Passkeys
Online authentication commonly relies on passwords, but they pose significant challenges. Passwords are hard to remember, easy to forget, and easy to exploit by malicious entities, exposing individuals to potential attacks. Microsoft has launched a strategic initiative to eliminate passwords, aiming to improve online security and convenience for users across the digital landscape. As part of this vision, passkeys represent the next phase in the journey towards a passwordless future, serving as the alternative to passwords.
Microsoft's passwordless journey started in 2015 with the introduction of Windows Hello for consumers and Windows Hello for Business for enterprises. At that time, username and password attacks exceeded 10 million per day. This figure has since risen steadily and currently stands at over 4,000 password attacks per second, totaling more than 300 million daily. In 2019, Microsoft adopted the API standards developed by the W3C, enabling web authentication or WebAuthn for Windows Hello. For those familiar with the concept, this transforms Windows Hello and Windows Hello for Business into a passkey.
Passkey basics
In 2022, Microsoft partnered with the FIDO Alliance, Apple, and Google to endorse passkeys, confirming their commitment to advancing passwordless solutions. This collaborative effort with the FIDO Alliance and the W3C resulted in the creation of FIDO2 WebAuthn standards. These standards leverage public key cryptography to authenticate users, eliminating the need to transmit passwords over the Internet. Instead, your device generates a pair of keys – a private key securely stored on your device and a public key registered with the respective website or application. To sign in, your device needs to prove possession of the private key by signing a challenge from the website or application. The website or application then verifies the signature using the stored public key and grants access. In Windows, the private key is securely stored within Windows Hello. This process is more secure than traditional passwords because the private key never leaves your device, protecting it from potential theft by hackers or phishing attacks. The objective is to leverage the hardware-supported biometrics of your device, such as facial recognition, fingerprint reader, or device PIN, to unlock it and speed up the sign-in process, offering a more convenient alternative to typing a password.
Passkeys serve as a robust defense against identity theft, protecting you from hackers and phishing attacks. By eliminating the need to remember or reset passwords, they save time and the inconvenience associated with traditional authentication methods. Furthermore, passkeys enable quicker and more straightforward access to your apps and services through the biometrics on your device, granting you more control and privacy over your online accounts.
Security benefits of passkeys
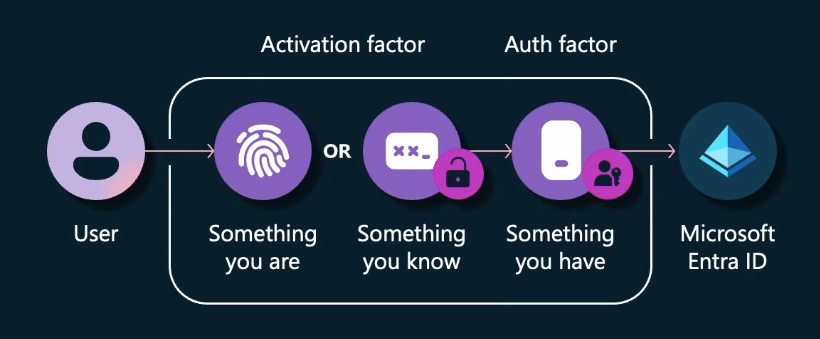
Multi-factor authentication
Passkeys are inherently multi-factor authentication (MFA) tools. To authenticate using a passkey, users must provide a combination of something they have, something they are, or something they know. The user's device, which holds the passkey, represents something they have. To sign in with the passkey, users must use their biometrics (something they are) or a device PIN (something they know). This combination forms the basis of a secure multi-factor authentication system, eliminating the need to combine vulnerable legacy sign-in methods like passwords with SMS to achieve MFA.
Protect users from phishing attacks
Bad actors persistently attempt to deceive users into entering their passwords on malicious websites and fatiguing them into approving foreign MFA requests. Microsoft issues alerts for an alarming monthly number of around 10,000 password entries on malicious websites. Also, they detect approximately 6,000 instances of MFA fatigue attempts per day. It's crucial to have strong protection measures in place to keep your users' accounts secure.
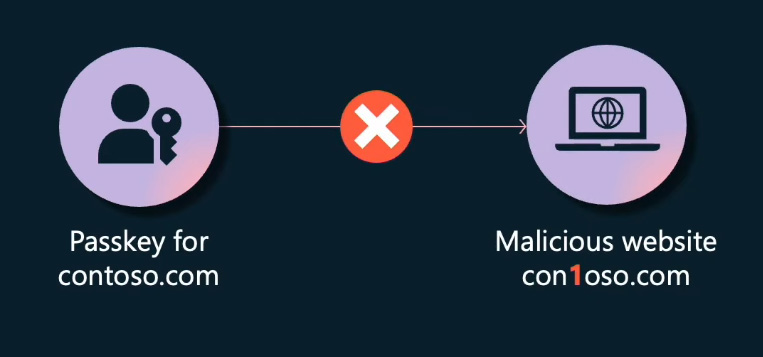
Imagine a malicious website, contoso.com, where the letter 't' is replaced with the digit '1,' aiming to gather credentials from unsuspecting users seeking to sign in to the legitimate contoso.com. Although a user might be misled into visiting this visually similar site, the crucial point is that they cannot be deceived into providing their passkey to this malicious website. The user's device prevents such actions. When a passkey is generated, it is only linked to the trusted domain of the registered website. A passkey created for contoso.com can only be used on contoso.com.
Cross-device authentication
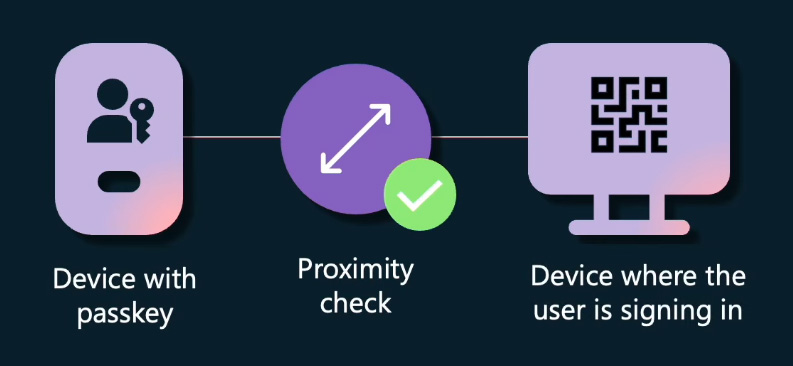
Users remain protected from phishing attacks during cross-device authentication, which occurs when a passkey from one device is used to sign in to another. Suppose a user wants to sign in on a new device and link two devices for cross-device authentication. In this scenario, the user is prompted to scan a QR code generated on the target device where they intend to sign in. Throughout this process, a proximity check is conducted, ensuring that the passkey is only used for authentication on a linked device nearby. Users can trust that this technology ensures their passkey remains secure, preventing any misuse by a malicious actor attempting unauthorized access from a remote location.
What organizations should consider when deploying passkeys?
The term passkey technically references the FIDO2 credential, which can be stored on various devices, including security keys, computers, and mobile phones. Some passkeys can sync across devices. This feature ensures that if a user loses their phone, they will not lose their passkey, as it is backed up. While syncing offers excellent availability and recoverability, it also comes with some considerations for organizations. Synced passkeys can be backed up to Clouds associated with consumer identities, where there are limited administrative controls for governance. As passkeys sync across devices, it becomes challenging to understand the properties of the user's device, given that these properties may change over time. Users can share sync passkeys with family, friends, and others, offering convenience for shared accounts. However, this sharing functionality might not be suitable for work or school accounts. Passkeys can be device-bound, indicating that the passkey remains confined to the device where it was initially created. Passkeys are device-bound when they are stored as FIDO2 security keys, as well as Windows Hello for Business. These options are already supported in Microsoft Entra ID today.
Create a passkey with Windows Hello
Creating and storing a passkey on Windows is a straightforward process. With the Windows native platform authenticator, Windows Hello, users can conveniently save their passkey. When logging into or creating a web or application-based account on your Windows device, you need to follow the instructions provided by the relying party to save the passkey on your device. Once the private key is generated, Windows Hello will authenticate your identity through a biometric or PIN challenge and store it within the Windows Hello container, backed by isolated hardware in the TPM. When returning to the website or application to log in, you will not be prompted for a username or password. Instead, you can use your passkey within Windows Hello to sign in.
Managing passkeys
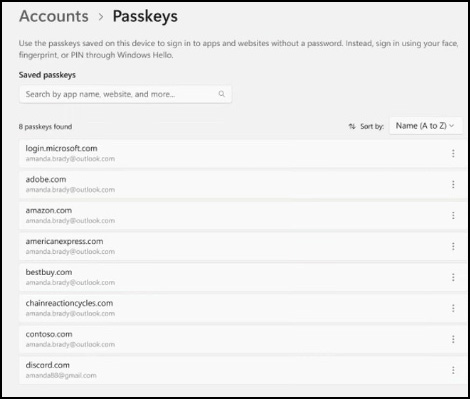
Microsoft has streamlined the process for users to view and manage their passkeys. To do so, go to Windows Settings, proceed to accounts, sign-in options, and passkeys. Windows will list all your passkeys, allowing you to review and manage them. In this section, you can remove and delete any passkey that you no longer wish to have associated with your Windows device.
Beyond making passkeys compatible with Windows and integrating them into Windows Hello, Microsoft has introduced cross-device authentication. This means you can now use a passkey stored on another mobile device, such as your tablet or phone, to authenticate a web or application session on your Windows device. Imagine you are planning a trip on your phone. While using a travel app, you are prompted to set up a passkey for that specific app and account. Following the provided steps, you successfully create a passkey on your phone. As you browse and find a suitable plane ticket, you decide to switch to your Windows 11 PC to complete the transaction and payment instead of doing it on your phone. You save the trip details under your profile on the app. Now, sitting at your Windows 11 PC, you navigate to the same travel website and proceed to log in. Instead of entering your username and password on your Windows 11 PC, you prompt with a QR code. Using your phone, you can scan the QR code to confirm your presence or proximity to the device initiating this new session. Your phone recognizes the QR code, receives information from your PC, and prompts you for biometric identification. Upon completing the biometric challenge on your phone, it sends a notification to the relying party over the Internet, granting you access to the website on your PC. Now, you can proceed with your transaction and embark on that dream vacation you have always wanted.
Passkeys for the developers
Passkeys on Windows are not exclusive to consumers. Developers, for instance, frequently use GitHub as a repository for their code. GitHub, being a relying party, has enabled passkeys for its users. In enterprise settings, users often maintain distinct GitHub accounts separate from their enterprise login.
Microsoft Authenticator app
Mobile phones have become integral in our daily lives, and the Microsoft Authenticator app stands out as a premier authentication credential, offering users the flexibility to authenticate from their mobile devices anywhere they go. This credential undergoes continuous upgrades and improvements to enhance customer protection in an evolving security landscape. Microsoft's flagship credential is evolving towards becoming phishing-resistant to counteract man-in-the-middle attacks. Customers in high-security enterprise settings have provided feedback, emphasizing the need for device-bound, phishing-resistant credentials. The Authenticator app will fulfill this demand by leveraging device-bound passkeys on Android 14 plus and iOS 17 plus devices. By leveraging passkeys, Microsoft aims to provide customers with a free, phishing-resistant credential based on open standards. This ensures users benefit from the latest security enhancements aligning with the FIDO standard.
The phishing-resistant Authenticator app allows admins to enable and restrict passkeys to specific passkey providers and security keys. Admins can leverage conditional access authentication strength policies to mandate that users utilize the Microsoft Authenticator app when accessing specific high-security flows and resources. Any organization seeking a free phishing-resistant credential that offers universal accessibility for users should consider the Microsoft Authenticator as their preferred solution.
Reference:
Microsoft Ignite Sessions




