
The rate of technological innovation has been astounding in recent years. As businesses take advantage of technological innovation, cybercriminals also benefit from it. As a result, the way we approach space must change. Cybersecurity should focus on problem management rather than problem resolution because cybercriminals constantly change their methods of infiltrating systems and do not adhere to any rules. As a result, industry vendors cannot claim that their solutions have solved the security.
Today many businesses and security teams have a finite mindset. Organizations should think and act differently to face sophisticated cyber threats, especially when it comes to cloud security, where the pace of innovation and complexity can be staggering. Microsoft has an approach to cloud security with an infinite mindset. They use intelligence, AI, and automation to create a virtuous cycle of signals to evolve and respond faster to cyber criminals and events. In the SolarWinds incident, attackers exploited vulnerabilities much earlier in the development lifecycle of the code itself. It opened the need for industry collaboration to share threat intelligence and respond as a team.
Code to cloud
Microsoft's cloud security approach spans from code to the cloud, regardless of the cloud technology you use, and employs intelligence and automation to help you be secure. It starts with outstanding runtime protection, which allows you to protect all of your workloads in the cloud, including VMs, data apps, devices, and networking, not just in Azure but across all clouds you operate. It requires comprehensive visibility and a simplified way of remediating issues across all these assets. You must consider security earlier in the development lifecycle, beginning with the code and shifting later. Customers need to connect security and DevOps teams more effectively to help developers bake security earlier in the experience and remediate issues in the code itself. It is necessary to do that across pipelines whether you're using GitHub, Visual Studio, Azure DevOps, or other pipelines.
Microsoft Defender for Cloud
That's the approach Microsoft brings to cloud security, from the development cycle to runtime protection, uniquely powered by intelligence generated from trillions of signals in the cloud, along with insights from thousands of the best security researchers in the industry. This is possible with Microsoft Defender for Cloud, a comprehensive cloud security platform. It helps to strengthen your security posture, protect workloads across multi-cloud and hybrid environments, and secure your organization from code to cloud. Security teams are dealing with disconnected tools, gaps in coverage across their environment, and countless security issues. It is more difficult than ever to identify and focus on what is most important. Defender for Cloud is a centralized platform that provides you visibility across your entire environment, allowing you to strengthen your security posture against evolving threats and prioritize risk with graph-based analysis. It also helps you accelerate remediation with integrated governance tools across clouds once you've identified your most serious security issues.
How Defender for Cloud helps transform cloud security
It becomes increasingly important to proactively reduce risk as organizations expand their deployments across multi-cloud environments. With advanced prioritization and remediation tools, Microsoft Defender Cloud Security Posture Management builds on existing capabilities to provide centralized visibility into your entire environment.
Let's start with the Defender for Cloud dashboard to understand and respond to cloud security risks.
The overview page helps to understand the cloud security posture across Azure, AWS, and Google Cloud deployments. It also provides a quick view of cloud security compliance against industry standards, a complete resource inventory, and a summary of your workload cloud protection. In the right panel, you can track the latest vulnerabilities and insights from Microsoft's industry-leading threat Intelligence researchers. Strengthening your security posture begins with visibility. Here, you can see that Defender for Cloud is continuously assessing 3,300 resources across the environment.
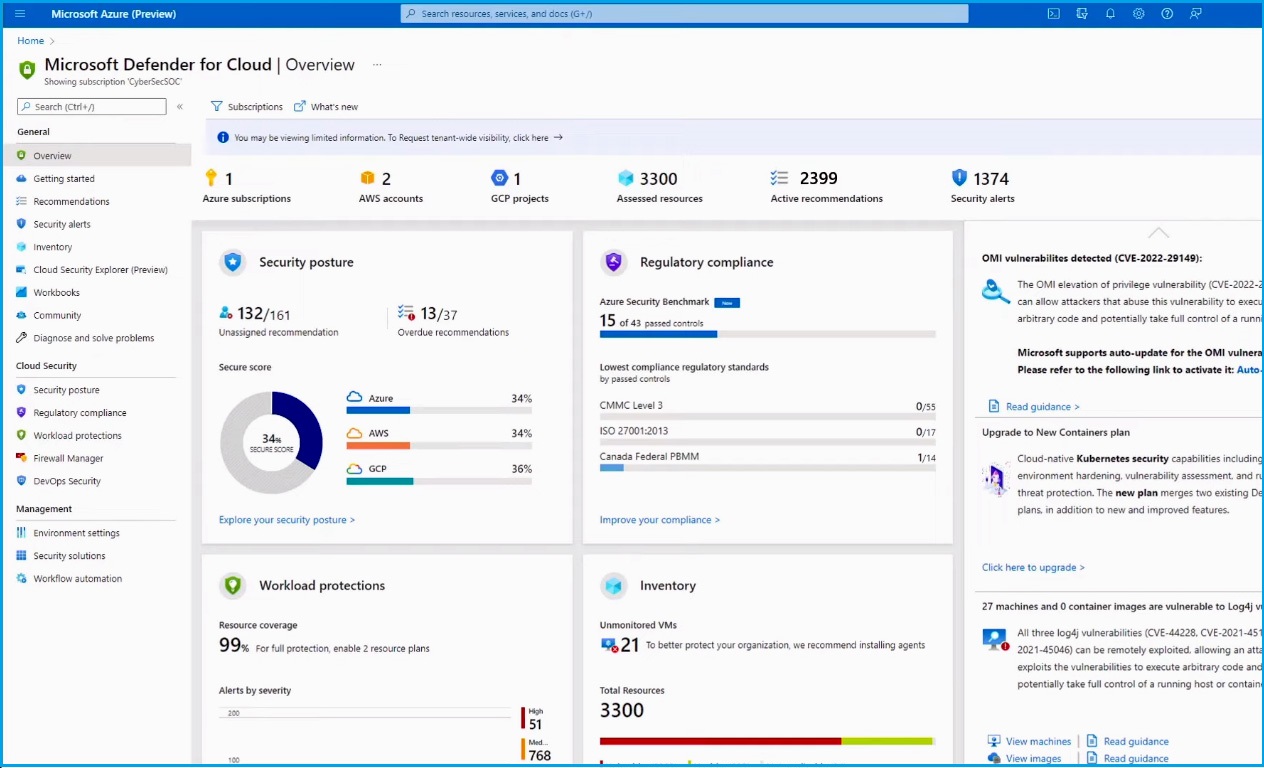
In active recommendations, you can see groupings of key recommendations, including areas such as Identity from Entra Permissions Management, Endpoint Protection, and Vulnerability Management.
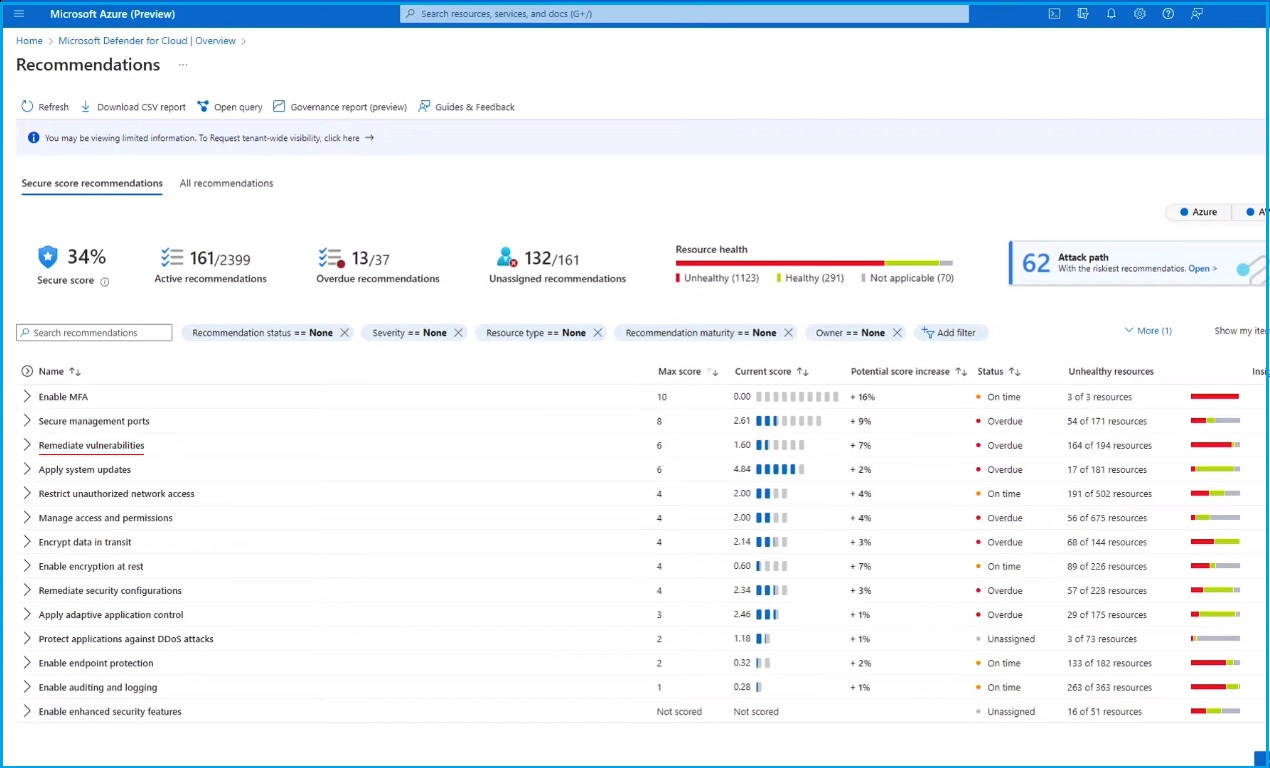
Defender for Cloud ensures complete workload protection with new agentless vulnerability scanning. It seamlessly scans all multi-cloud resources in your environment without the friction of deploying an agent and with zero impact on workloads. Defender for Cloud is one of the only solutions providing full breadth and depth of coverage, marrying the visibility of agentless scanning with in-depth agent-based endpoint protection.
In the "Remediate Vulnerabilities" section, you can see a top recommendation highlighting a large group of resources with unresolved vulnerabilities.
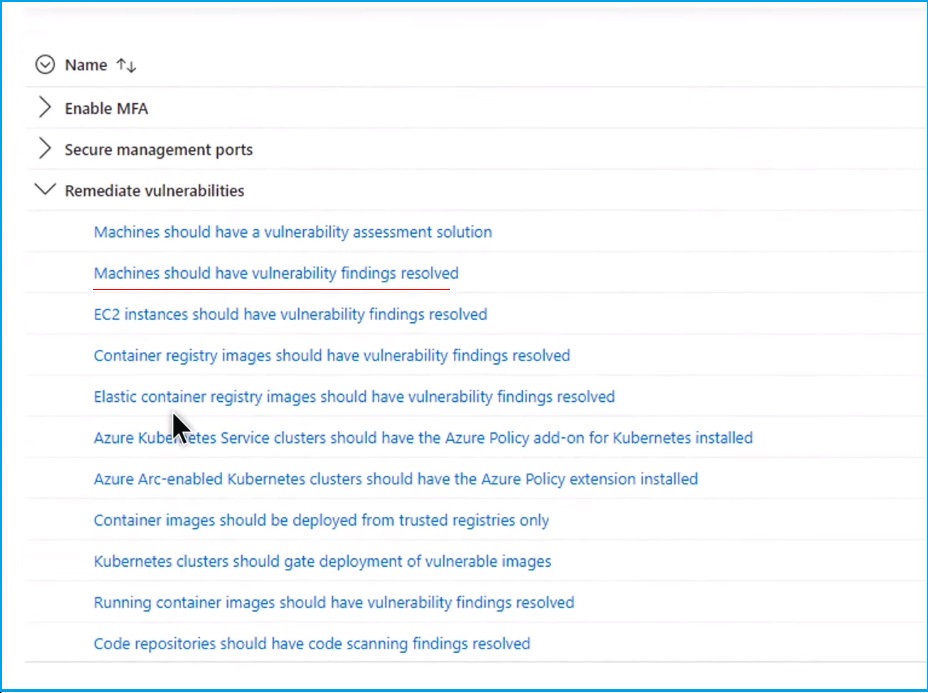
Hundreds of high-severity CVEs found in scanned Azure VMs and AWS EC2 instances are displayed here. Selecting one of these resources will give you a more detailed look at the specific issue.
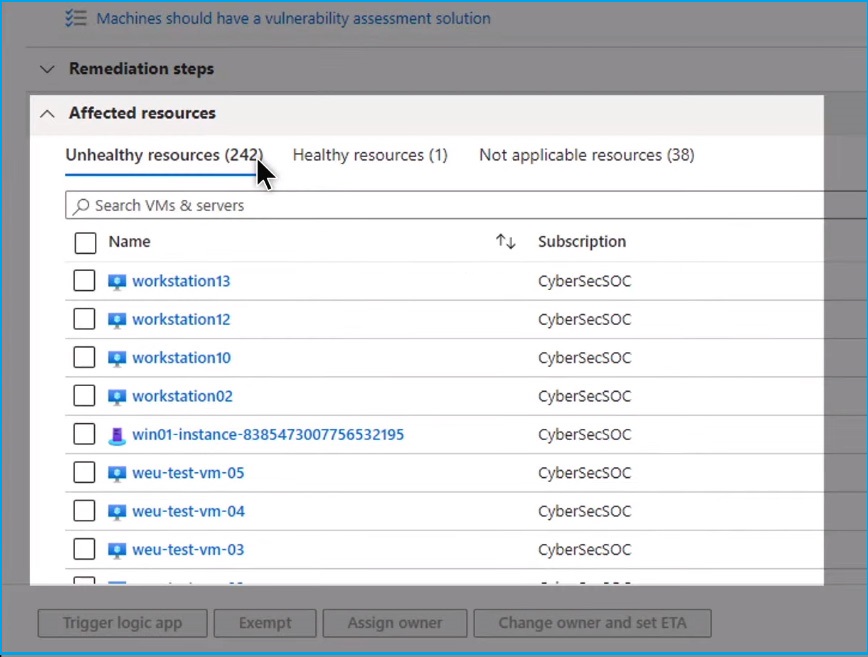
In the "Recommendations" tab, the Attack Path analysis tool helps you focus on the most pressing risks. It is based on the Cloud Security Graph, which brings insights from all your cloud resources, External Attack Surfaces, and Entra Permissions Management. This data is analyzed to identify the most exploitable vulnerabilities across all potential paths. The Cloud Security Graph's threat context cuts through the noise, narrowing down from thousands of recommendations to show you potential attack paths that require your attention.
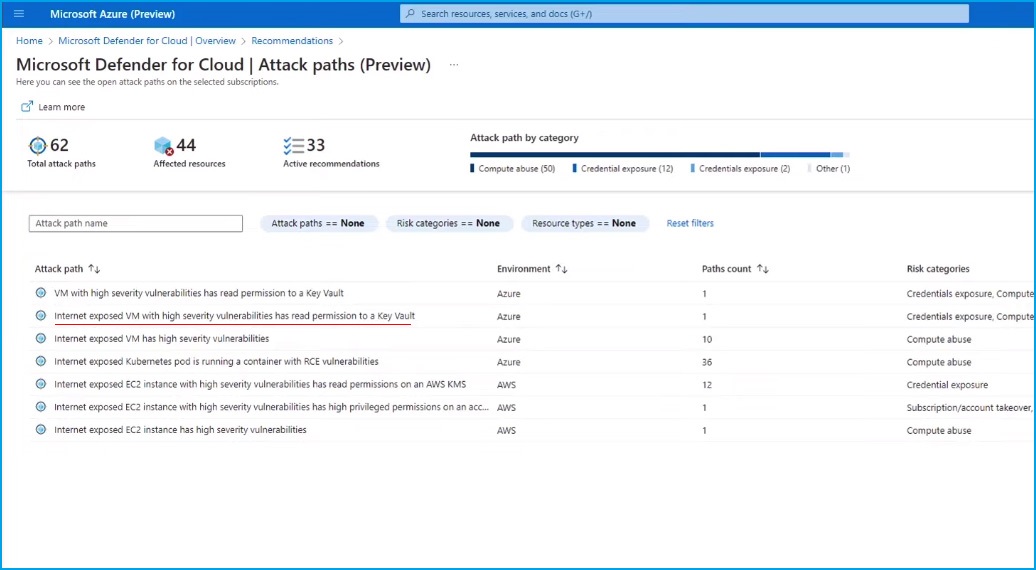
Let's check one to learn more. This attack path involves a virtual machine with high-severity vulnerabilities. It's exposed to the internet, has remote code execution, and has access to a sensitive Key Vault.
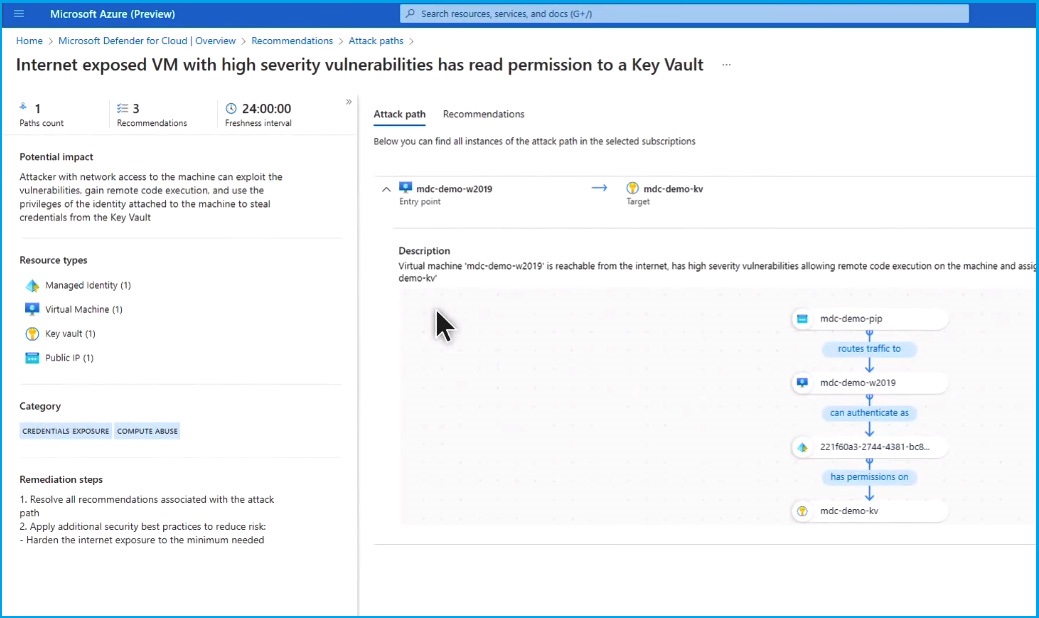
By clicking on the "Virtual Machine," you can see the contextual risk for each node and the environment, its internet exposure and details on related vulnerabilities, and critical recommendations to mitigate this risk.
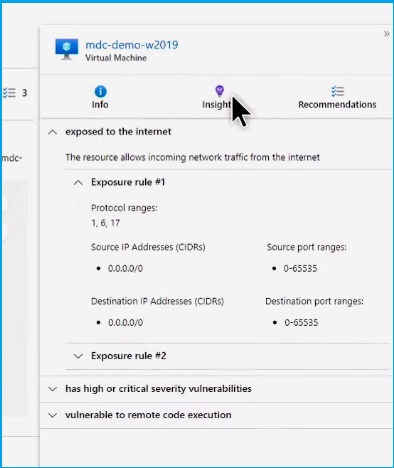
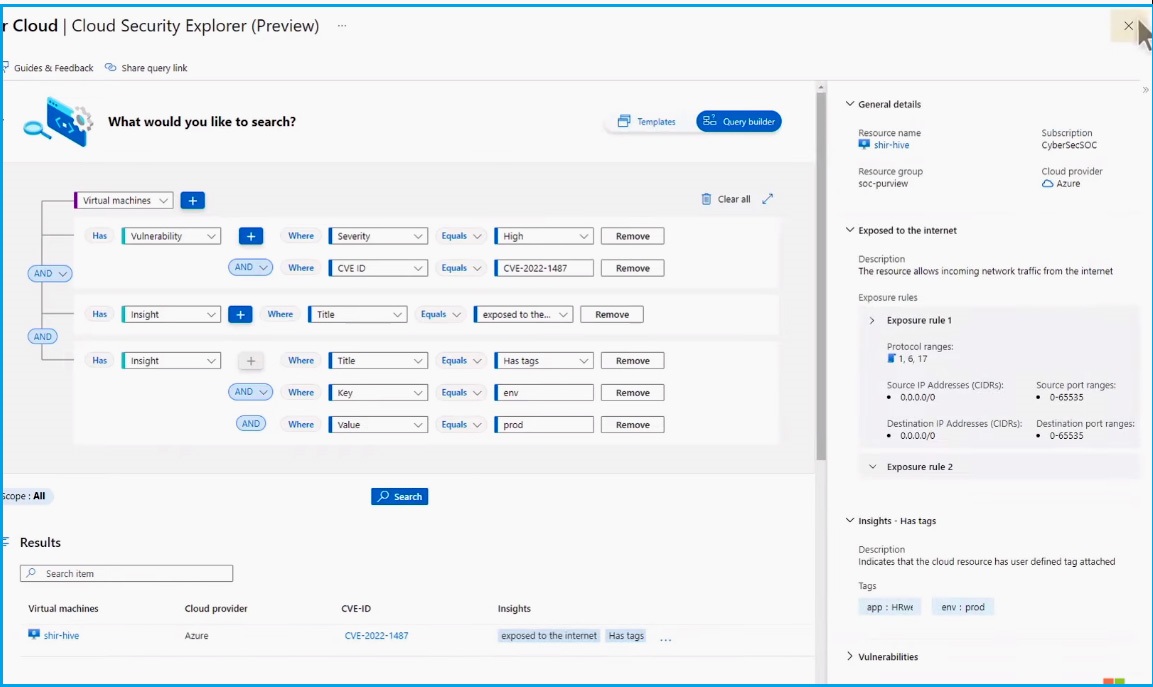
When you need to search for specific vulnerabilities or resources using parameters unique to your environment, you can do that with the Cloud Security Graph Explorer.
Return to the Defender for Cloud dashboard and select the Cloud Security Explorer.
For example, if external exposure is a top concern in your organization, you can start by searching for internet-exposed VMs. Here, you will find a long list of VMs matching the high-severity criteria for your template.
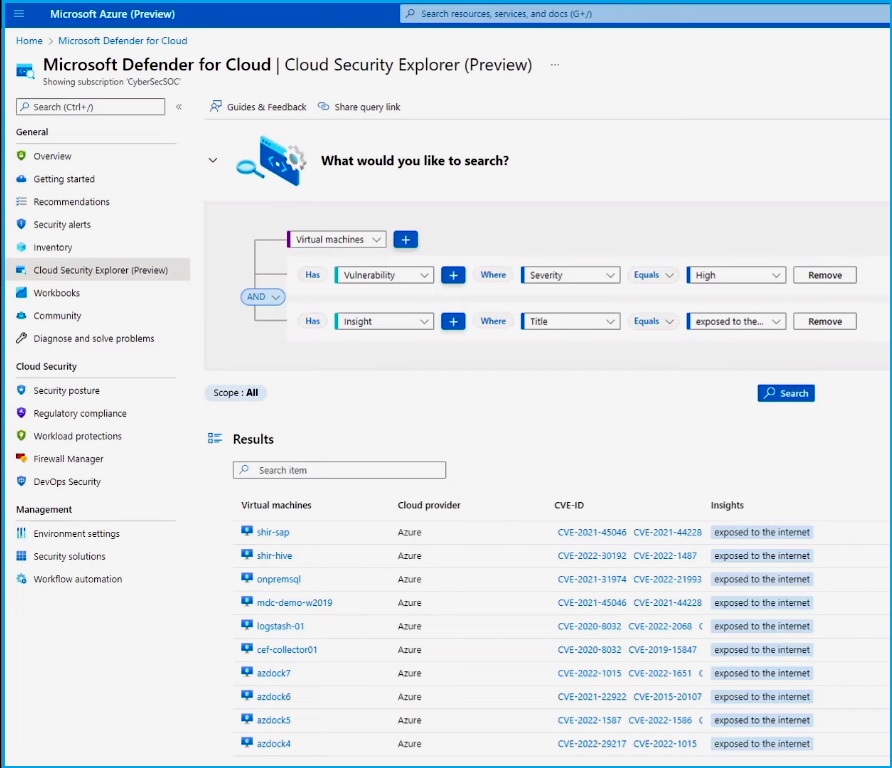
The Graph Explorer allows you to search for specific insights, such as unique data sensitivity labels or tags your company has defined to identify your production and test environments. You have the option of narrowing your search. For example, you can search for a specific CVE. By checking the results, you can reveal critical details such as how it was exposed, which CVEs were discovered, and relevant tags. Then you can identify and remediate the most critical risks in your organization.
With the new Defender CSPM capabilities for agentless scanning and attack path analysis, SecOps teams can save time and prioritize the most significant risks with context-aware cloud security.
Defender for DevOps
Defender for DevOps helps you bridge SecOps and DevOps with automated discovery across pipelines, starting with GitHub and ADO. It will also continuously assess the posture and compliance of cloud configurations. Think of it as infrastructure as code security that will help minimize misconfigurations ever reaching production. It combines all these insights in a unified view powered by the Cloud Security Graph.
Security teams' major challenge when managing their posture is the fragmented visibility caused by the plethora of cloud platforms, DevOps environments, and disconnected security tools used throughout their organizations. Security and development teams continue to operate in silos, and security tools equip to keep pace with developer velocity. Microsoft Defender for DevOps unifies DevOps Security Management across multi-pipeline and multi-cloud environments, starting with Azure DevOps and GitHub, available today.
Let's take a look at how Defender for DevOps helps you mitigate risks to secure from code to the cloud. Earlier, we explored potentially exploitable vulnerabilities across the Azure and AWS Clouds.
Go to the Defender for Cloud dashboard and select DevOps Security.
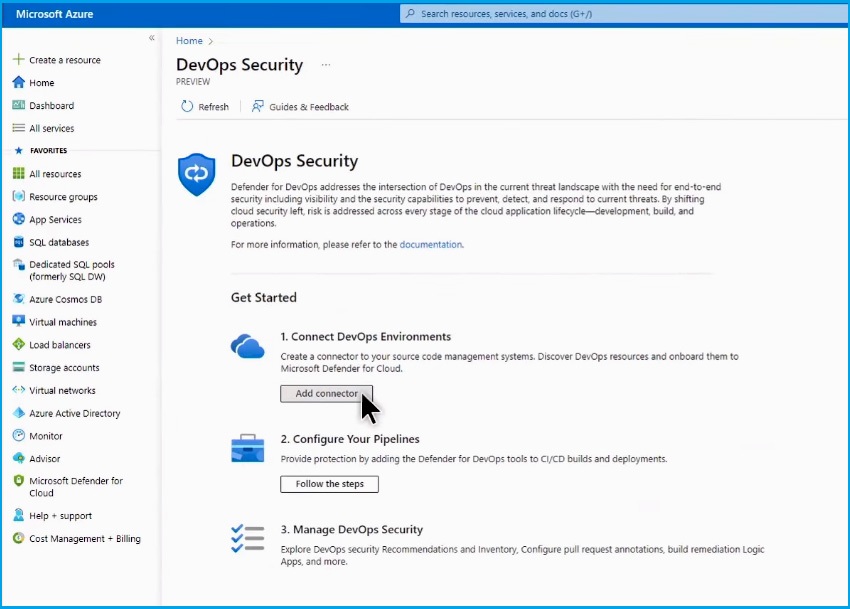
To begin, connect to GitHub and import all DevOps environments into Defender for Cloud.
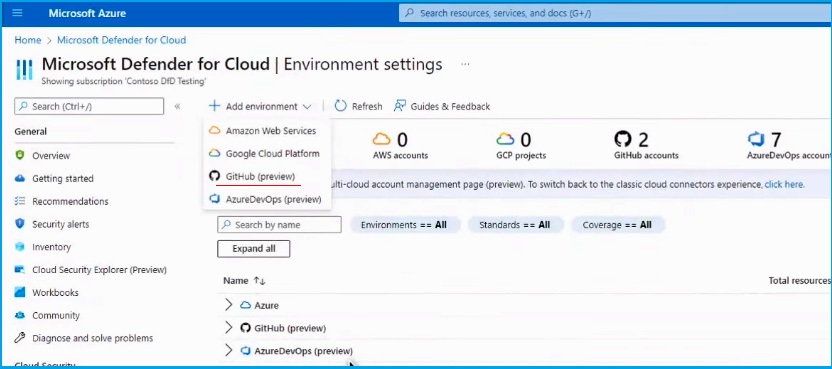
You can authorize the connection and define key details such as a name, resource group, and region here.
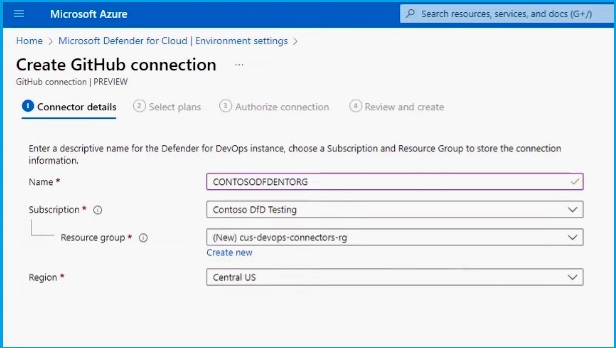
You can see that you have successfully connected to your GitHub environment. Behind the scenes, Defender for Cloud is onboarding all of your resources. You can also integrate with GitHub Advanced Security to analyze the code for vulnerabilities.
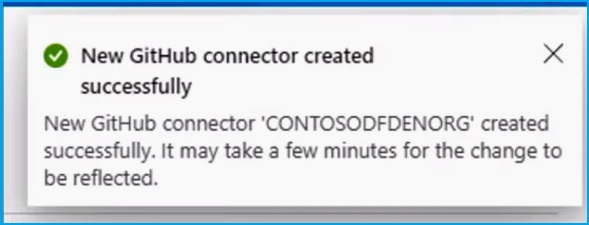
There are two connectors available in the Defender for Cloud portal: GitHub connectors and Azure DevOps connectors, for a total of 21 repositories. All of your GitHub and Azure DevOps repositories are listed in the table below, along with information on your top security concerns: pull request status, exposed secrets, open-source vulnerabilities, and code scanning vulnerabilities. You can drill down into each repository to view the specific recommendations and take action to remediate the risks.
The GitHub is now connected. To begin, enable infrastructure as code security on the GitHub repositories to prevent cloud misconfigurations in production environments.
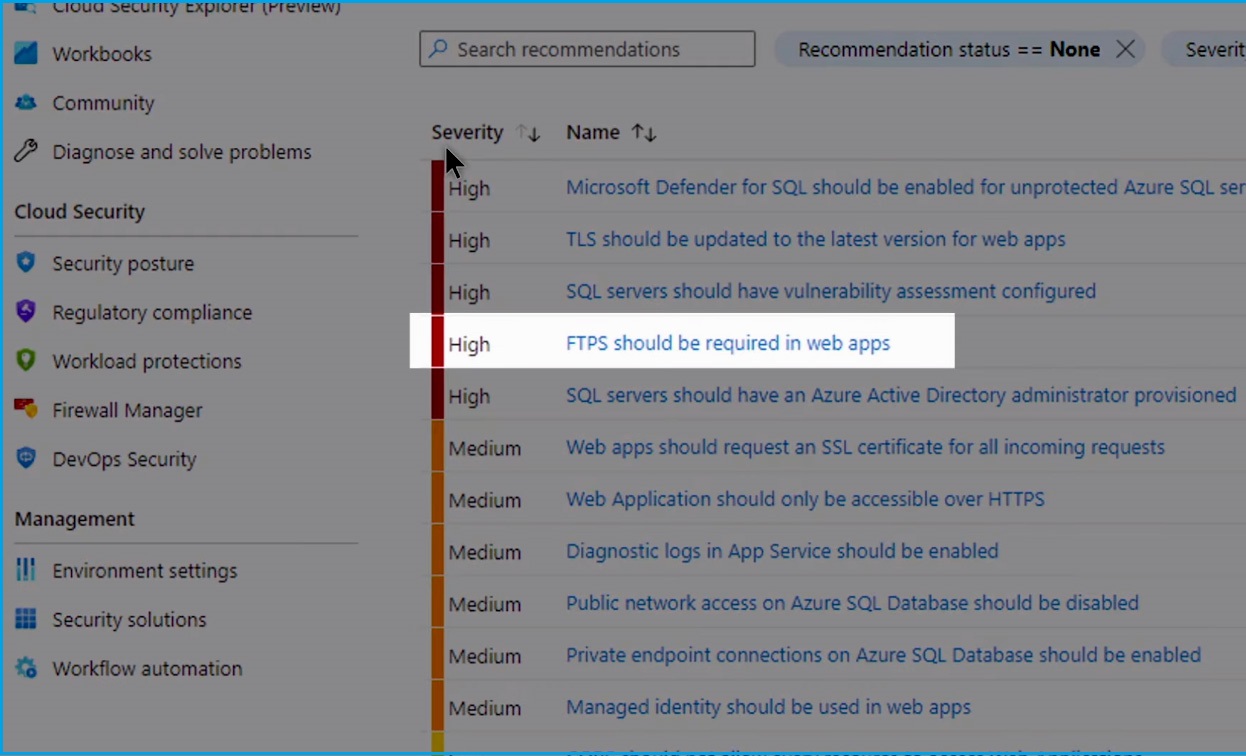
Navigate to the "Recommendations" page and select the "All Recommendations" tab. There are numerous critical issues and items labeled as unhealthy. By utilizing Defender for DevOps' integrated capabilities, you can reduce the volume of security issues by shifting left and fixing these issues in the developer workflow, preventing them from ever appearing as vulnerabilities in production.
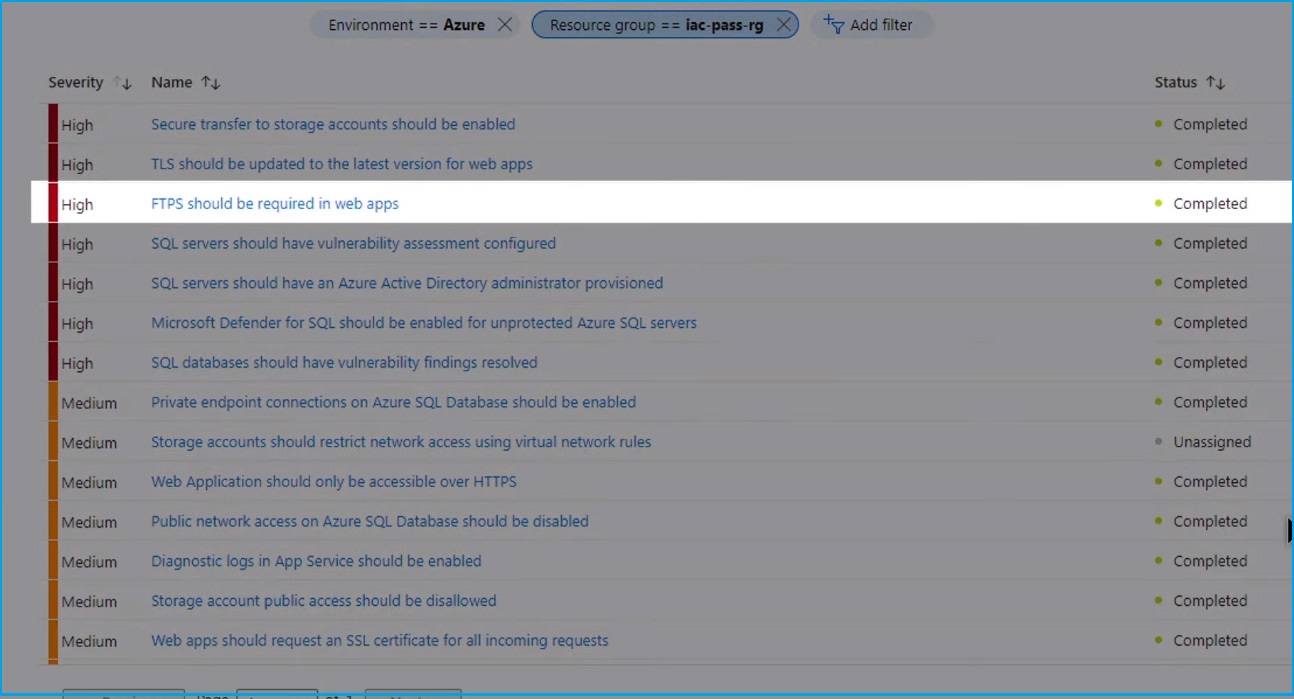
Let's look at one of the most common and widely exploited misconfigurations: FTPS should be required in web apps.
Go to GitHub and select "Actions" to examine your workflow deployments, where you set up GitHub Actions for your Defender for DevOps tools. This will scan any infrastructure as code or IaC templates committed to a repository.
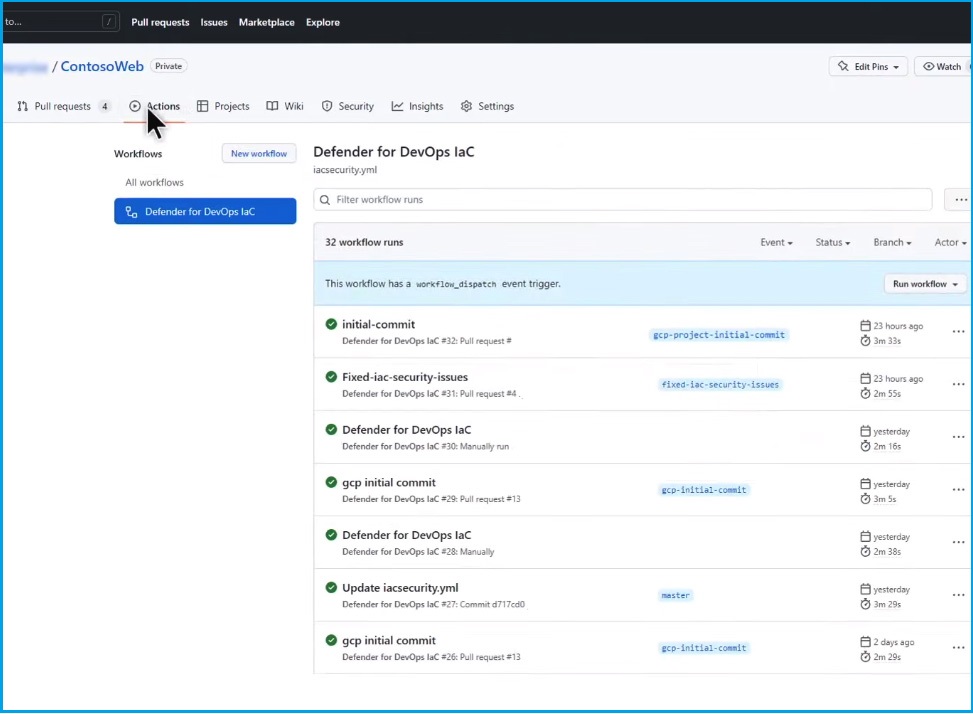
Next, check the "Pull Requests," where you will find several across Azure, AWS, and Google Clouds.
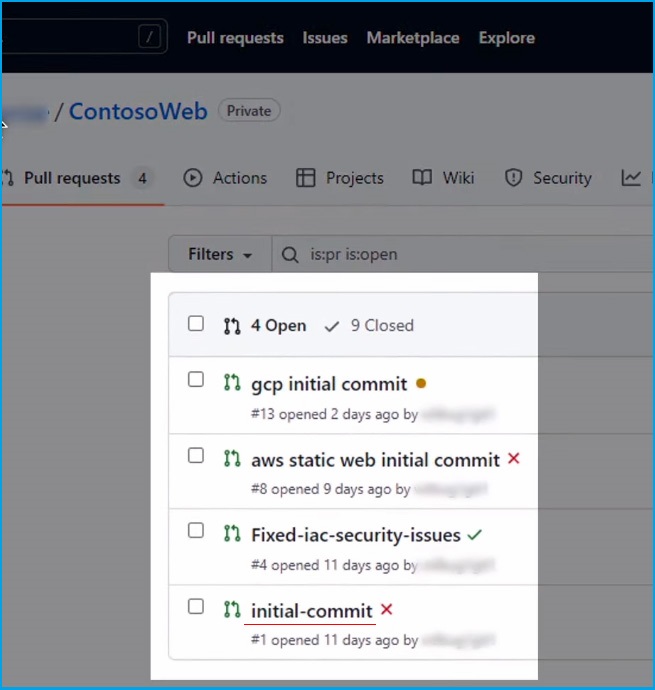
Let's start with the Azure workload. The Defender for DevOps discovered some IaC misconfigurations in the CI/CD pipeline. Here, you can see the recommendation (FTPS should be required in web apps) you saw in the Defender for Cloud console. The developer can see the precise location in the code to resolve the issue.
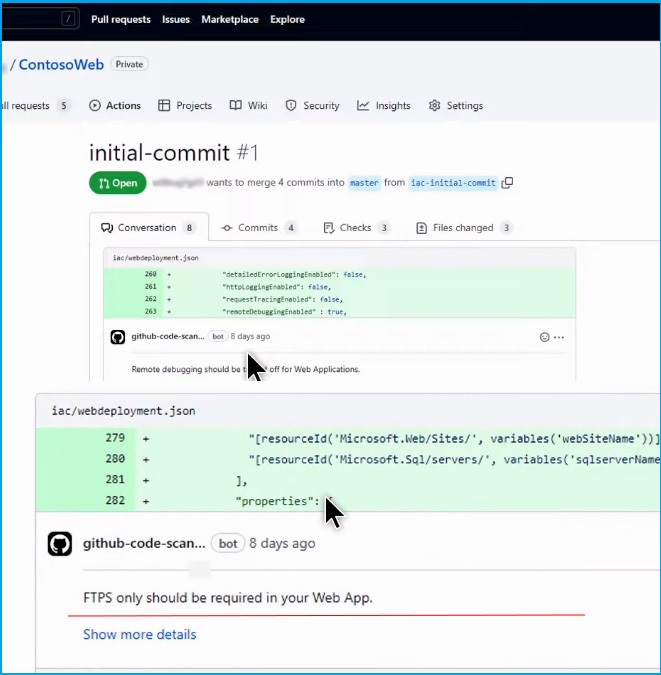
By integrating Defender for DevOps with GitHub advanced security, developers see the same recommendations in their tools as security admins see in Defender for Cloud—no need to switch to a different console.
Switch to the developer's IDE in Visual Studio Code. Here, you can empower the developer to fix these issues even earlier. First, ensure the developer has installed the GitHub Pull Requests and Issues extension in their Visual Studio Code IDE. This will allow them to interact with the pull request information without leaving the IDE.
Go to the s-code and open the IaC workload project. Select the webdeployment IaC template and scroll down. You can see that the same recommendations (FTPS only should be required in your Web app) appear inline, as you saw in the Defender for Cloud console.
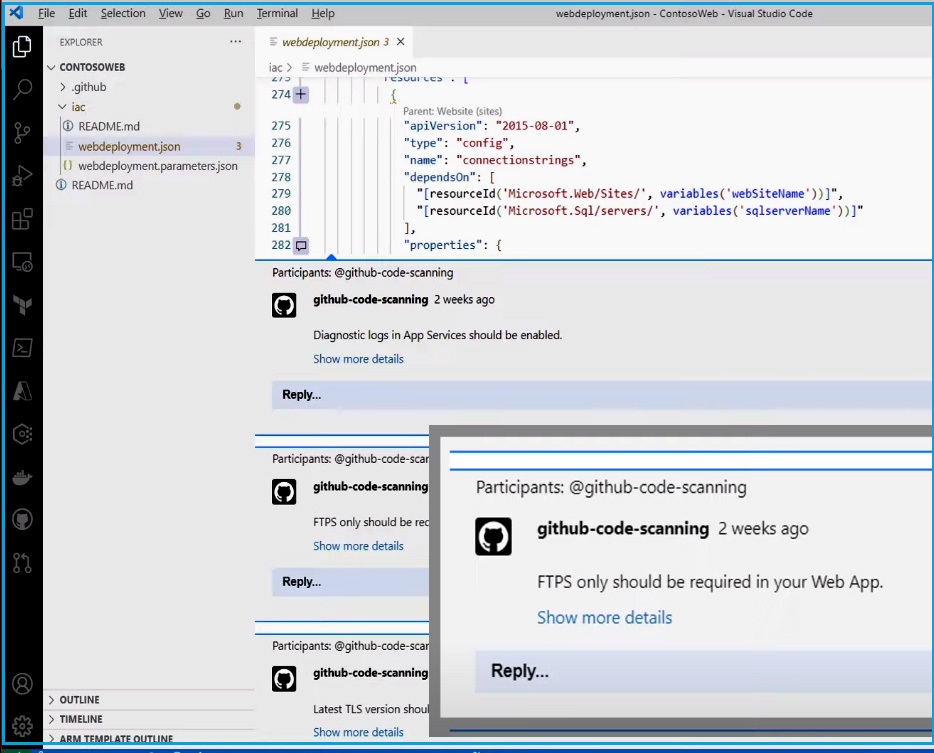
The developer can see the line of code that needs to be fixed and click to see more details on how to fix it without having to switch tools. Now, the developer can address the issue and submit another pull request. It prevented this issue in the code, so it never reached the cloud.
Go to the security operator's view in Defender for Cloud, and notice that the pesky FTPS recommendation now shows all healthy.
You can prevent issues in the code from reaching the cloud and reduce the workload for your security team. Previously, we searched for specific vulnerabilities in Azure and AWS runtime resources. You can now use the Cloud Security Graph and Graph Explorer to identify vulnerabilities in your connected DevOps environments. All of these capabilities in Defender for Cloud are fully integrated, allowing you to use the intelligence in the Cloud Security Graph to explore, identify, and remediate risks from development to runtime.
The Defender for DevOps is now in public preview. You can see how it enables the entire breadth of code-to-cloud security to get your security teams rightfully focused on the new emerging threats way earlier in the life cycle. These new capabilities will empower security teams to unify DevOps Security Management across multi-pipeline and multi-cloud environments without slowing down developers.
Reference:
Microsoft Ignite Session






















