
Domain controllers are fundamental to any Windows-based networking infrastructure, providing centralized authentication and authorization for users and computers. In the cloud, Microsoft Azure is the preferred choice of many organizations for hosting their domain controllers. However, just like on-premises deployments, secure deployment of domain controllers on Azure requires careful planning and implementation of best practices.
In this blog post, we will explore some of the best practices you can implement to securely deploy a domain controller on Azure.
- Azure Enterprise architecture recommendations
- Active Directory best practices
- scalability considerations
- Plan Your Network Architecture
- Implement Security Best Practices
Azure Enterprise architecture recommendations
Microsoft has defined Enterprise scale best practices as part of their Cloud Adoption Framework (CAF). It is to provide prescriptive architecture guidance coupled with Azure best practices, and it follows design principles across the critical design areas for an organization's Azure environment and landing zones.
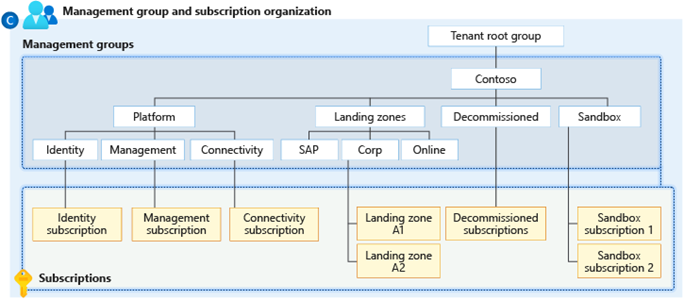
Identity Management Group
This management group contains a dedicated subscription for identity. This subscription is a placeholder for Windows Server Active Directory Domain Services (AD DS) virtual machines (VMs) or Azure Active Directory Domain Services. The subscription also enables AuthN or AuthZ for workloads within the landing zones. Specific Azure policies are assigned to harden and manage the resources in the identity subscription.
Policies for Identity
You can define policies to govern the identity management group and the subscriptions. These policies can be deployed through Azure Landing Zone options.
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/landing-zone/implementation-options#implementation-options
VM Sizing recommendations
VM Size would be based on your expected volume of authentication requests. You can start with the current on-premise specifications to match Azure VMs. Once deployed, monitor the utilization and scale up or down based on the actual load on the VMs.
Capacity planning for Domain controllers - https://learn.microsoft.com/en-us/windows-server/administration/performance-tuning/role/active-directory-server/capacity-planning-for-active-directory-domain-services
Separate disk for SysVol Database – you can use a separate Azure Disk for Sysvol Database. This disk can be created when you deploy the Azure VM. By default, data disks are attached to a VM using write-through caching. However, this form of caching can conflict with the requirements of AD DS. For this reason, set the Host Cache Preference setting on the data disk to None.
Deploy at least two VMs for ADDS. You can use Azure HA options such as Availability Zones or Availability Sets. We will discuss this further on scaling options.
Plan Your Network Architecture

Virtual Network and Subnet
You can consider placing the domain controllers in a separate subnet. From this, you can isolate that network through NSGs or firewalls. I prefer to keep the identity environment in a separate management VNET, where you can provide all other shared services. You can connect the other workloads and landing zones through peering.
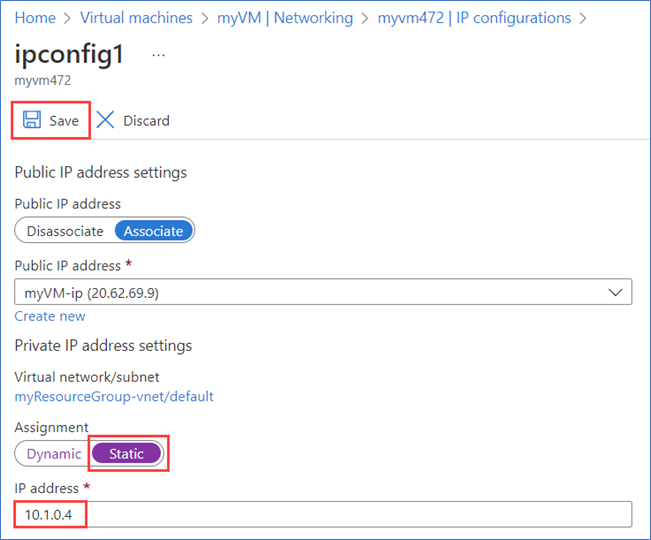
Static Private IP address
You can configure the VM network interface (NIC) for each AD DS server with a static private IP address for full domain name service (DNS) support.
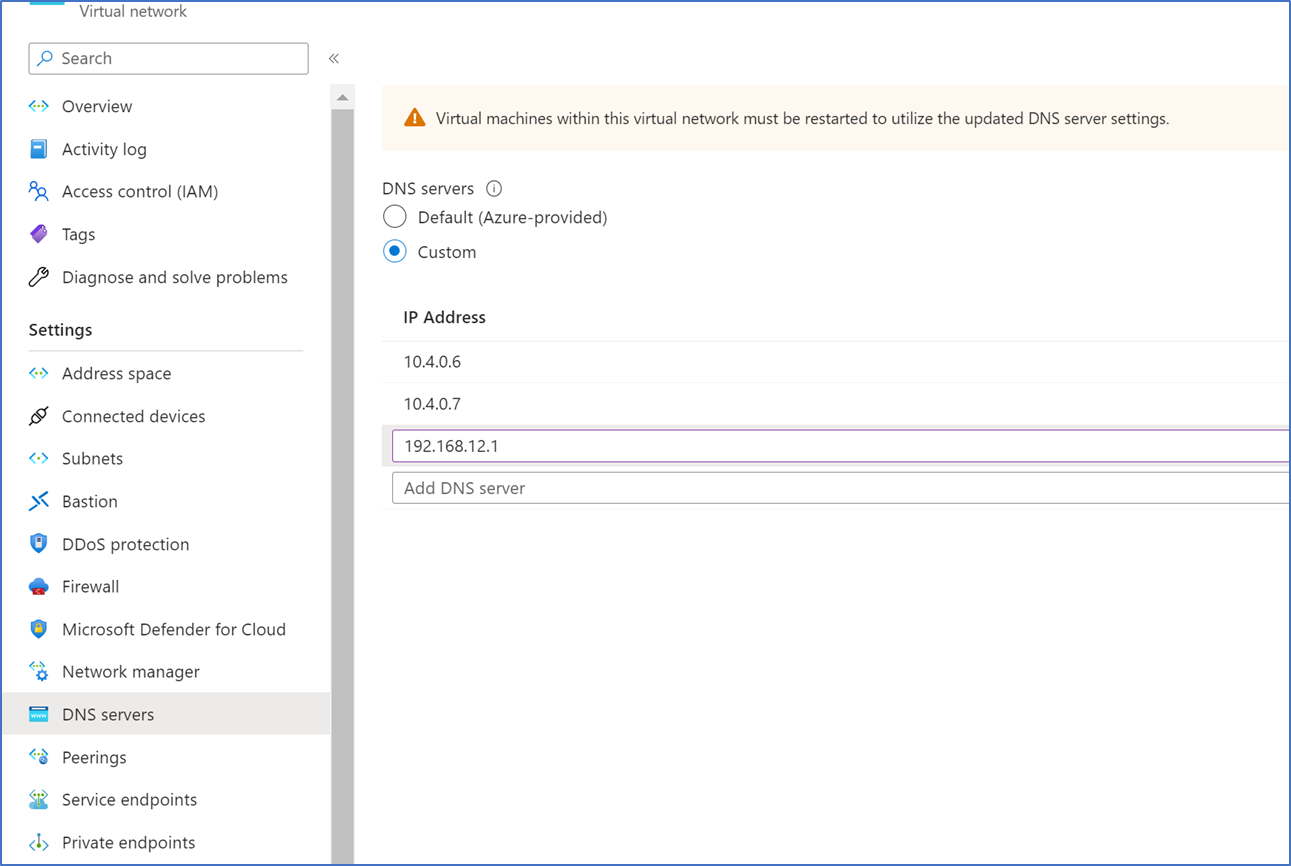
DNS
If you use Domain controllers as your DNS, you need to use custom DNS on ADDS-hosted VNET and all other peered VNETs. Add both domain controller IP address and any on-premises additional domain controller IP address.
Network security groups
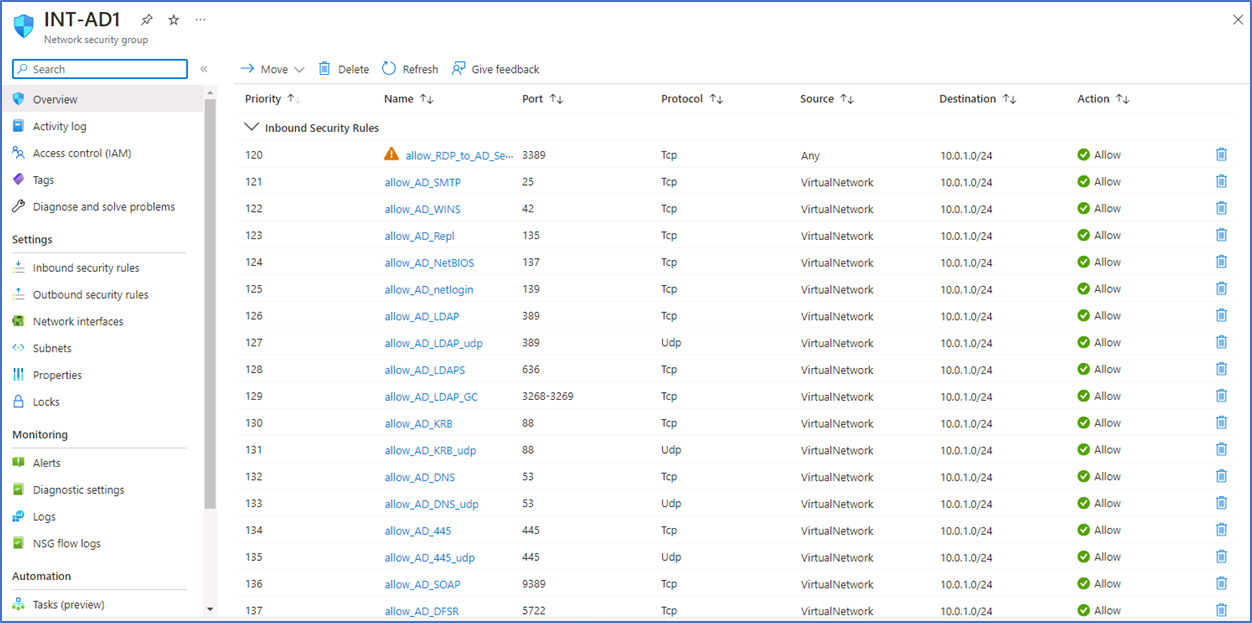
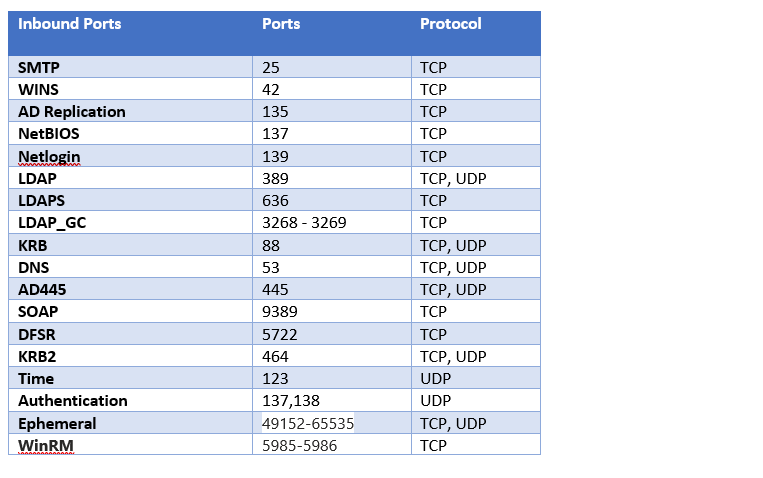
The Active Directory subnet NSG requires rules to permit incoming traffic from on-premises and outgoing traffic to on-premises. You need to add all the necessary ports by AD DS.
https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/config-firewall-for-ad-domains-and-trusts
Scalability considerations
Active Directory Domain Services has built-in high availability capability. It works as active load sharing with its additional domain controllers. If you want to scale up, you can deploy more domain controllers or size up the VM. You can use Azure Resize for VM size alterations.
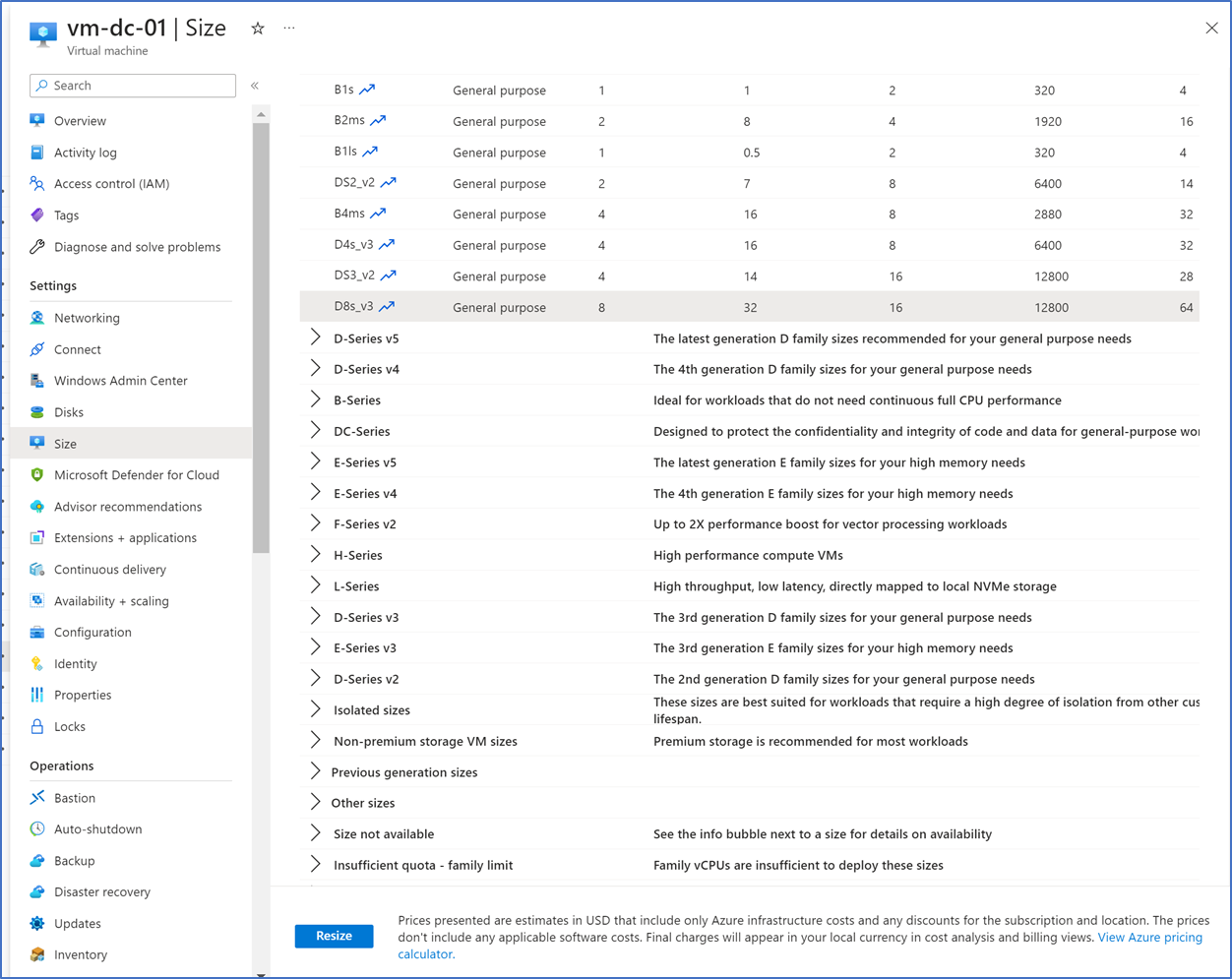
Availability Zones and Availability sets
Availability zones provide redundancy in an Azure region. It's a datacenter isolated logically and physically while connected to other zones within the region with a high-performance network with a round-trip latency of less than 2ms. Availability zones are not available in all regions. If it is available in your region, make sure to use it on your domain controllers.
Availability set is hardware in a datacenter that is divided into multiple update domains and fault domains. If you place your domain controllers in an availability set, hardware updates restart, or common failures such as power source or network switch defects will not have an impact on all your VMs. Always try to use this feature with your domain controllers.
Active Directory Best practices
AD site for Azure Network Range
You need to define a new AD site in AD DS and configure all the IP ranges in Azure to be part of that AD site. This will ensure that authentication requests generated from Azure VMs will go to DCs in Azure without going to on Prem.

Backup
Don't perform modern backup methods such as snapshots or copy VHDs for domain controllers in Azure. Perform regular system state backup and Azure Backup. Azure Backup is reliable, and you can schedule the backups.
Stop Deallocation
Don't stop or deallocate the domain controllers from the Azure portal. Restarting or stopping the VM from the portal can cause these issues. When you need to restart, always use the regular restart method from the VM.
- Resets the VM-GenerationID and the invocationID of the Active Directory repository.
- Discards the current Active Directory relative identifier (RID) pool
- Marks the sysvol folder as nonauthoritative
Implement Security Best Practices
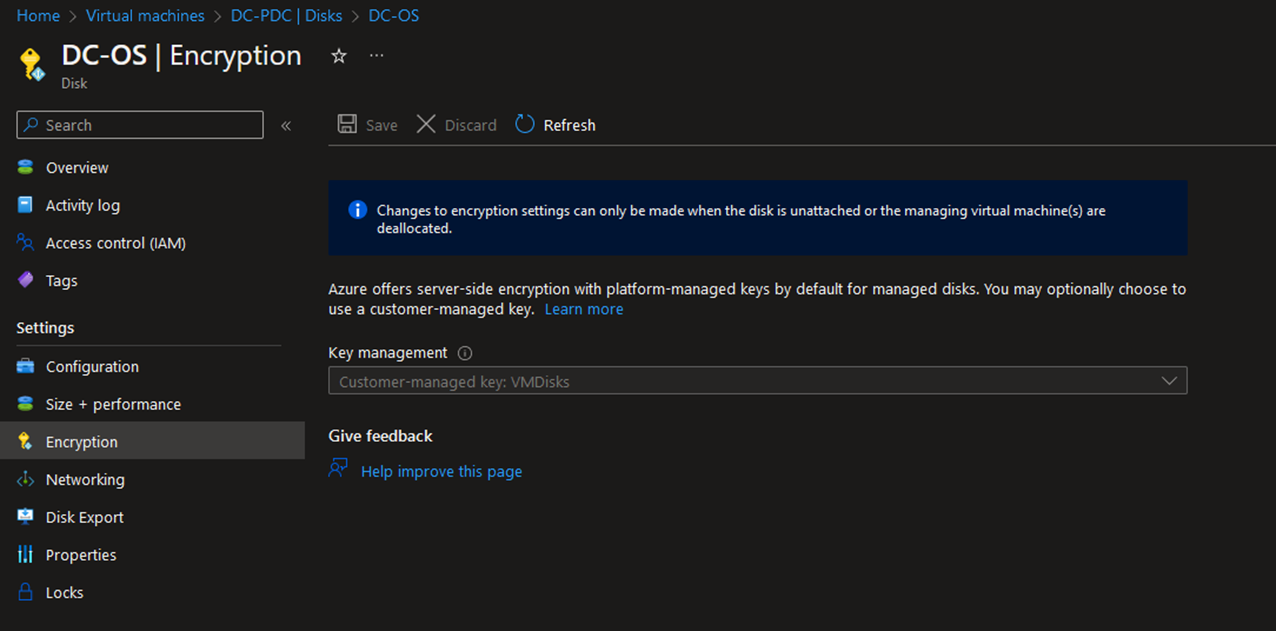
Azure Disk encryption – Always use Azure Disk encryption on your Domain controllers' OS Disk and SysVol Data disks.
For the Encryption key, you can use Azure managed or customer-managed key. If you are using the customer-managed key, first, you need to create a KeyVault and create a Key to use when disk encryption.
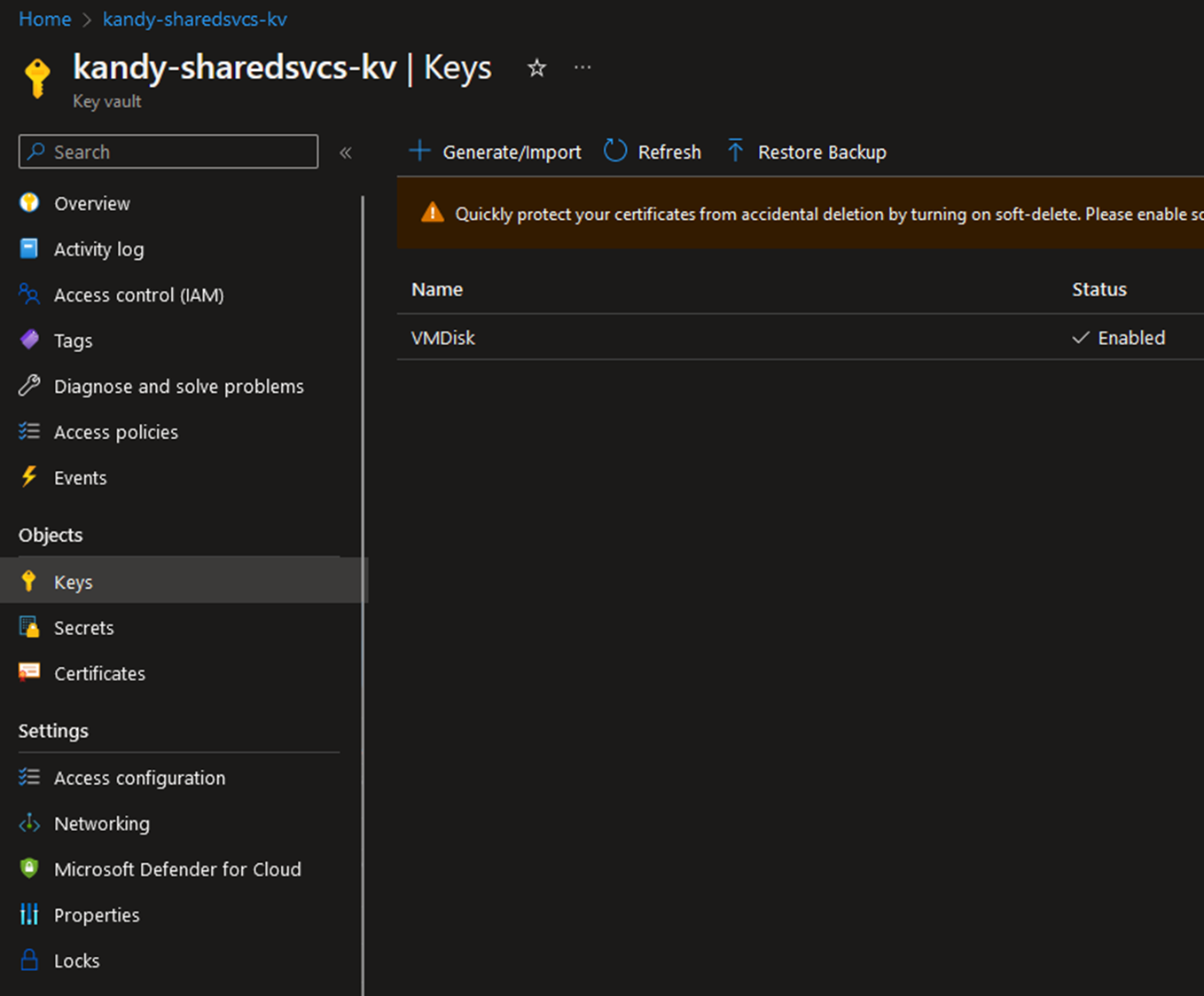
Make sure to encrypt both OS Disk and SysVol Disk using the key.
Use of Azure Firewall and NSG
Domain controllers need additional protection from your network, it is always recommended to use a separate subnet.
Step by Step on Deploying a Domain Controller in Azure.
- Log in to the Azure Portal, Virtual Machines, and Create new Virtual Machine
- Make sure to select Availability zone or Availability set.
- Select the Operating system and VM sizing for the Domain controllers.
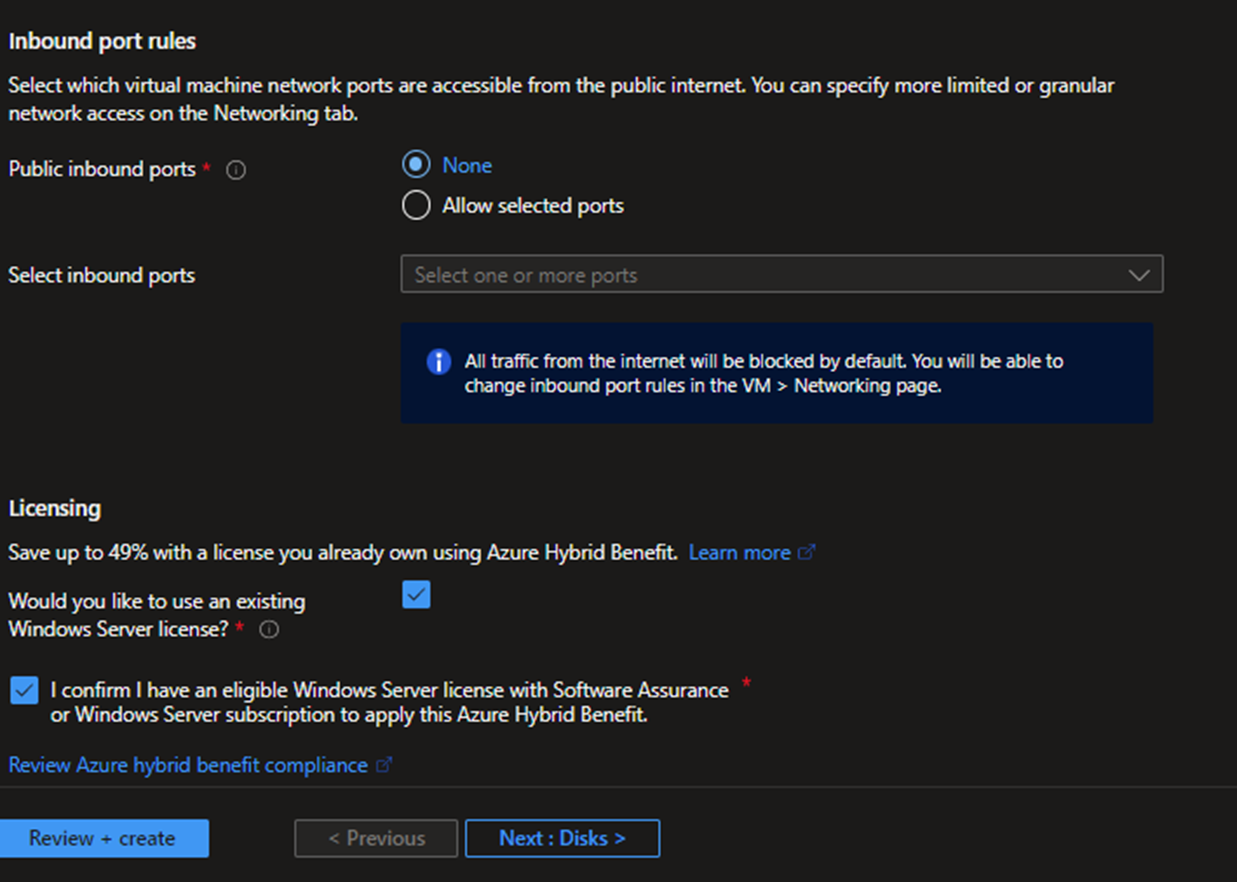
- Remove public access.
- You can select Premium or standard SSD as the OS disk. Premium has an SLA bound to the disk. Make sure to encrypt the OS disk using Platform managed key or Customer managed key. For customer-managed keys, you need to create a key vault and create a key before doing this. Since this is a domain controller, you can select customer-managed key.
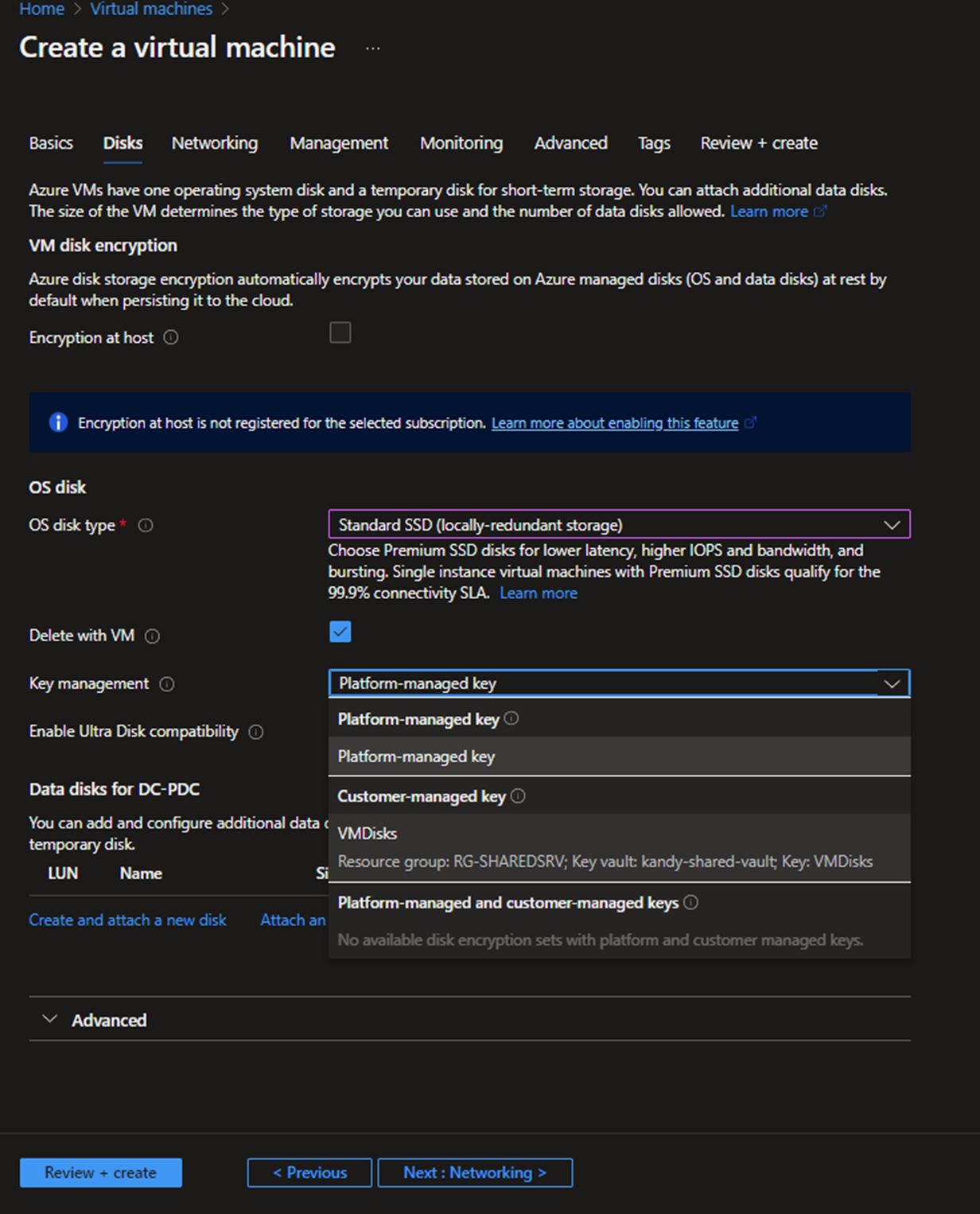
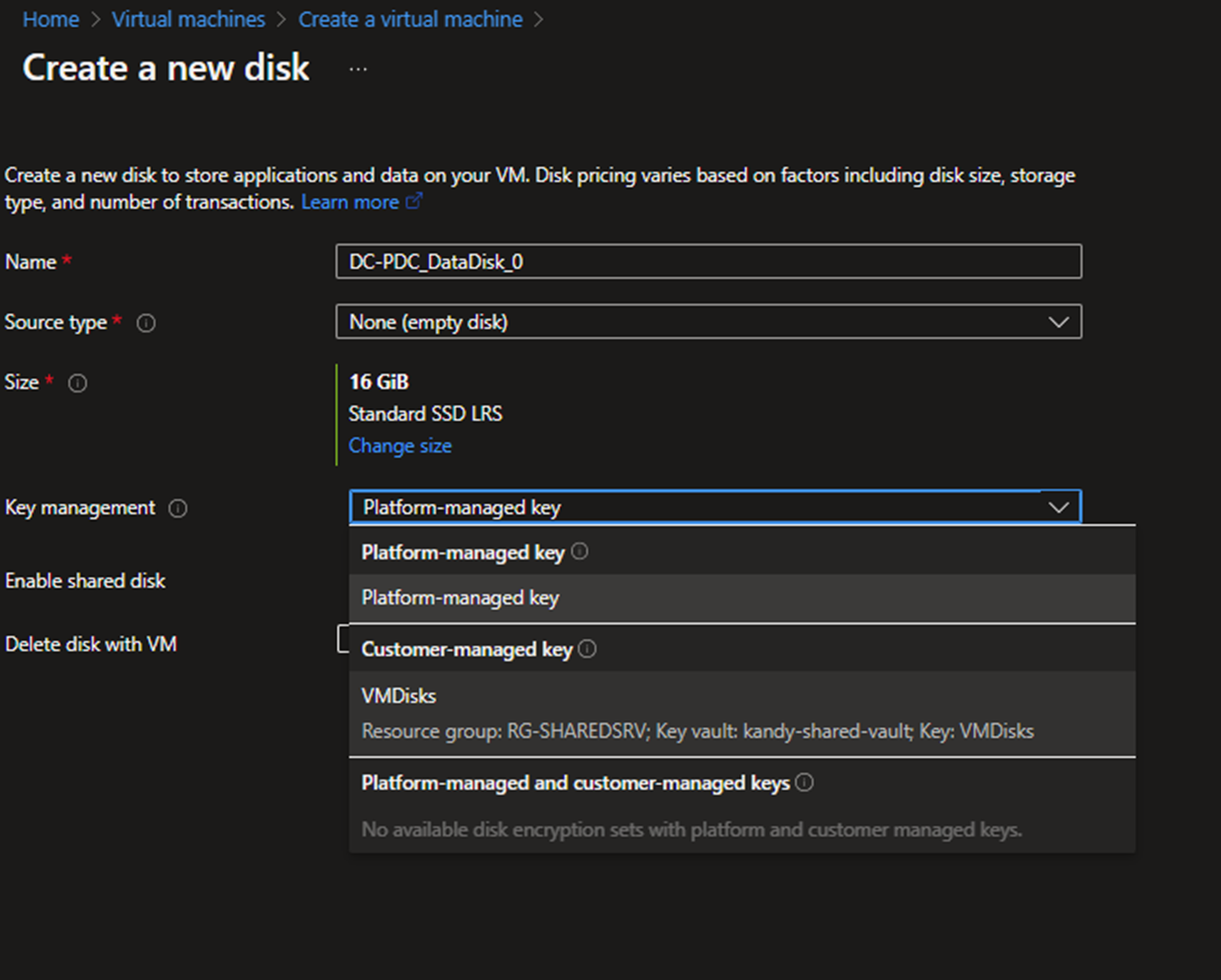
- Create another disk for sysvol directory, click Create, attach a new disk, and select the encryption key.
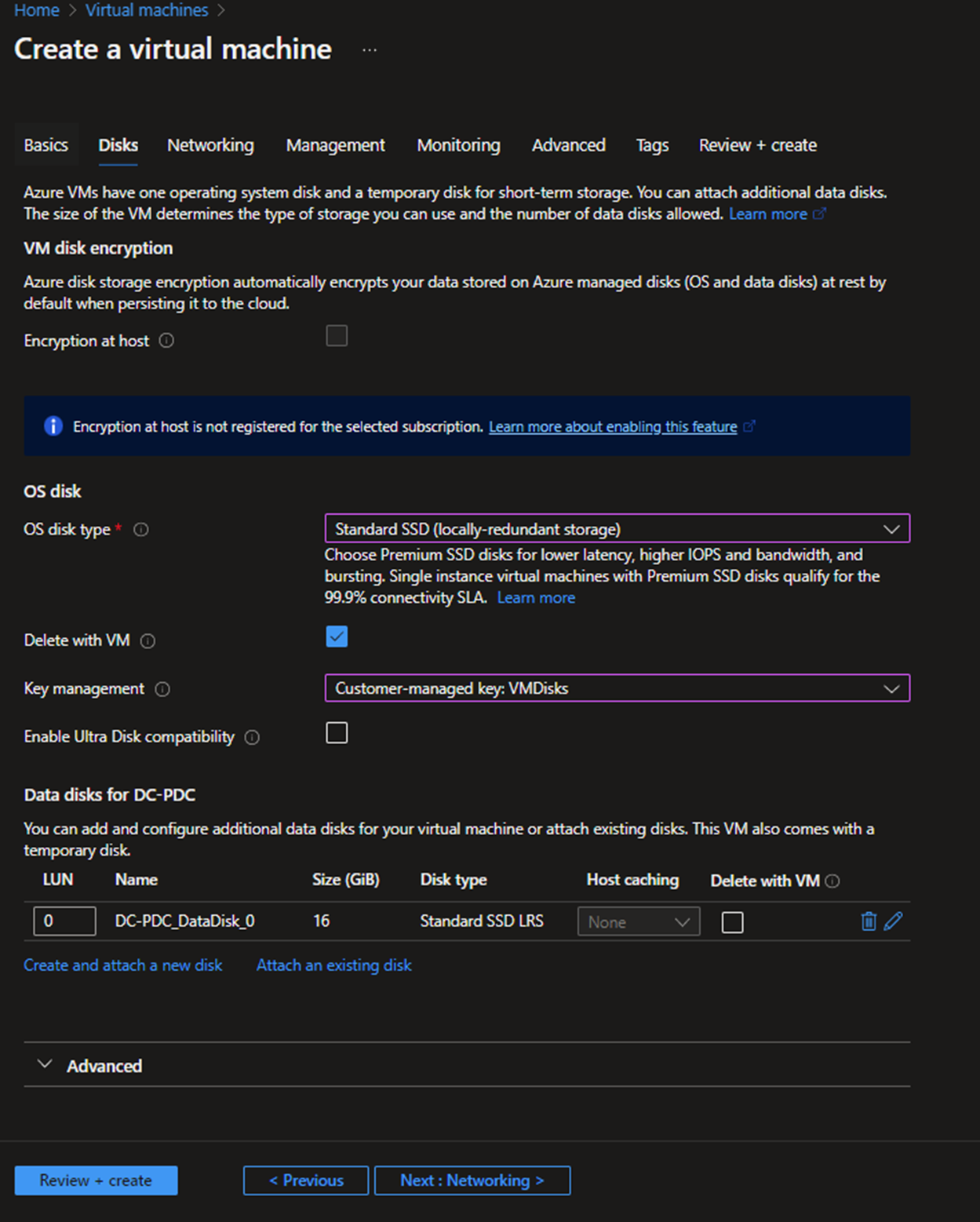
- Make sure you have configured host caching to none.
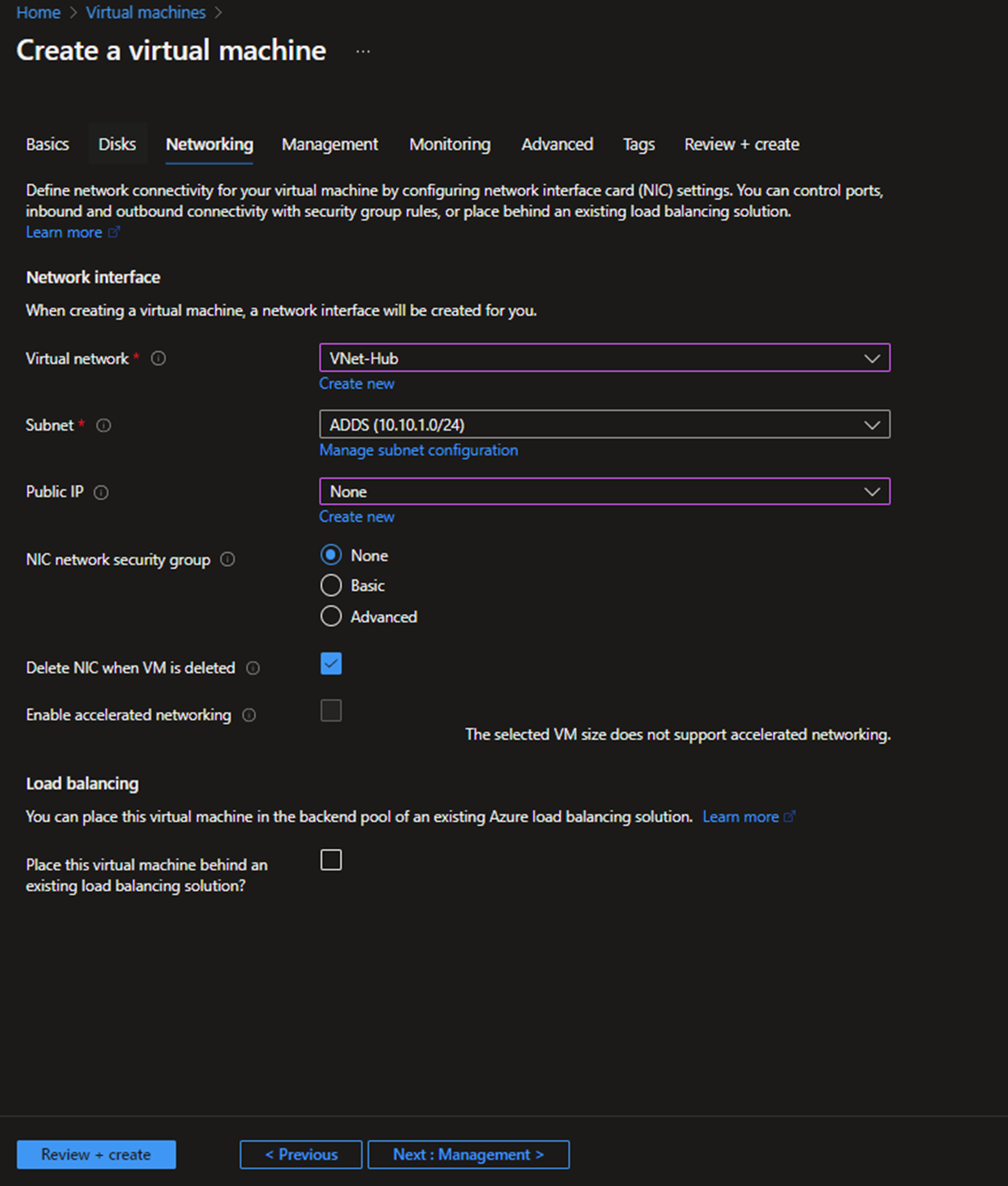
- Select the Virtual network and dedicated subnet for Domain controllers, and make sure not to add a public IP address. Also, you can avoid setting a Network security group for the NIC since we are deploying an NSG for the whole subnet.
- Configure the Tagging and create the VM.
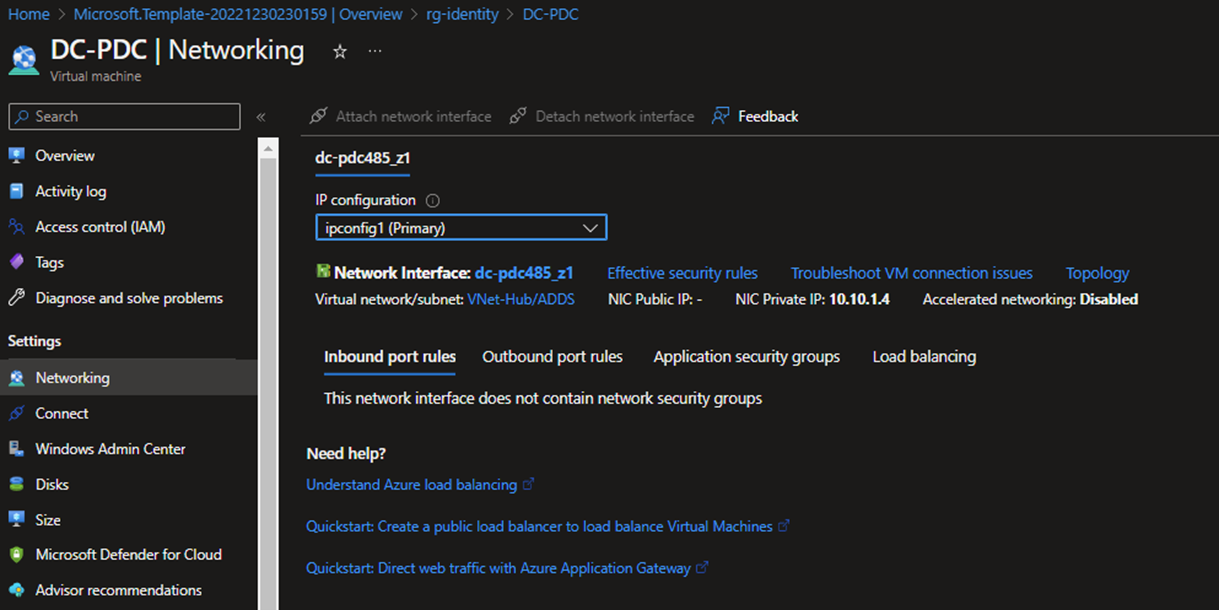
- After the VM is created, you can set up a static IP address for the internal IP of the DC. Go to the networking settings and click the Network interface.
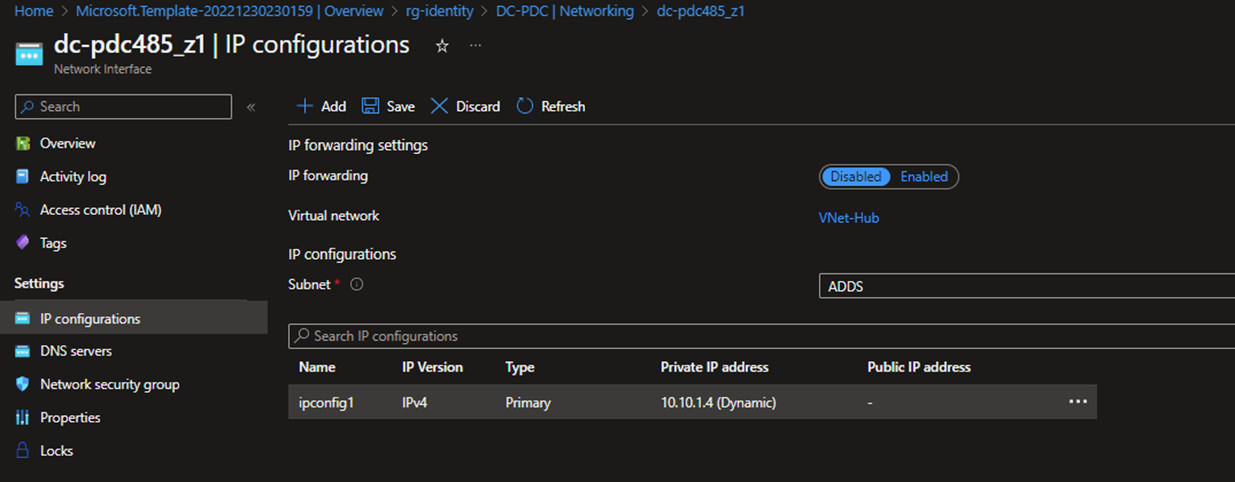
- Click IP configurations and click the Primary IP address (Dynamic)
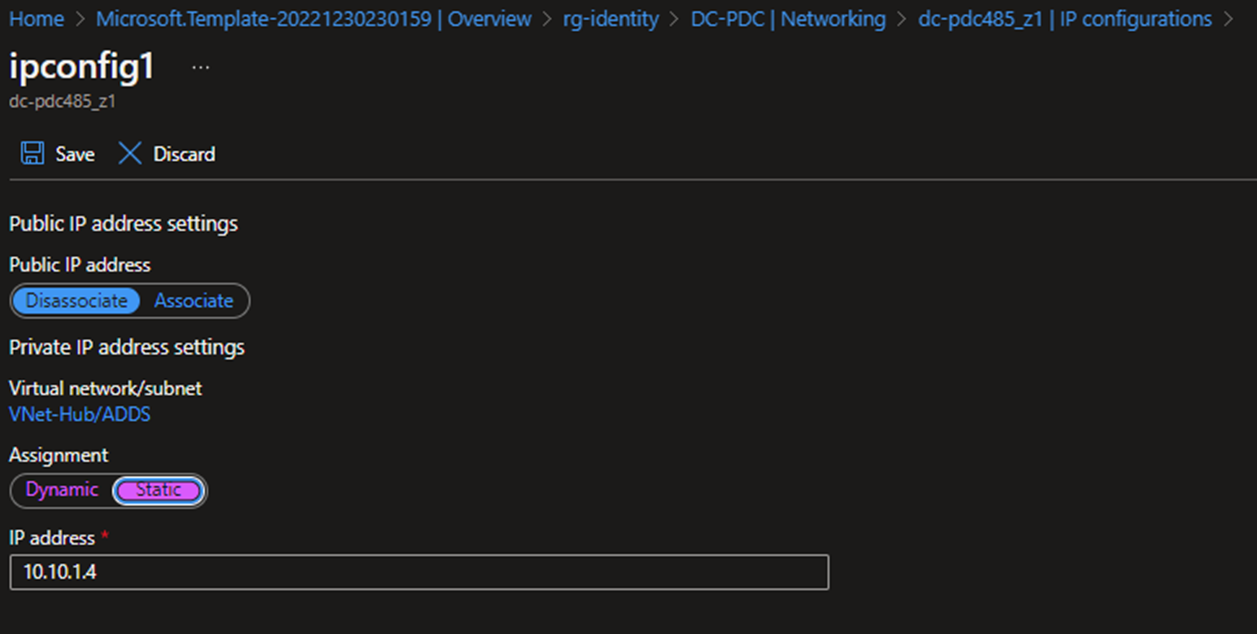
- Change it to Static and save.
- Next, you need to log in to the VM to initialize the disk for the sysvol, Disk management – create volume.
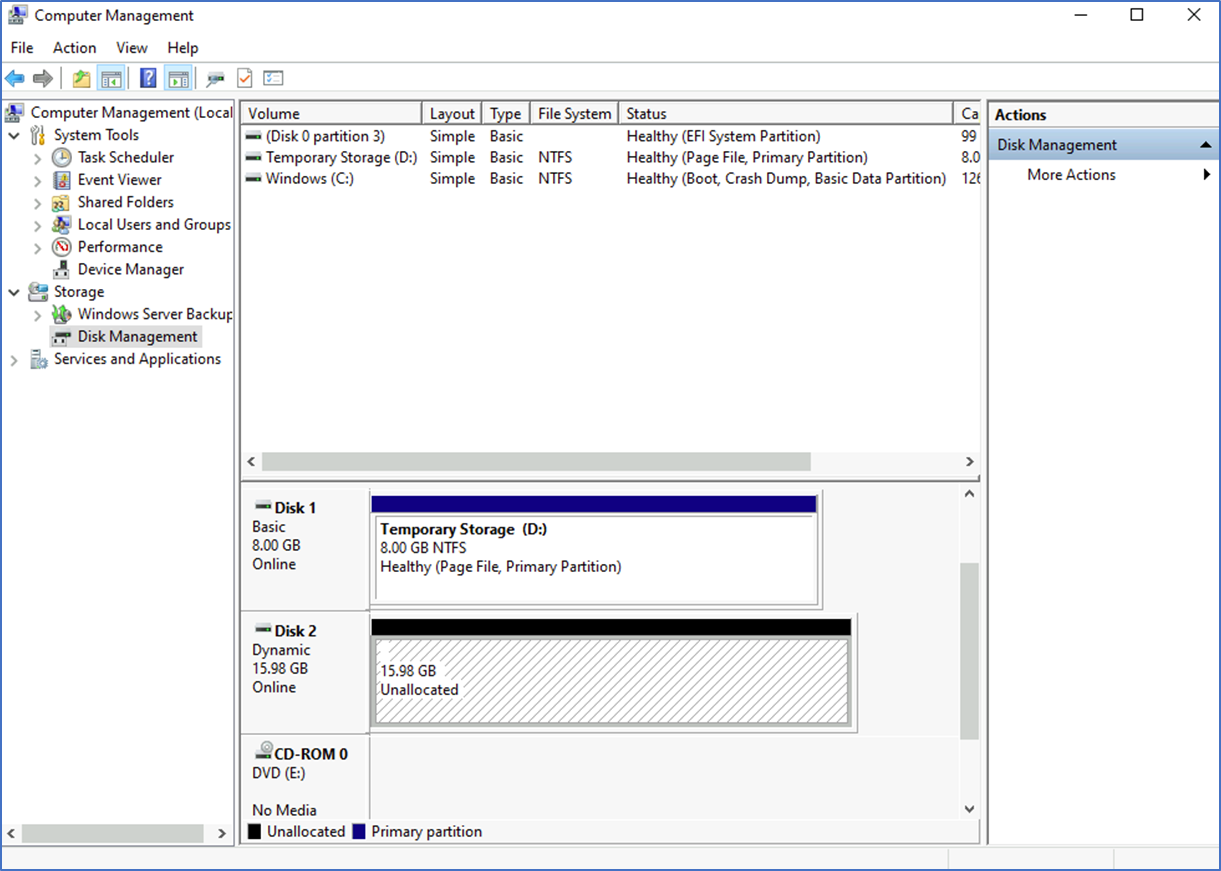
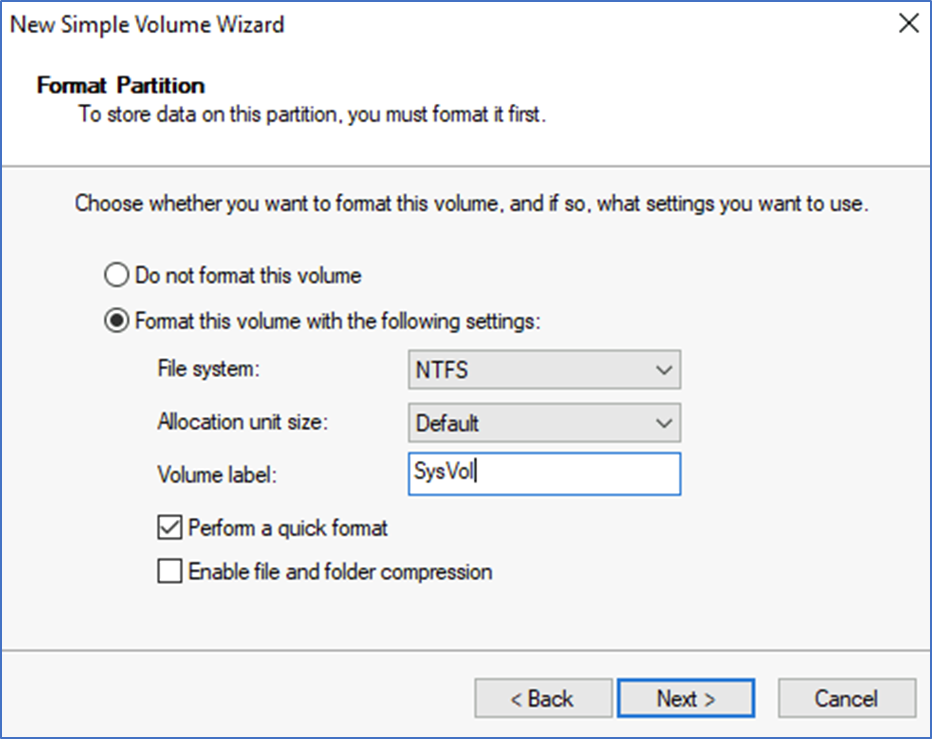
- When promoting the domain controller, don't forget to select this drive for the Sysvol.
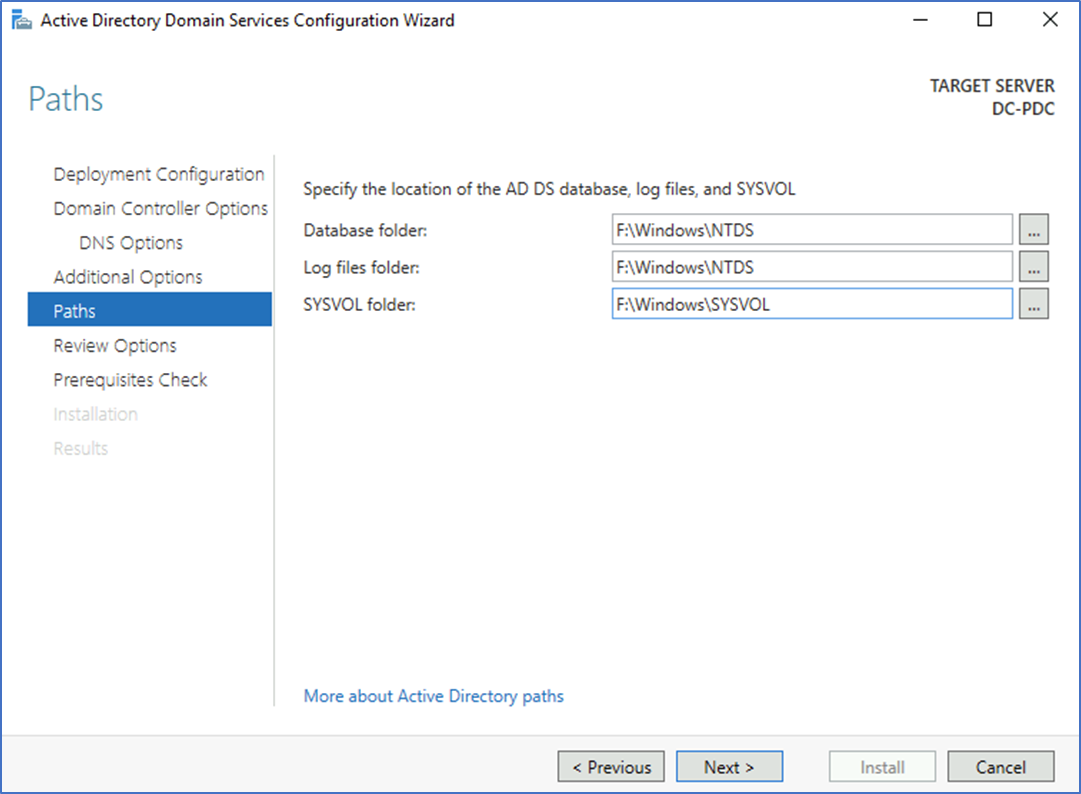
I'm not covering promoting the domain controller and configuring the AD site. After configuring the VM, you can follow the same steps to configure an additional domain controller on-prem.
I hope this post is helpful.
Thanks


























