What are workload identities?
Identity management is not limited to human users alone. In addition to human identities like employees, customers, and partners, there are non-human entities that also require identities to authenticate and gain access to resources. One prevalent category of such entities includes applications, services, and scripts. Workload identities are specifically created and assigned to these applications and services to regulate and maintain their access security. Within the Microsoft Entra framework, workload identities include both applications and service principles.
Why use workload identities?
One of the primary scenarios in which workload identities come into play is when you deploy applications or build Cloud services. These applications and services provide identities that enable them to access other resources. As the migration of workloads to the Cloud becomes increasingly prevalent, there is a significant increase in the demand for effective workload identity management. To address this heightened need for management, some organizations model their workloads as user identities and leverage the identity management solutions they have traditionally used for their human identities.
Challenges in securing workload identities
Securing workload identities presents unique challenges due to their differing characteristics and usage patterns compared to user identities. Traditional identity and access management capabilities designed for user identities do not readily extend to workload identities. This gives rise to several challenges in protecting workload identities. For instance, once a workload identity is created, there is limited visibility into its activity. This lack of visibility makes assessing the consequences of deactivating or removing that identity challenging, potentially resulting in the retention of redundant identities. Secondly, while most human users can reliably remember their passwords, applications, and services do not have such a capability. Since secrets for workload identity must be stored somewhere, there is a heightened risk of leaked credentials, consequently increasing the vulnerability to identity breaches. Also, the absence of robust access security features in existing solutions further compounds the challenge of securely managing workload identities. It becomes a daunting task to recognize which privileges are unnecessary and can potentially be revoked.
As organizations expand their footprint in the Cloud, the number of workload identities within their ecosystem continues to grow. Organizations often find themselves tasked with managing more applications and services than they have employees. According to Microsoft's internal research, organizations typically have five times more workloads than human users. That ratio will reach 1:20 in five years. Even within the Microsoft Entra ecosystem alone, the count of workload identities has surged, more than tripling in the past three years.
Many organizations have focused on enhancing the security of user accounts to defend against the rising tide of password spraying and phishing attacks. This proactive approach has involved the implementation of security measures like multi-factor authentication and the transition towards passwordless authentication. Even as user account security improves, recent cyberattacks have shown a shift in the attention of malicious actors towards workload identities. To address these evolving challenges, Microsoft has stepped up its efforts to enhance its capabilities for addressing this crucial area.
Microsoft Entra Workload Identities
Workload identity types have existed for a long time and continue to expand. Microsoft must secure these identities with a defense-in-depth approach. In pursuit of this objective, Microsoft has introduced the Microsoft Entra Workload Identities. Leveraging Entra workload identities, you can proactively detect the risk of compromise and improve the security posture of your workload identities, all conveniently managed through the new Microsoft Entra Admin Center.
Key capabilities of Microsoft Entra Workload Identities
Conditional Access
Conditional access represents one of the most powerful forms of access control. Microsoft has already introduced location-based policies, which allow you to specify trusted locations and then restrict sign-in access to those designated locations for one or more workload identities. Conditional access blocks any sign-in attempts from locations outside these trusted boundaries. Furthermore, sign-ins that target Microsoft Graph are now inherently protected by continuous access evaluation, promptly reinforcing these location-based controls. Conditional access extends its support to risk-based policies for workload identities and allows you to restrict access when identity protection raises concerns about risks.
Identity Protection
The workload identity lifecycle is less defined and can be challenging to manage. Identifying risk indicators within this context involves an examination of the entire identity lifecycle. This entails a search for signs such as compromised credentials, unusual sign-in activities, and unauthorized changes to the account.
Access Review
Another critical aspect of the defense-in-depth strategy is attestation, the process of reviewing, confirming, or revoking access to enforce the zero-trust principle of least privilege. Through access reviews within privileged identity management, you can assign the responsibility of conducting reviews to the right individuals.
App Management Policies
Strengthening the security of application credentials is a crucial aspect of workload identity security. This involves shifting from using secrets to certificates or long-lived credentials to those that undergo frequent rotation. Although Microsoft recommends using managed identity for all application scenarios, there may be instances where you need to manage credentials for applications on your own. Application management policies provide the means to mitigate the risk of credential compromise. Through these policies, you can define the types of credentials allowed for new and existing applications within your organization.
Creating a new policy
To create a new policy in the Microsoft Entra Admin Center, navigate to the Conditional Access blade, select New Policy, and assign it a name.
Under Assignments in the drop-down box, select Workload Identities, and decide whether this policy should be applied to all of your line of business applications or just a specific subset. If you select the latter, you can search for a particular application and target it exclusively. However, for a more comprehensive approach that enhances security across all applications, it's advisable to apply this policy to all apps.
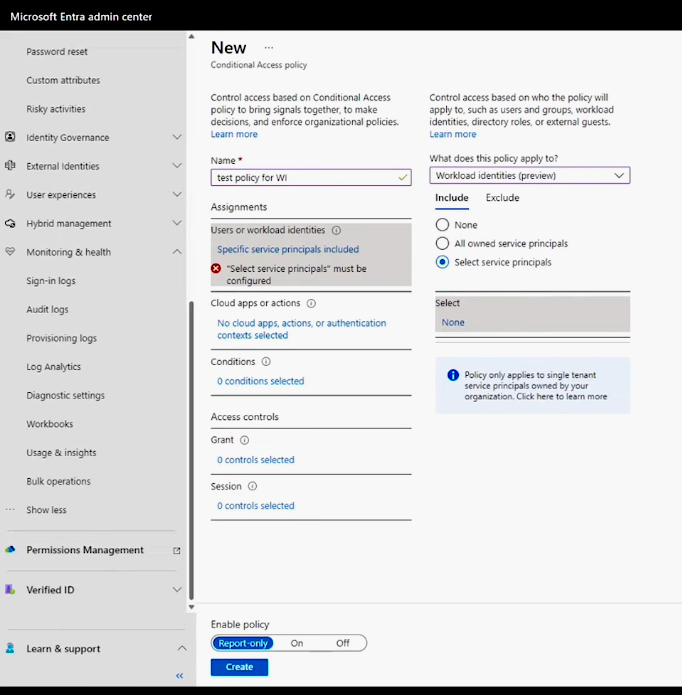
Under Cloud apps, select All Cloud apps. Next, focus on the Conditions section, where automation becomes pivotal. Here, you can configure a policy to automatically block access whenever the system detects deviations from the expected norm. You can create a risk-based policy by selecting Service Principal Risk and selecting which level of risk should trigger a block control. Choose any combination of high, medium, and low.
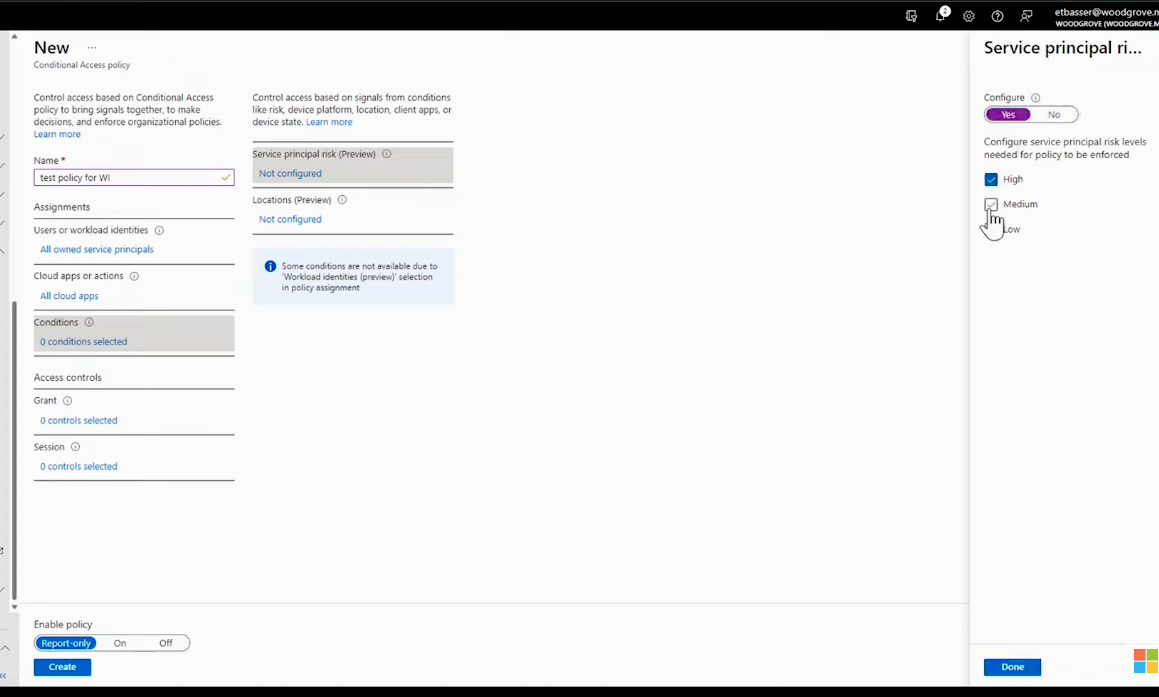
Another option is to create a location-based policy for workload identities. Creating a distinct policy specifically for blocking access from locations outside of trusted ones is recommended. To do this, initiate the process by configuring the trusted locations for the data center where you host the particular application.
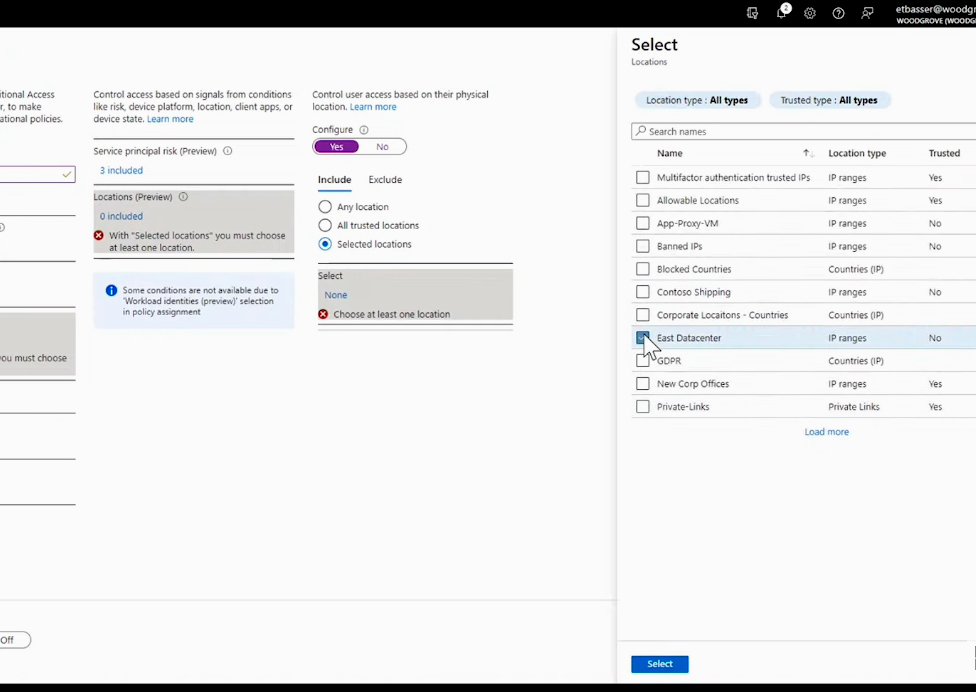
Under Grant controls, select Block access, and create your policy. The Report-only default lets you put the policy in a silent mode that will log the activity without blocking access.
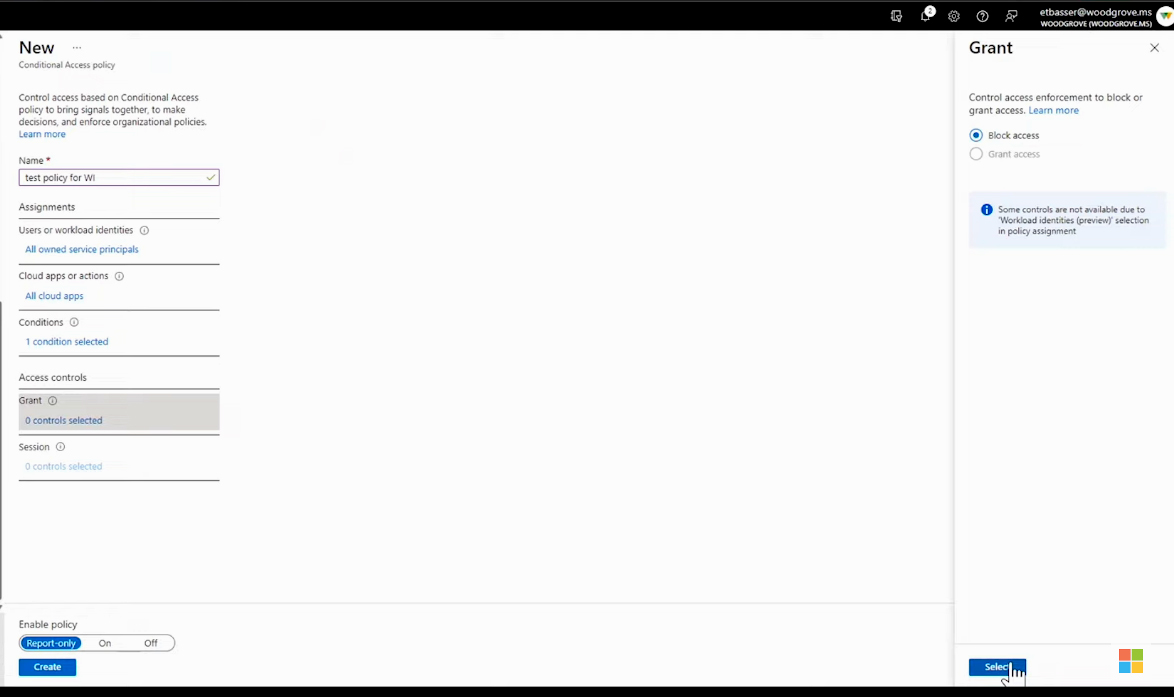
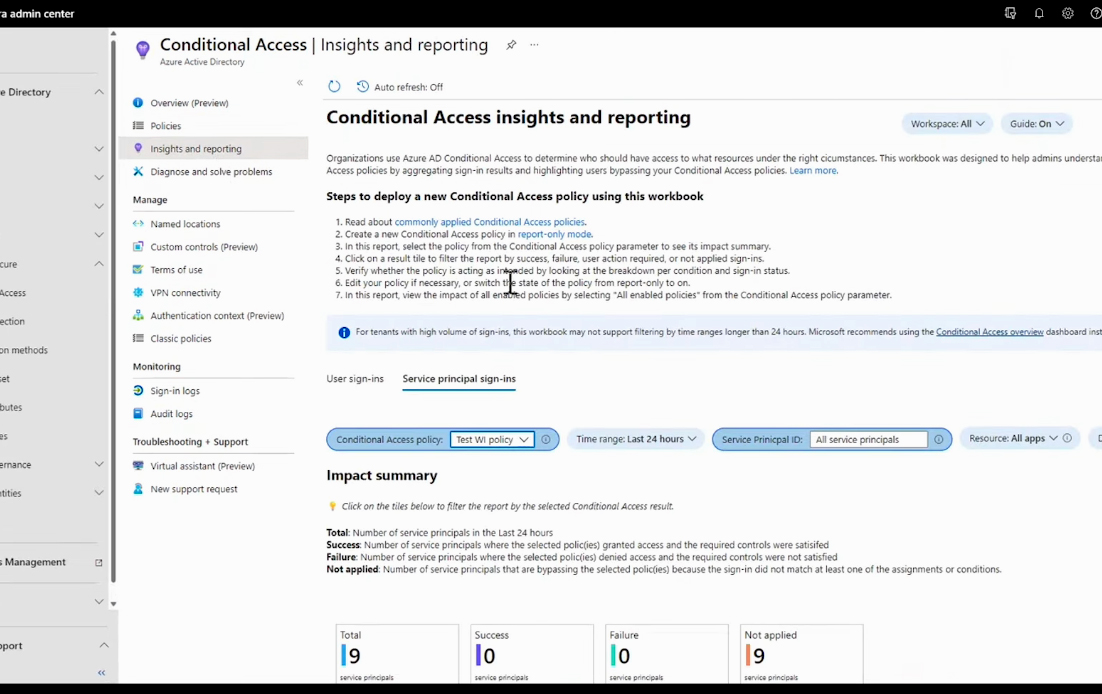
During that piloting phase, the Conditional Access - Insights and reporting will give you a more holistic view. It will show you which workload identities would have signed in, which ones your policies would have blocked, and which ones were out-of-scope.
Let's see how to find workload identities at risk with identity protection to help you identify workload identities that need to be prioritized for access control. Starting from the security blade, navigate to Identity Protection. A new feature called Risky Workload Identities is accessible through a single dashboard. This dashboard shows applications or services flagged for risk by identity protection. Within this blade, you can click on any row to access additional information about the associated workload identity. Much like the approach for managing risky users, you can take immediate actions, such as confirming or dismissing the risk. Alternatively, you can explore more details by selecting options like risk detections, audit logs, or sign-ins.
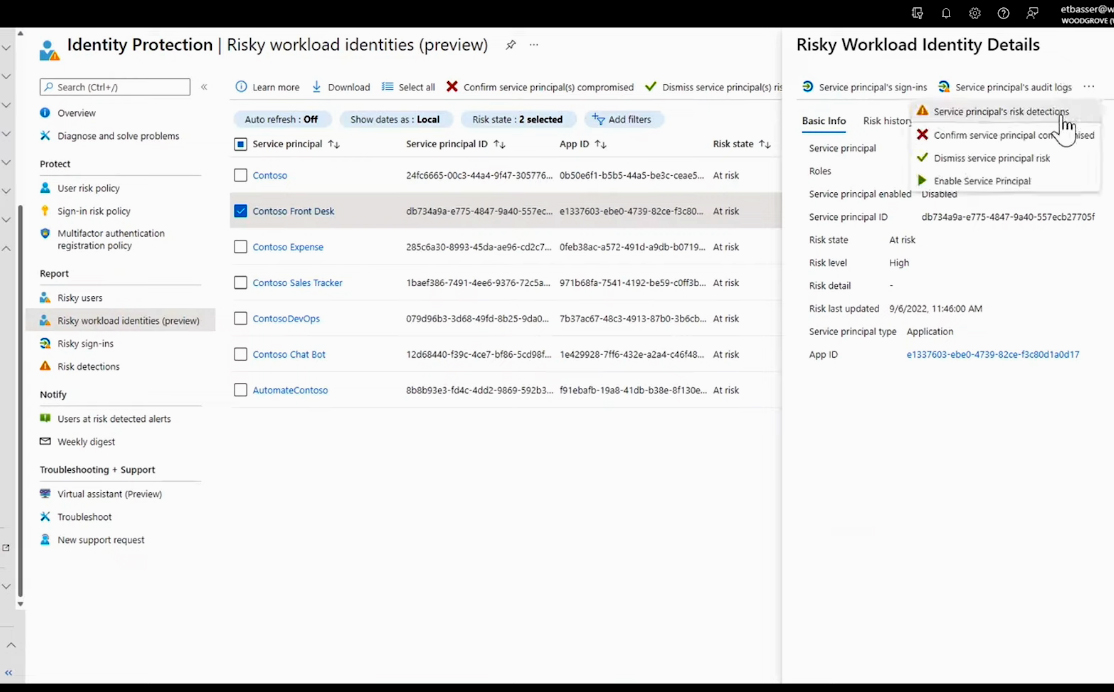
Navigate down to the Risk detections blade and select Workload identity detections. There, you can get more specific information about the detected risk, including when it was detected, the detection type, and the risk level. If you click here for more information, you can view the repository to see the credentials and who worked on this.

With risk monitoring and access controls in operation, the next step is to review the workload identities that possess access to privileged roles.
In the Identity Governance blade, under Privileged Identity Management, select Azure AD roles, and then Access reviews under the Manage menu.
Then select New, enter a Review name, Description, and set the Frequency of the review based on what's suitable for your team. You can set it for only once, but a recurring review is recommended.
Then select Scope for service principles. Under Role, select the privileged roles you want to review. This way, the review will capture any workload identity in your organization with these roles.

How do organizations utilize Microsoft Entra Workload Identities?
Microsoft Entra Workload Identities offer extensive functionality for protecting and managing workload identities and their access. Today, one of the organizations' most popular features is risk-based conditional access for workload identities. This empowers organizations with identity protection capabilities integrated into their workload identities, effectively protecting against common attacks by using machine learning and insights derived from the broader Microsoft ecosystem. Even in cases where a workload identity is compromised, leaked by accident, or subjected to a data breach, Microsoft Entra Workload Identities can protect against its misuse. Beyond proactive protection, Entra Workload Identities also provide reactive protection. All activities involving usage, creation, modification, and deletion are locked and can be exported to an SIEM system, such as Microsoft Sentinel.
Resources:
What are workload identities?
Microsoft Entra Admin Center
Reference:
Microsoft Ignite Sessions









