
At its core, Zero Trust is a simple strategy for protecting critical business assets regardless of their location. The approach has evolved beyond securing elements just on the corporate network. In essence, Zero Trust focuses on protecting assets wherever they exist.
The guiding principles of Zero Trust
Zero Trust is built upon three foundational principles: assume breach, verify explicitly, and use least privileged access.
Assume breach
Assume breach marks a significant shift in mindset from traditional security perspectives. It involves operating under the assumption that an attacker will compromise an account, identity, endpoint, application, or API. Then, protective measures are implemented for all assets accordingly. The key aspect of an assume breach lies in its transformative effect on security thinking, moving away from the conventional inside-outside paradigm to adopt an approach similar to an attack chain or security graph. This perspective assumes that attackers navigate various control relationships within the environment to reach their targeted assets.
Verify explicitly
Verify explicitly rejects the assumption of trust and demands the explicit verification of trust. This approach focuses on the attack surface to defend any entity against potential attacks.
Use least privileged access
The application of least privileged access aims to limit the blast radius. If one of those entities, identities, or endpoints is compromised, the objective is to restrict the extent of damage they can do. The blast radius can be limited through factors such as time constraints and specific permissions.
Zero Trust Transformation
Zero Trust represents a fundamental and end-to-end transformation. It starts with identity and network access control, but the forces driving the modernization of access controls extend to the Cloud as attackers navigate their way into networks. These same forces also drive transformations in security operations, demanding the ability to detect threats within and outside the environment. The impact of Zero Trust extends to various domains, including infrastructure and development security, data security, IoT and OT security, and governance. Zero Trust spans across your entire program and technical stack.
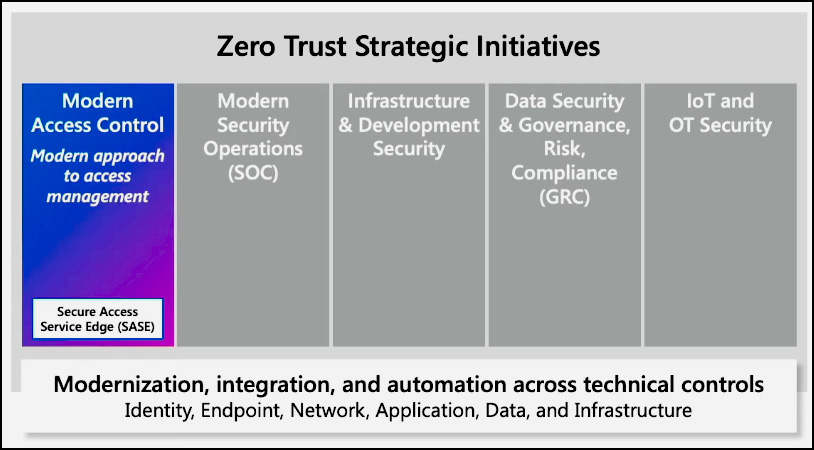
The adoption of a Zero Trust approach proves advantageous in three specific scenarios: supporting remote and hybrid work, identifying and protecting sensitive business data, and building confidence in security posture and program.
Secure remote and hybrid work
Zero Trust extends beyond being a mere security mandate; it functions as an enabler for your business. In the current business environment, employees seek flexibility, desiring to work from any location, at any time, and on any device. For security professionals, this translates into the need to address many scenarios and secure them effectively. The increasing sophistication and multifaceted nature of cyber-attacks add another layer of complexity. Further, securing all identities within your environment is crucial—be it employees accessing resources, collaborating with business partners, vendors accessing resources, or managing non-human identities.
New user onboarding
In a secure remote and hybrid work plan, the first focus is securing new users' onboarding process. Explicitly verifying these users before onboarding onto the account is crucial. This process differs among organizations, with each having a different identity verification and onboarding workflow. Some organizations rely on reporting managers to provide the username and a temporary password. However, considering the evolving landscape without passwords, alternative methods need exploration. Once the user is verified, the next step involves assisting them in setting up secure and robust credentials. Not all credentials hold the same level of strength, and more robust options such as FIDO security keys, Windows Hello for Business, and Microsoft Authenticator need to be adopted. Finally, it's important to guide the users in configuring their devices to align with the organization's policies. While users may typically have company-issued devices during onboarding, there are instances in the remote work scenario where the devices may not reach the users in time, requiring them to use their own devices. Options include the users enrolling their devices with the company or utilizing a virtual desktop to access applications.
Seamless access
As users engage with a wide range of applications to fulfill their tasks, the aim is to streamline their experience. To prevent users from remembering multiple credentials or the need to input credentials for each application, it is advisable to invest in a centralized identity provider and set up single sign-on capabilities for all applications in the environment, including on-premises apps. The goal is to simplify the user experience, eliminate unnecessary steps, and ensure explicit protection of access to the applications. With the central identity provider and integrated apps in place, you are prepared to apply the principles of Zero Trust. Access to the app should undergo explicit verification based on all available data points. Multi-factor authentication should be mandatory for all access, with a preference for Phishing-Resistant MFA. Further, it is essential to assess the health of the device from which the user is accessing the system.
Identify and protect your business-critical assets
Eventually, the main focus is on protecting the data. The protection revolves around controlling access to resources containing sensitive data. In this context, applying Zero Trust principles to the data pillar involves a four-step process. First and foremost, know your data. Once you know your data, you can start applying Zero Trust principles—verifying explicitly and employing least privileged access to apply controls and protect the data. Additional measures involve applying controls to prevent data loss and exfiltration. Finally, you can constantly monitor and govern your data using the principle of assume breach.
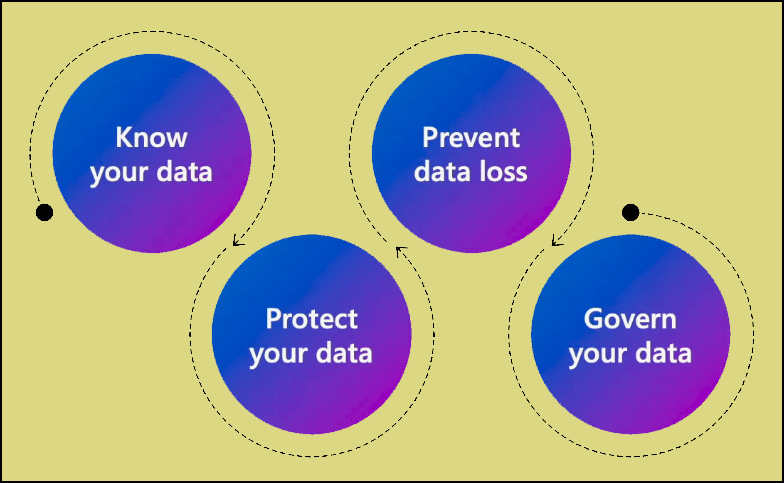
Know your data
Before taking any action, it is necessary to understand where your data is located, spanning your entire digital estate and hybrid, multi-cloud environment. Manual efforts are not scalable for this task and require an automated tool capable of scanning all data sources, including Microsoft and non-Microsoft apps like Hive Metastore, SAP, and Oracle. Once the data has been scanned, a data map is generated, illustrating sensitive information types within the organization and the specific locations and applications where the data resides. With this understanding, the following steps involve scoping the problem and formulating strategies for the deployment.
Protect your data
Users can manually classify data while creating content, although it is not essential to rely only on this approach. Implementing data protection tools allows for automatic labeling based on predefined rules and machine learning. Access policies can be enforced, particularly for more sensitive data, such as requiring Phishing-Resistant MFA for highly confidential data.
Prevent data leak
To mitigate the risk of data leaks, it is necessary to set up policies that prevent oversharing, ensuring users do not share data with unintended audiences. Also, access restrictions should be implemented, such as prohibiting data downloads on unmanaged devices or blocking actions like printing, downloading, and copy-pasting under specific conditions if the user account is risky.
Govern your data
Using the principles of assume breach, it is possible to constant monitoring and refining of controls. This involves monitoring for potential gaps in security coverage, verifying that any new sensitive data remains within the scope of established controls, investigating instances where data exfiltration is suspected, and quickly addressing any unexpected data sharing through early detection.
Build confidence in security posture and programs
Adopting a modern security strategy like Zero Trust provides visibility across various endpoints, including corporate-managed devices, personal devices, and unidentified IoT devices accessing corporate resources. Incorporating access decisions for these endpoints involves a risk assessment and automated detection response actions triggered by alerts from any endpoint. This approach enables comprehensive security monitoring, risk-based access controls, and policies throughout the security infrastructure. The goal is to prioritize real-time protection of critical assets and data in a dynamic threat environment.
Optimize and re-optimize
Utilizing assessment tools such as Microsoft Secure Score and Microsoft Purview Compliance Manager allows you to measure the security posture of your assets, spanning identities, devices, apps, and data. These tools measure your security standing against industry benchmarks and best practices, helping in risk reduction related to data protection and regulatory standards. Continuous monitoring of your Secure Score provides insights into current risk levels and vulnerable assets. This measurable data can be included in regular reporting and security KPIs, enabling you to demonstrate progress.
Posture is all about prevention.
Enhancing your security posture is a proactive measure to prevent high-risk scenarios and vulnerabilities. It is important to observe and monitor your assets across various attack vectors continuously. Detecting potential and actual leaks, as well as identifying pressure points that pose threats to the flow of sensitive data, is essential. By analyzing these observations and patterns, you can effectively derive insights into risks and reduce the likelihood of a significant breach. Through continuous analytics and tracking, you can determine the right level of access controls in real-time, striking a balance between user experience and proper governance. The analysis of security signals evaluates your security culture and identifies areas for improvement.
Security team morale
Enhance your security team's confidence by improving your security posture. A Zero Trust approach empowers your security team to streamline their cybersecurity strategy and retire unnecessary legacy solutions.
More details: aka.ms/zerotrust/
Reference:
Microsoft Ignite Sessions



