
AVD is the Microsoft VDI solution that has global Microsoft managed PAAS components such as Remote gateway, Web Access, and Broker services. Now, you can use Azure private links to connect to these remote resources privately and securely. With private endpoints, you no longer expose your services to the public internet. Using Microsoft's backbone, session hosts will connect to the PAAS components by internal IP addresses. Also, if required, you can configure clients to connect only through the Site-to-site VPN or Express route.
This is a two-part article series, and from this first article, I will configure private endpoints for the session host to the Microsoft AVD control plan and make that connectivity private.
Private links architecture for AVD control plane
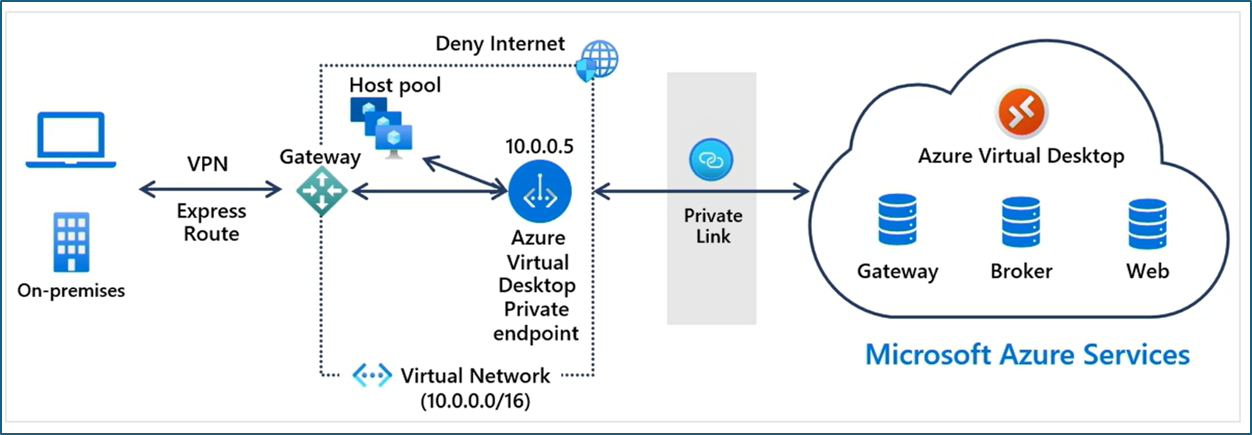
AVD is a half PAAS solution, meaning Microsoft maintains VDI components such as Gateway, Broker, and Web services. Since these services are hosted in Microsoft's internal network, we had to connect to these services through the public internet. However, with the latest introduction of private links for AVD, we can now connect to these services through private endpoints. There are three corresponding resources we can configure with private endpoints.
Initial feed discovery - This is the end user's client device identification of the AVD feed URL - https://rdweb.wvd.microsoft.com/api/arm/feeddiscovery. Through private network.
- One private link for AVD deployment
Feed Download – AVD client downloading user application group resources
- One private link per workspace
Connection to host pools – Configuring the connectivity between session hosts and AVD control plane traffic through private networks.
- One private link per host pool
You don't need to configure all the private endpoints mentioned above. You can decide what components need to be enabled for internal network connectivity according to your requirements. For example, if your users need to connect from the public internet, but you want to secure session hosts to Microsoft-managed AVD components, you can only Implement Private endpoints for Connections to host pools.
Here are the supported scenarios.
- Both clients and session host VMs use private routes.
- Clients use public routes, while session host VMs use private routes.
- Both clients and session host VMs use public routes. A private link isn't used.
Prerequisites to configure Private Links for AVD
- Existing AVD environment with Host pools, Application groups, and workspace
- You can use the same subnet or specific subnet to place Private endpoints.
- Azure RBAC permissions to deploy Private endpoints.
- DNS for Private Endpoints.
- If you use ADDS for DNS, you must create a forward lookup zone in the Active directory for Private endpoint DNS resolution. I'm going to use this option.
- Azure DNS Private Resolver can be used for DNS resolution
- Enable AVD Private link for subscription – Preview features
Enable Private links for AVD
You need to enable this from the subscription level. Navigate to Subscription – Preview features – search for Azure Virtual Desktop Private link - Register

Configure Private Endpoint for Host Pools
- Log in to Azure portal – AVD Host pool – Networking, and you will see new options to control network traffic to the AVD Host pool. If these options are not visible, you need to reconfigure the registration.
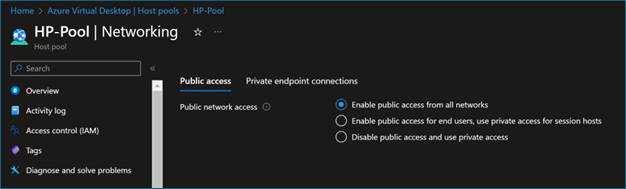
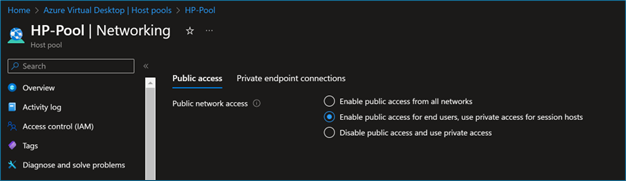
- You can configure the public access according to your requirements; I'm configuring end users to connect from the public internet, but Session hosts and AVD control panel will connect through Microsoft backbone using Private links.
So I'm selecting the second option – Enable public access for end users, use private access for session hosts.
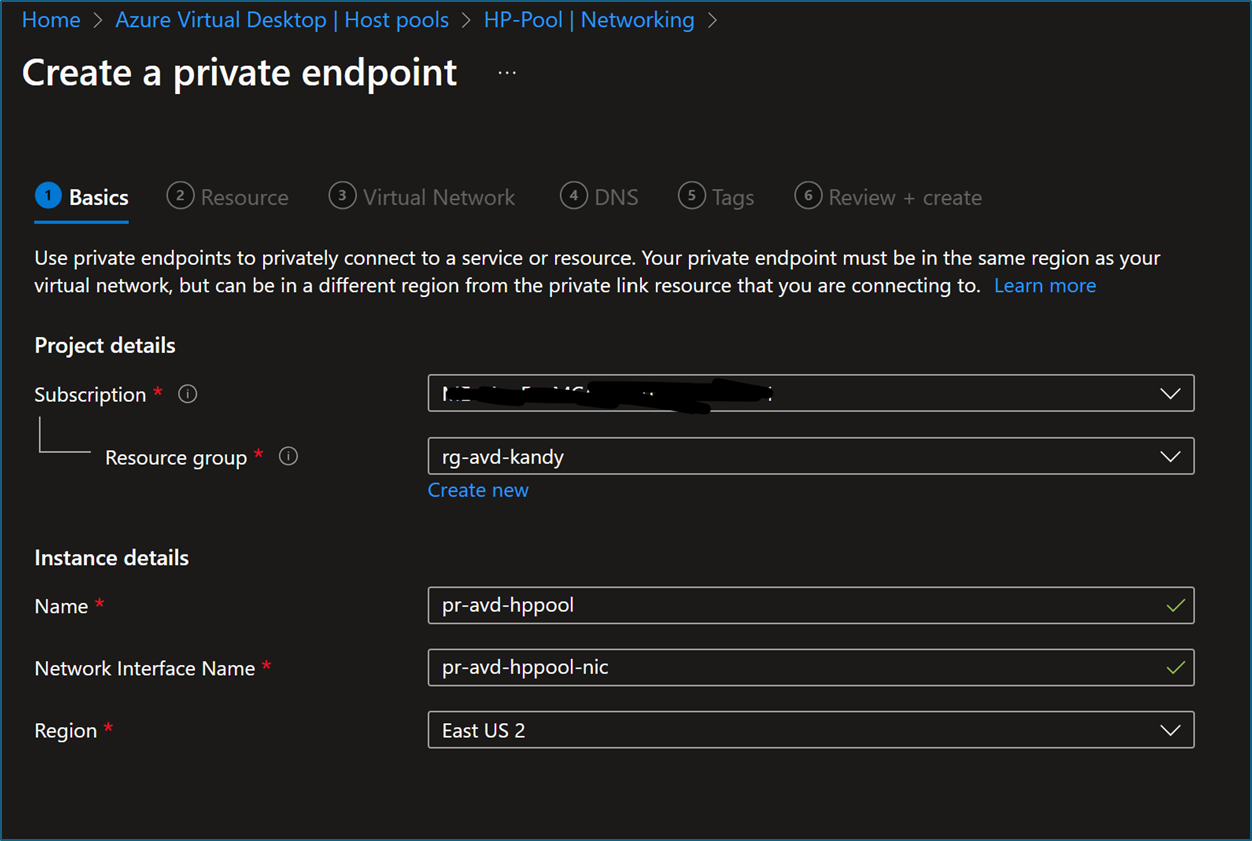
- Next, you need to create a private endpoint. To do so, click Private endpoint connections and create a New Private endpoint.

- Fill in the RG, Name, and Region

- Next, select the subnet that you want to place the Private endpoint. You can have a dedicated if you wish.
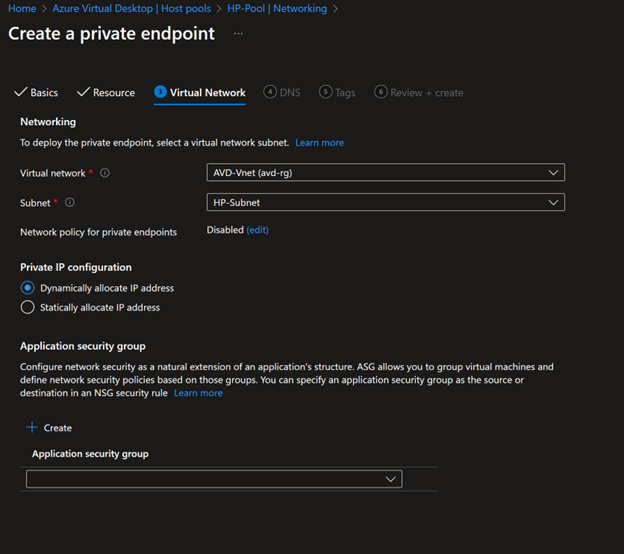
- Next, you need to select the DNS. You can use Private DNS Zone; I'm using the on-premise Active directory as my DNS server, so I'm not integrating with private DNS Zone.
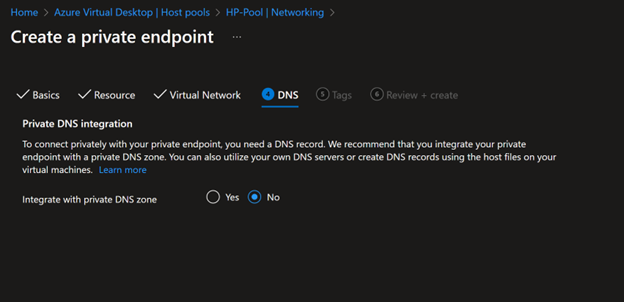
- Click next and review and create.
DNS forward lookup zone
This step is required if you use on-premise DNS as your primary DNS service in Azure and AVD session hosts.
- Login to the ADDS domain controller
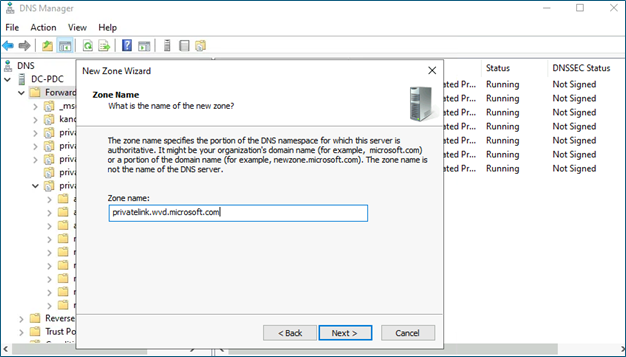
- Go to DNS – Forward lookup zone – Create new zone
- Name the zone as – Privatelink.wvd.microsoft.com
- Next, you need to create all the A records for the private endpoint. To get the internal IP address and FQDL, find the newly created private endpoint and click DNS configuration
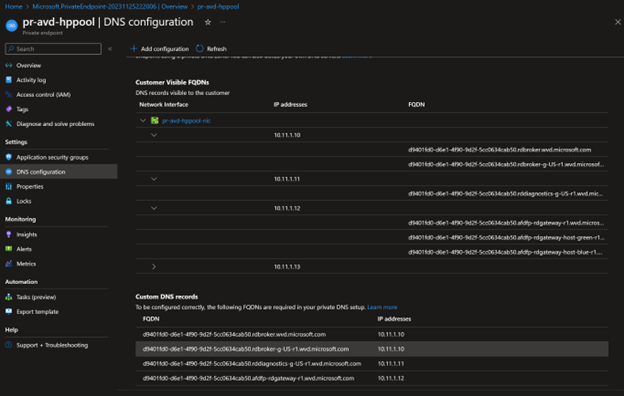
- Create all the DNS entries individually in the ADDS DNS forward lookup zone.
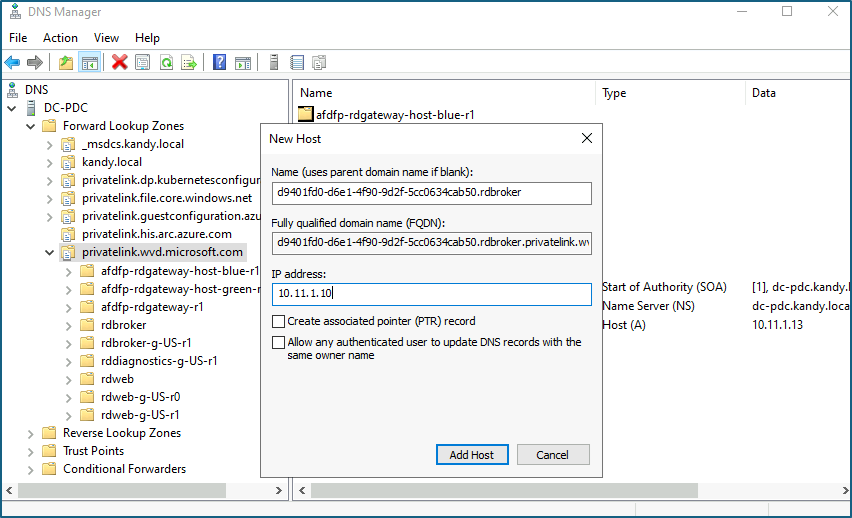
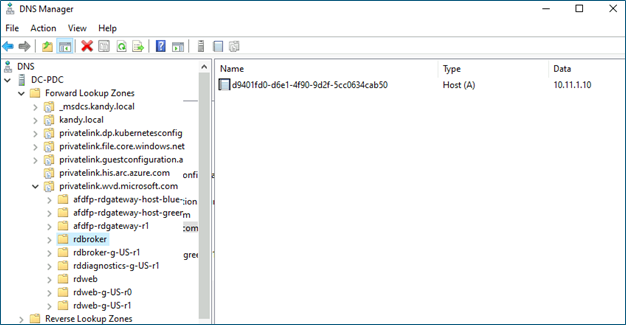
- After configuring the DNS, make sure to restart the Session host VMs. Once you have configured everything, you will see VMs connecting to the AVD PAAS service through private links.

- If you want to confirm the connection is not from public access, you can create an NSG and add an outbound rule to block all public access to the AVD control plan and see if it's connecting. Use WindowsVirtualDesktop service tag.
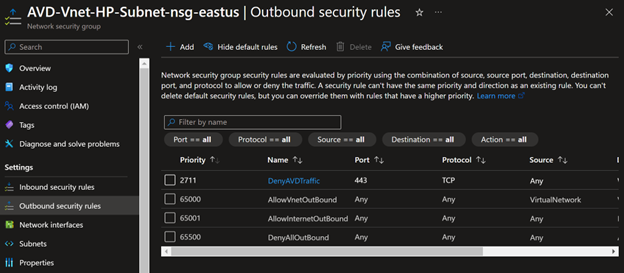
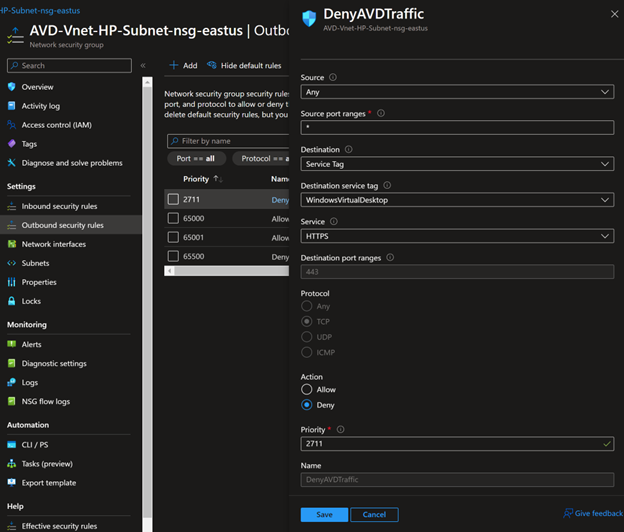
If all works fine, your session hosts will connect to managed services using a private IP address, and now it's not a requirement to enable outbound internet to Microsoft managed services. In my next post - Configuring Private Links for Azure Virtual Desktop – Part 2 Private Endpoints for Feed Discovery and Download, let's discuss how to make Feed Discovery and Feed Download work through private networks.
I hope this post is helpful.

















