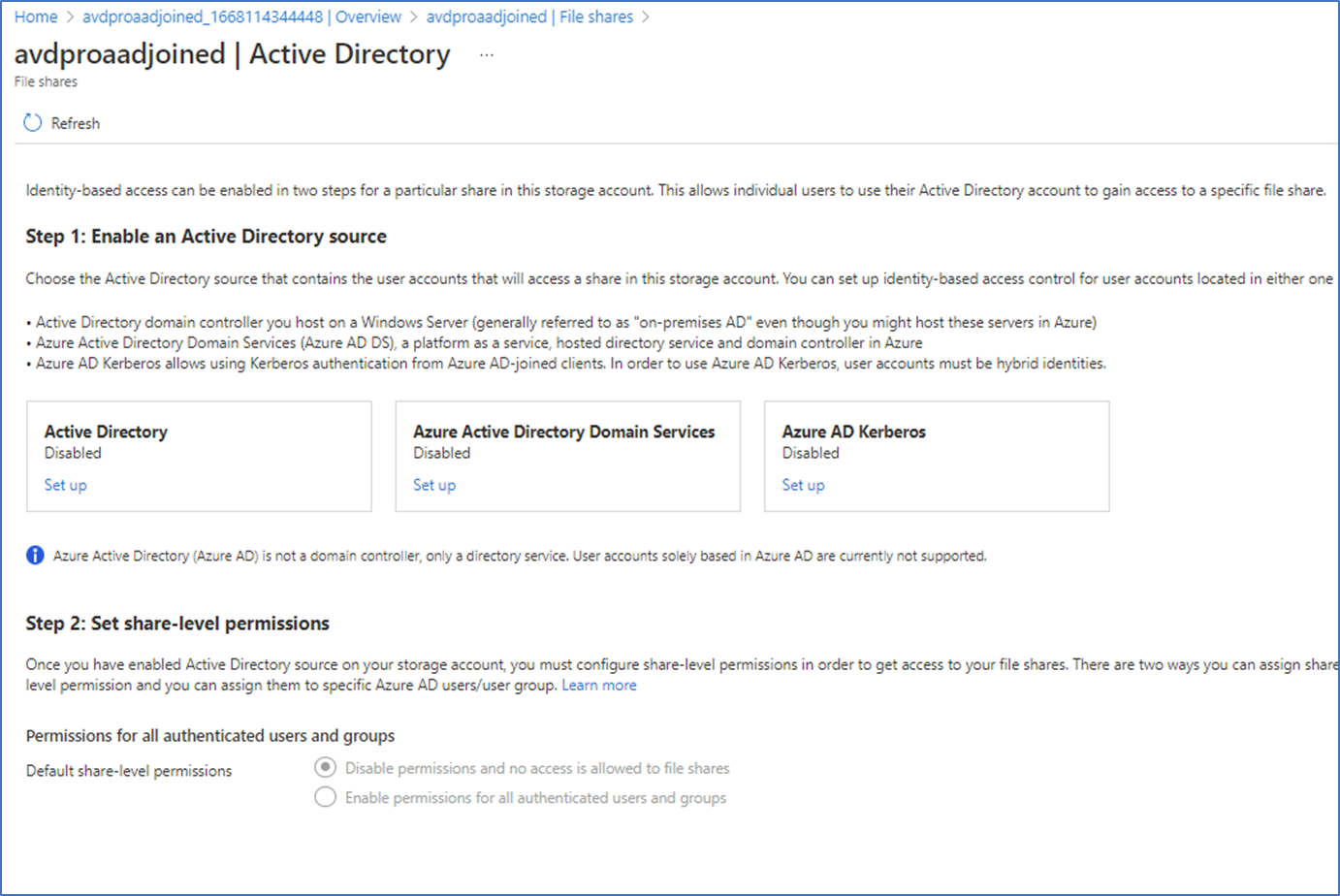
- On the file share, click Active Directory: Not Configured to configure the authentication and Click Azure AD Kerberos setup
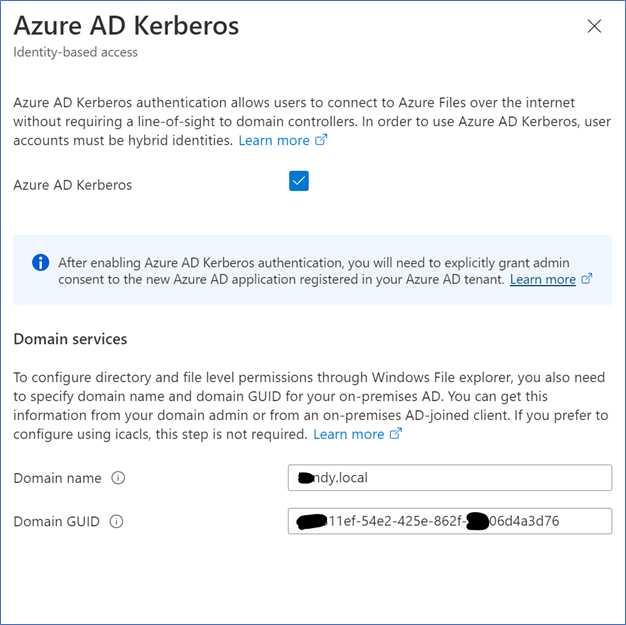
- Tick Azure AD Kerberos,
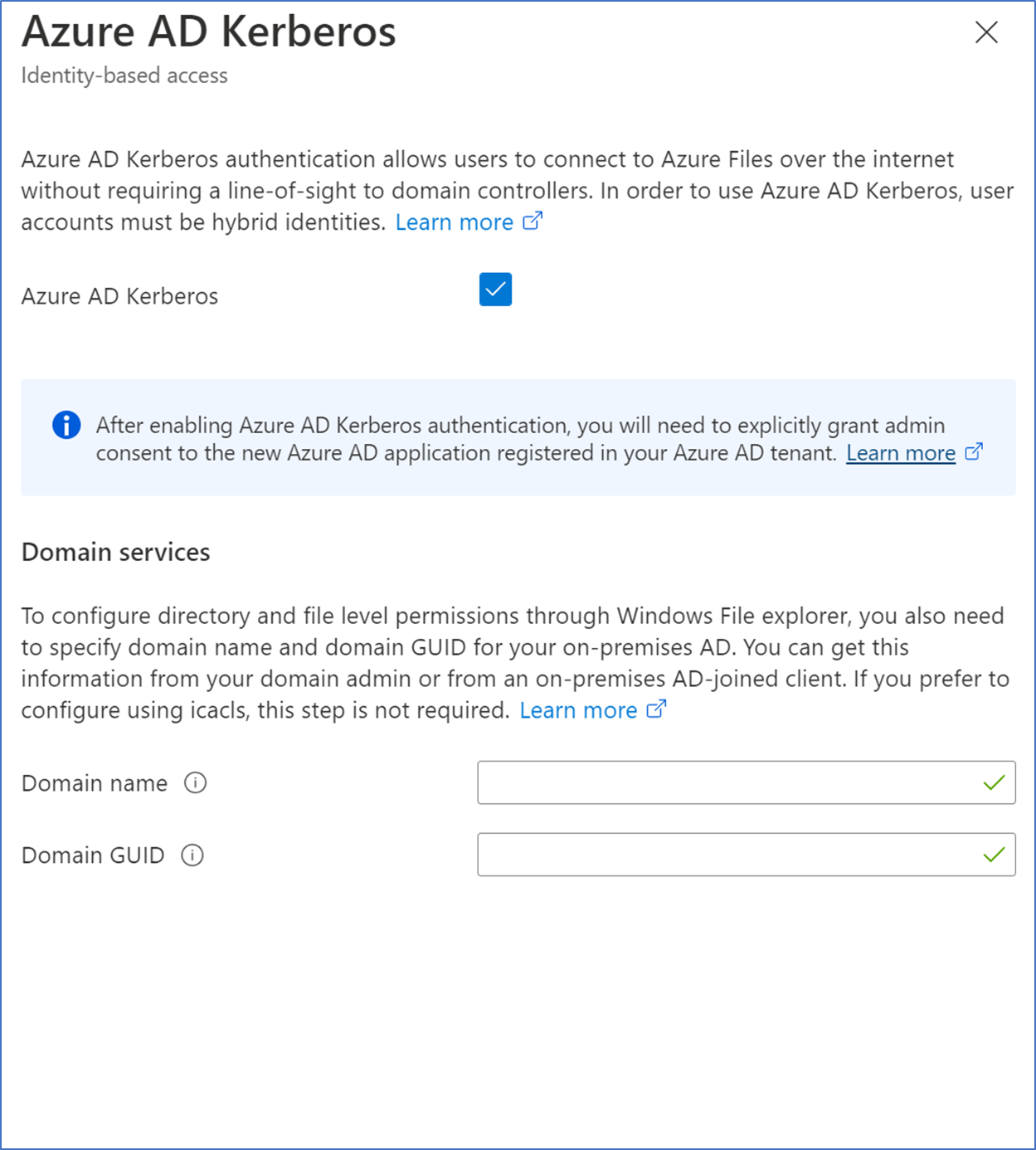
- Next, you need to add the Domain name and Domain GUID, this is important in AVD user profiles. It will help you to configure the file-level permissions for the hybrid users. Without proper directory-level permissions in place, users can access the user profiles or access the personal information of a different user. It's important to make sure users have proper permissions to prevent accidental deletion.
You can run the below PowerShell commands on your domain controller to grab Domain information
$domainInformation = Get-ADDomain
$domainGuid = $domainInformation.ObjectGUID.ToString()
$domainName = $domainInformation.DnsRoot
Configuring file-level NTFS permissions
Correct Folder permissions need to be created for AVD user profiles. Without proper directory-level permissions in place, a user can delete the user profile or access the personal information of a different user. It's important to make sure users have proper permissions to prevent accidental deletion from happening.
There are two permissions you need to set under Storage Account: RBAC permissions and file-level NTFS permissions. File-level permissions can be set to users or groups. This requires using a device with line-of-sight to an on-premises AD. To use Windows File Explorer, the device also needs to be domain-joined.
- Login to Azure Portal, click the Storage Account – Azure file share – Access control (IAM) and click Add role assessment
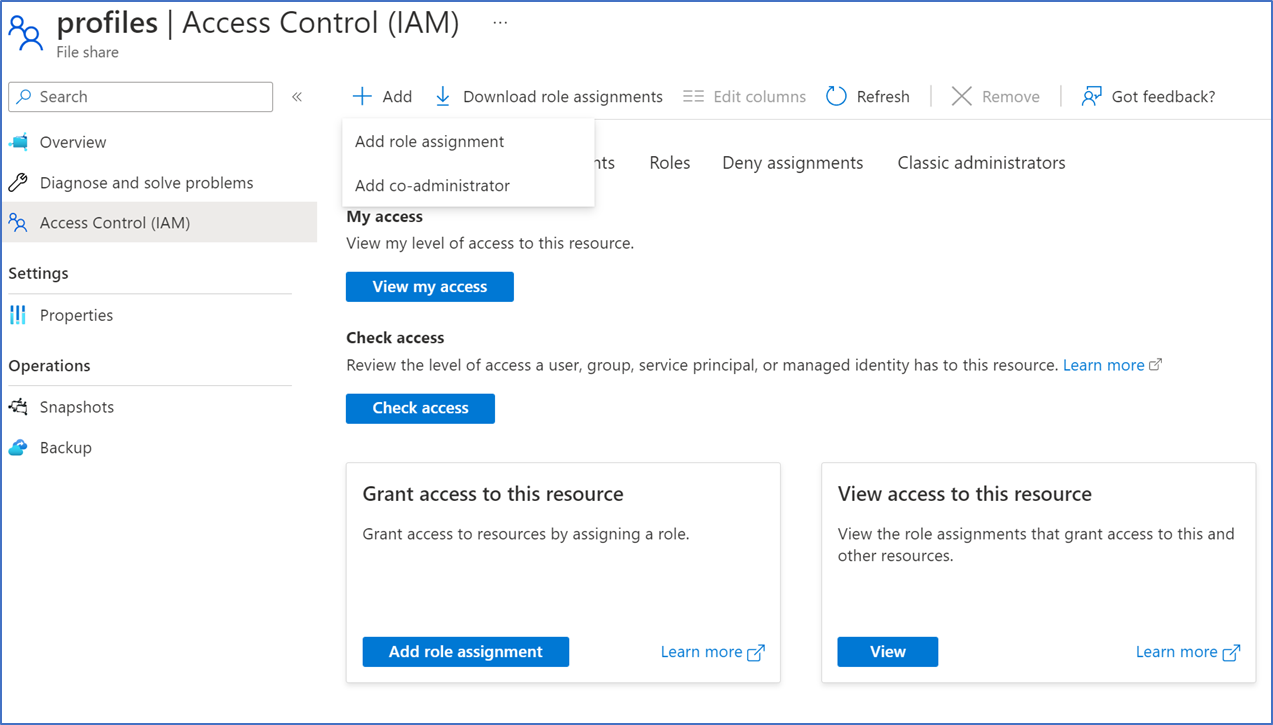
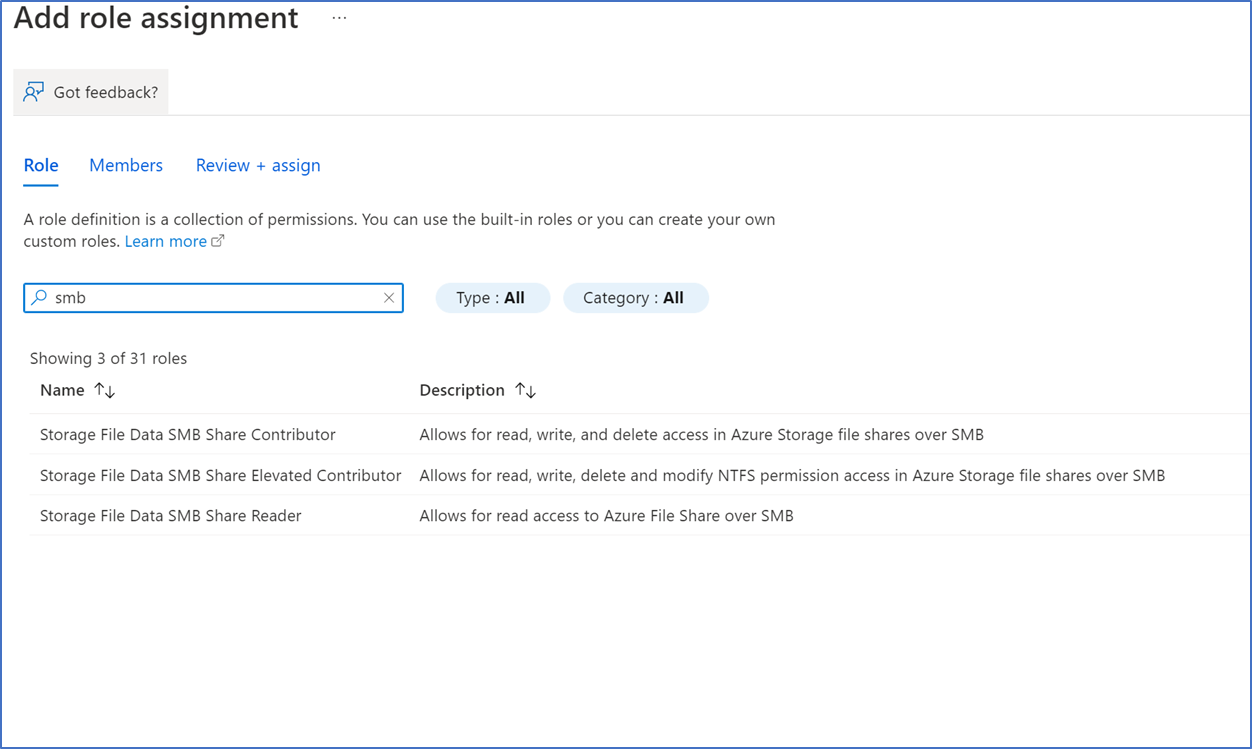
- Type SMB and assign AVD Administrators user groups to SMB share Elevated Contributor and add AVD users to SMB share Contributor role.
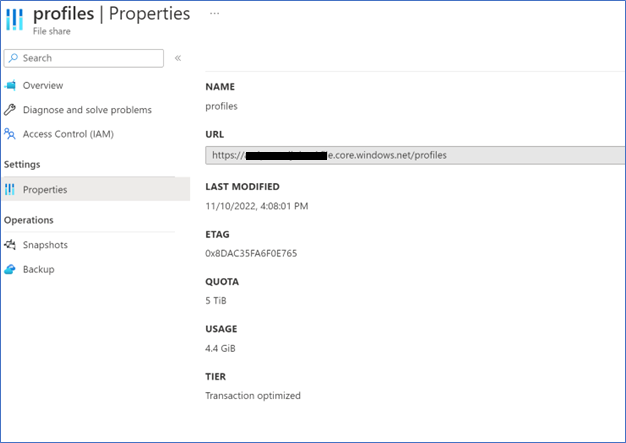
- On the storage account – file share – properties to copy the file share path
- To set file-level permissions, log in to a domain-joined device and access the profile path from file explorer. Change the URL to the File URL as shown below:
\\avdproaadjoined.file.core.windows.net\profiles
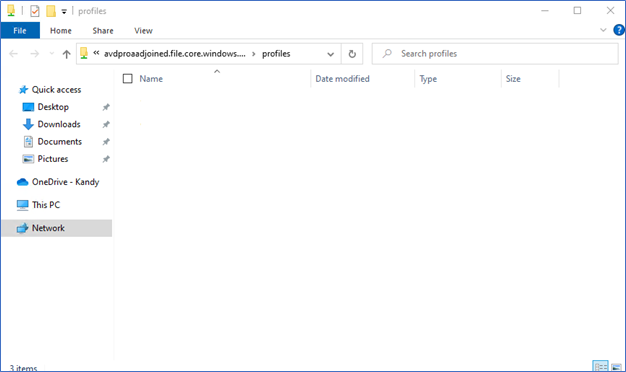
- If you cannot access the share path this way, you can use the Net use command with the storage account key to mount the drive
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> <storage-account-key> /user:Azure\<storage-account-name>
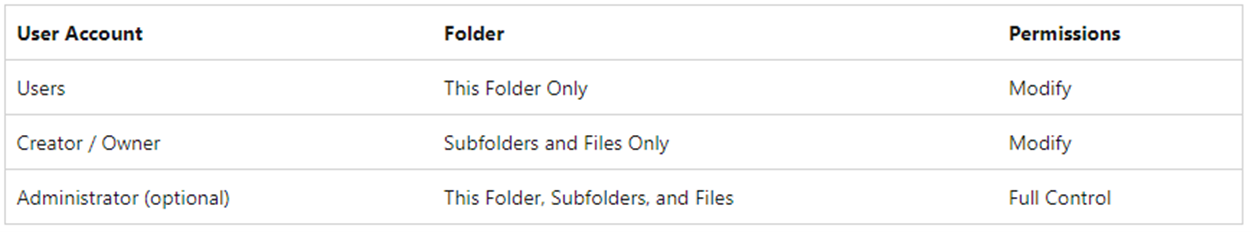
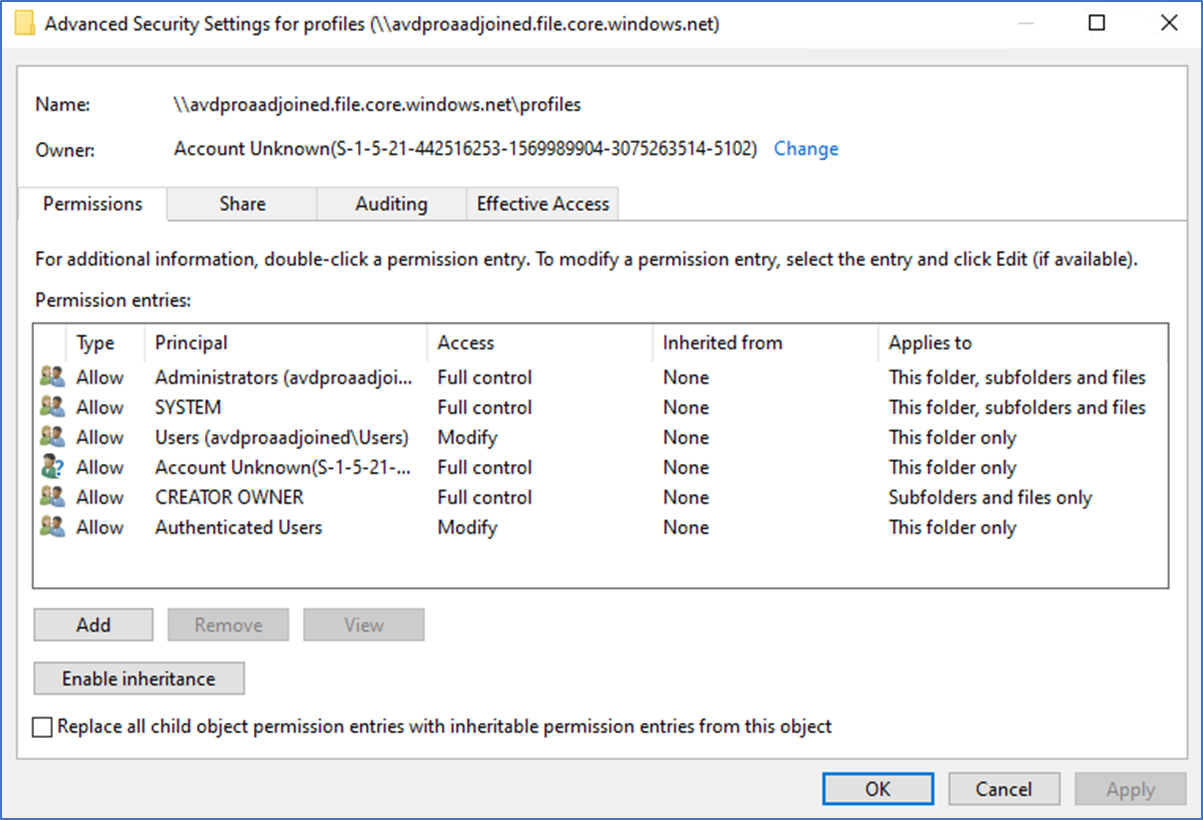
- Right-click and go to properties of the share and set the below permissions to your domain groups
Configuring FSLogix client
The final step is to install the FSLogix client in the host VMs and push the configurations. If you are using the Windows multi-session + Microsoft 365 Apps image from the marketplace, the agent is already installed in it. To push the FSLogix configurations, you can use local policies or the registry editor. Alternatively, you can do all these changes to the golden image before capture.
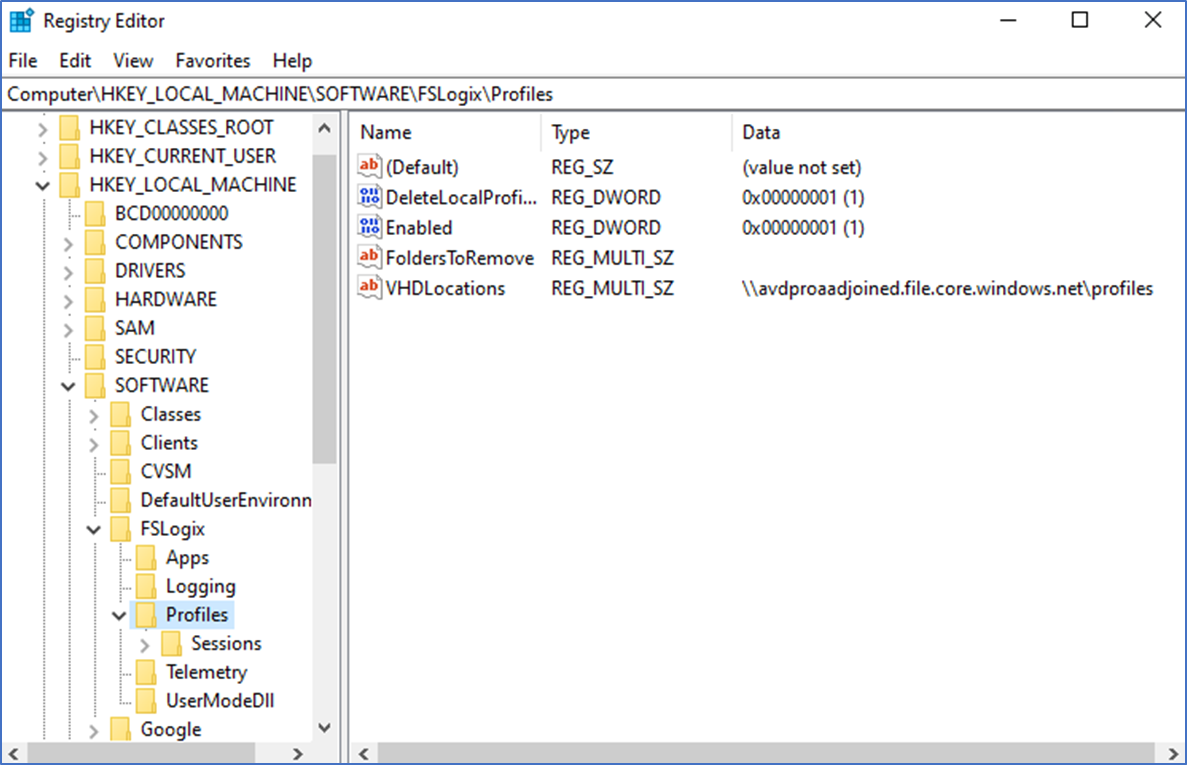
These are the basic registry configurations that are required.
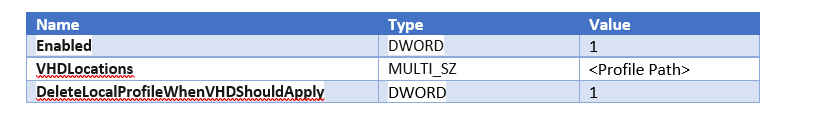
For example
Grant admin consent
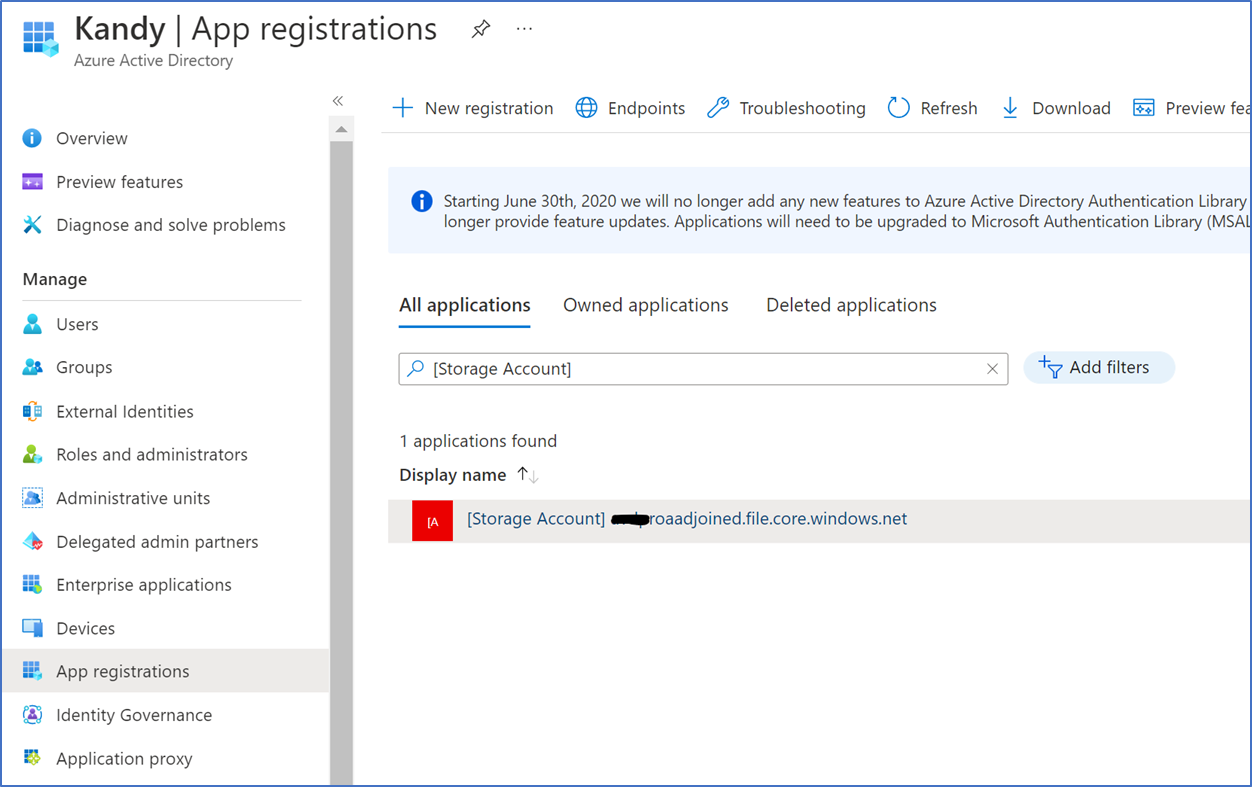
After enabling Azure AD Kerberos authentication, you'll need to explicitly grant admin consent to the new Azure AD application registered in your Azure AD tenant to complete your configuration.
Azure Active Directory – App registration – all applications
Type the application name in the search –
[Storage Account] <your-storage-account-name>.file.core.windows.net
Example –
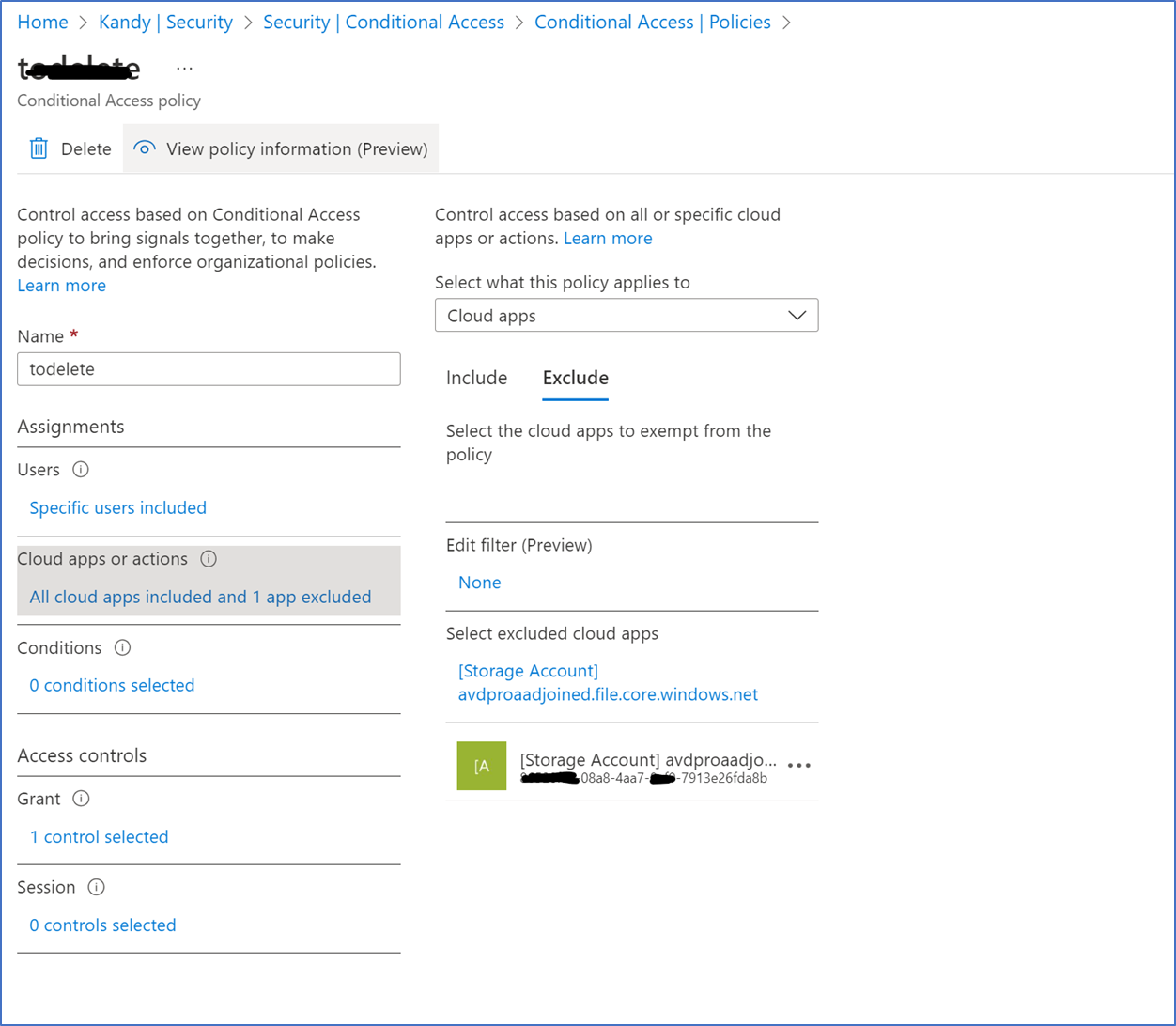
Azure Multifactor Limitation
Azure AD Kerberos doesn't support using MFA to access Azure file shares configured with Azure AD Kerberos. If you have an MFA policy targeted to all cloud apps, you need to exclude your Storage account from that policy.
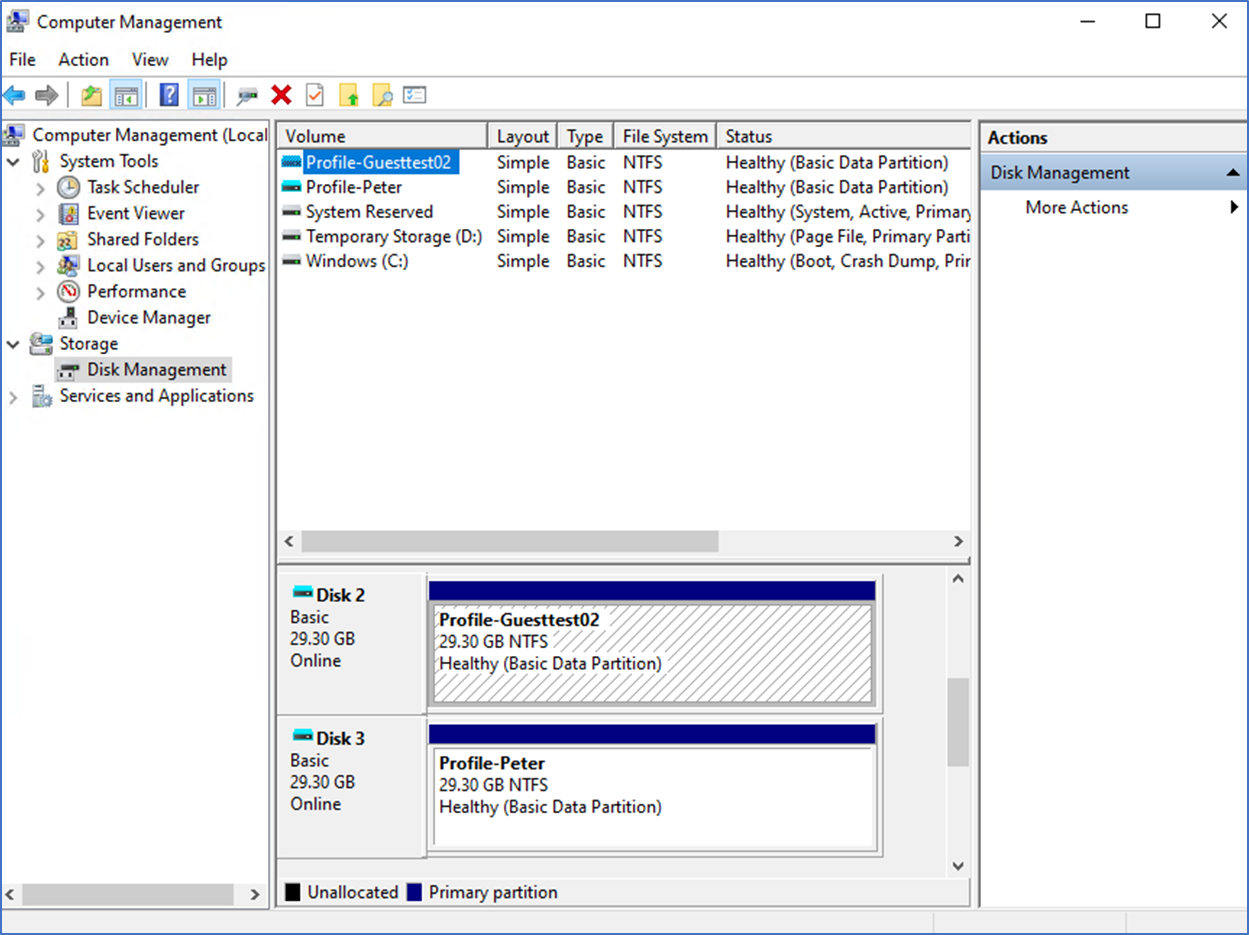
Test configurations
When everything is configured correctly, you can see the profile loading when the user logs in. Make sure you have the correct Storage account RBAC and file-level permissions configured.
Hope this post is useful.
Thanks

















